AWS Penetration Testing
RISK
Amazon Web Services (AWS) is the world’s leading cloud platform used over a million people across 190 countries. It provides elastic computing services, cloud storage, databases, and a range of data analytics and AI applications, as well as deployment and automation services.
AWS has rid its customers of a lot of hardships such as the need for on-premise data warehouses, distributed computing systems, and hardware management but cyber security threats are not among them. A highly effective way of discovering security vulnerabilities in a cloud environment is via penetration testing. A penetration tester can discover critical security weaknesses in an AWS deployment and provide actionable recommendations for remediating them.
Secure your AWS infrastructure!
Frameworks, PaaS, IaaS & SaaS are built in such a way that they are part secure and part customizable to its users/customers. Some things are just not a Plug and Play services.
IS AWS SECURE?
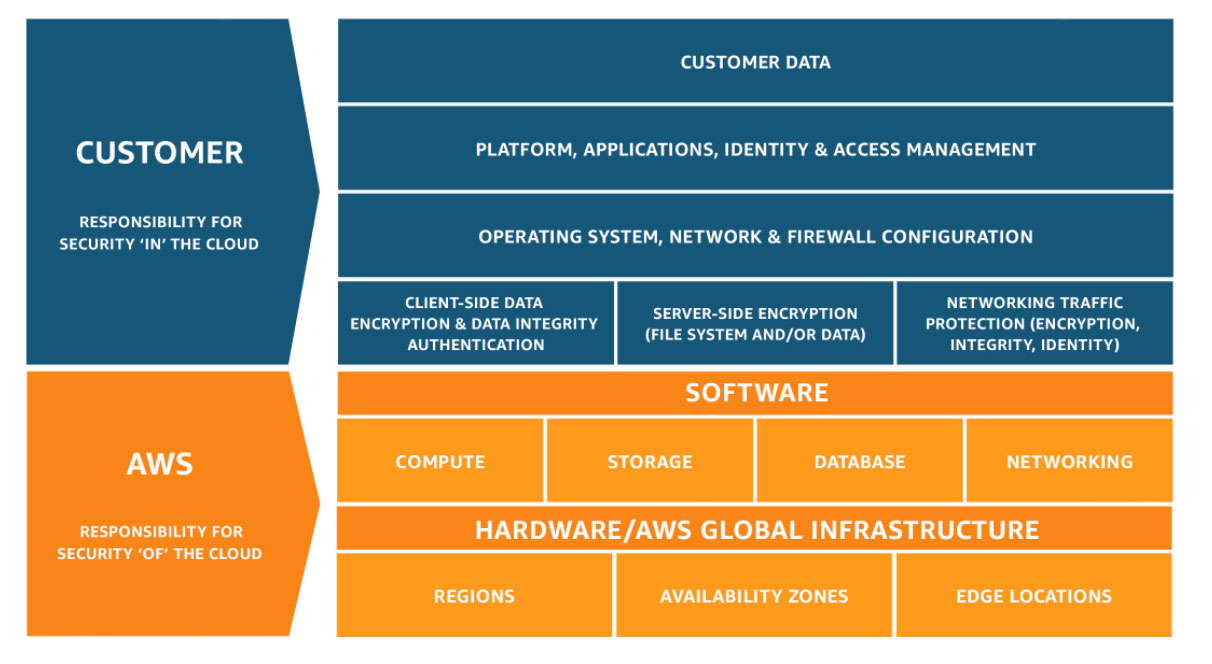
The Shared Responsibility Model
Security testing performed on AWS follows the shared responsibility model. Amazon differentiates between two types of security:
Security of the cloud: This means security of the AWS cloud platform itself, including the cloud platform and all AWS services. Amazon is responsible for securing the cloud platform and regularly tests its cloud with internal or external security engineers. Amazon customers cannot perform penetration testing on this aspect of cloud security.
Security in the cloud: This means the security of resources or assets deployed by an organization on the AWS platform. These are the responsibility of the company or resource owner, who need to ensure applications, assets, and systems are securely configured. In general, organizations may perform penetration testing to verify these aspects of a secure deployment.
Approach & Methodology
Pentesting AWS must focus on user-owned assets, identify & accesses management, user permissions configuration, and use of the AWS API’s that are deeply integrated into the AWS ecosystem. For example, targeting and compromising AWS IAM Keys, Testing S3 bucket configuration and permission flaws, establishing access through Lambda backdoor functions, and covering tracks by obfuscating Cloudtrail logs. These attacker’s strategies are specific to AWS Cloud and require specific knowledge and approach.
Here is the Major Areas to Focus on While Penetration Testing of AWS:

External Infrastructure of Your AWS Cloud

Application(s) You are Hosting/Building on Your Platform (AWS Application Penetration Testing)

Internal Infrastructure of Your AWS Cloud

AWS Configuration Review

AWS Infrastructure Scoping

AWS Service Identification & Mapping

AWS Reconnaissance & Enumeration

AWS Hosted App's Vulnerability Identification & Analysis

Targeting & Compromising AWS IAM Keys

EC2 instance & Application Exploitation

Testing S3 Bucket Configuration & Permissions Flaws

Lambda Backdoor Functions
Take control of your cyber security, choose our ultimate protection
Experience unbeatable cyber security with Certbar Security
Contact us today to learn more