Server Hardening
INTRODUCTION
An insecurely configured Network/OS is giving attackers an easy route into your organization. A quality dry run performed by our analyst to conduct configuration review helps to reduce this risk by identifying misconfiguration aka vulnerabilities across web application servers, web frameworks, firewall configuration, registry, NT authority, wireless devices, etc.
Certbar Network/OS Hardening team has extensive experience of configuration review services to help you identify and address such weaknesses.
PROCESS
Server Security Hardening
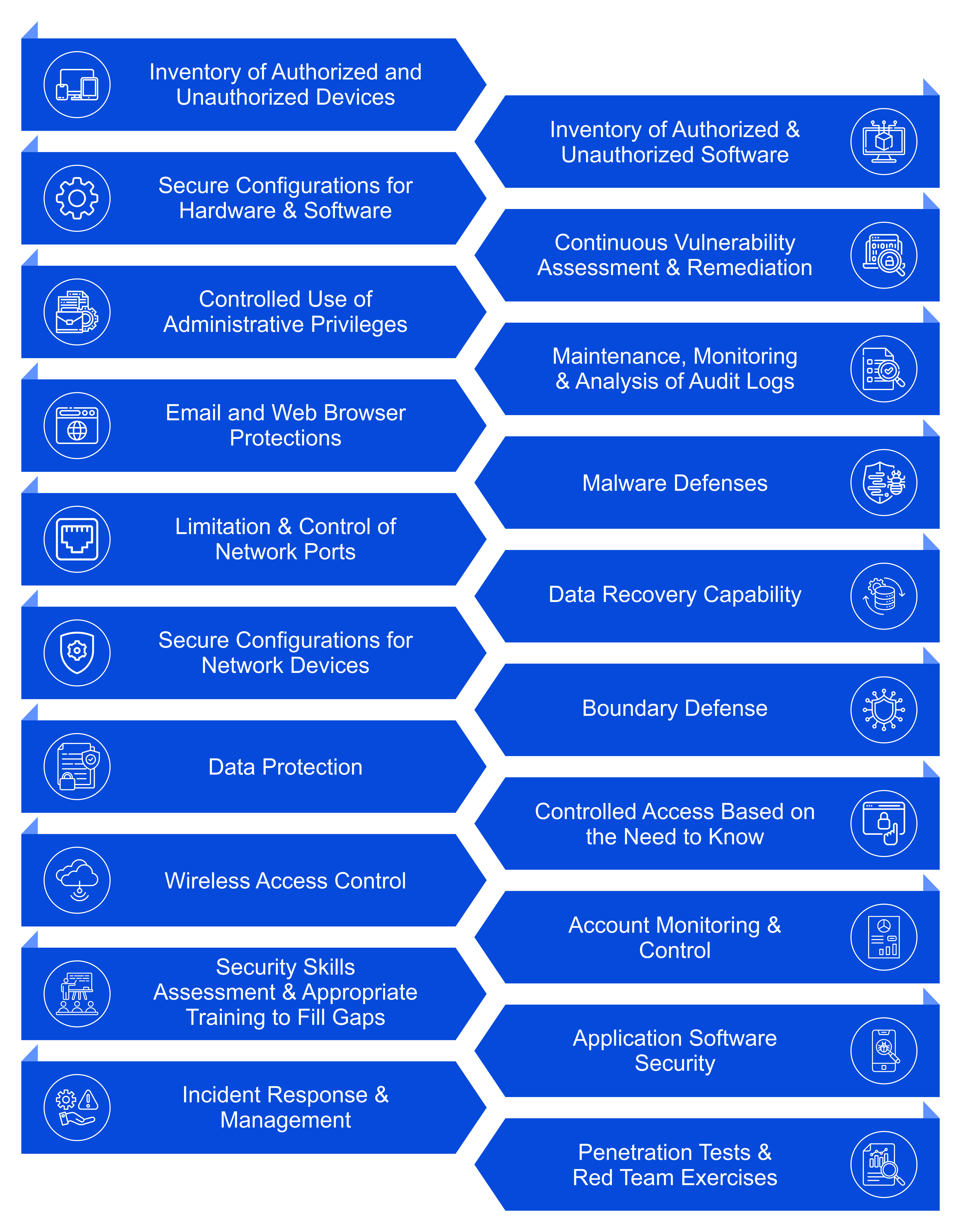
Attackers/Script-kiddies are always looking for “Publicly known vulnerabilities”. Network Hardening is basically a process to keep the environment up-to-date. So, any vulnerability present in the current version can be resolved by the official security patch released by the provider and this can be prevented by applying appropriate policies.
OS Hardening is the process of configuring an OS securely, providing least privilege required, updating it regularly, creating rules and password policies, and removing unnecessary applications, handlers, functionalities and services. This is performed to reduce the exposure of your attack surface from threats and to remediate possible risk factors.
Methodology Checklists
Standard
- Quick Security Scan
- Chkrootkit Scan
- ClamAV Anti-Virus Scan
- CSF IP tables Firewall Review
- Host.conf and sysctl.conf Review
- Securing /tmp, /var/tmp
- PHP Security Configuration Review
- Fixing Misconfiguration
- Memory log Protection
- Removal of Logs, Softwares
- Securing Apache/Nginx
- Rootkit Hunter Scan
- Sysctl Hardening
- MultiTail - Log Monitor
- MySQL optimization
- /shm & /proc hardening
- IfTop
- Brute Force Detection
- Web Server & PHP Hardening
- Vulnerability Scans
- Exploit Scan Service
- Mod_Evasive - DDOS protection
Professional
- Quick Security Scan
- Chkrootkit Scan
- ClamAV Anti-Virus Scan
- CSF IP tables Firewall Review
- Host.conf and sysctl.conf Review
- Securing /tmp, /var/tmp
- PHP Security Configuration Review
- Fixing Misconfiguration
- Memory log Protection
- Removal of Logs, Softwares
- Securing Apache/Nginx
- Rootkit Hunter Scan
- Sysctl Hardening
- MultiTail - Log Monitor
- MySQL optimization
- /shm & /proc hardening
- IfTop
- Brute Force Detection
- Web Server & PHP Hardening
- Vulnerability Scans
- Exploit Scan Service
- Mod_Evasive - DDOS protection
Enterprise
- Quick Security Scan
- Chkrootkit Scan
- ClamAV Anti-Virus Scan
- CSF IP tables Firewall Review
- Host.conf and sysctl.conf Review
- Securing /tmp, /var/tmp
- PHP Security Configuration Review
- Fixing Misconfiguration
- Memory log Protection
- Removal of Logs, Softwares
- Securing Apache/Nginx
- Rootkit Hunter Scan
- Sysctl Hardening
- MultiTail - Log Monitor
- MySQL optimization
- /shm & /proc hardening
- IfTop
- Brute Force Detection
- Web Server & PHP Hardening
- Vulnerability Scans
- Exploit Scan Service
- Mod_Evasive - DDOS protection
Take control of your cyber security, choose our ultimate protection
Experience unbeatable cyber security with Certbar Security
Contact us today to learn more