Kubernetes Penetration Testing
INTRODUCTION
Kubernetes is one of the fastest-growing projects in the history of open-source enhances a significant part of many organisations’ compute stack. The versatility and scalability of containers and pods inspire many developers to advance their MVC / Microservices workload to Kubernetes. While Kubernetes has many benefits, it also brings new unknown security challenges to life. Consequently, it is imperative to agree on the numerous security uncertainties that subsist in containerised environments, and especially in Kubernetes.
Certbar’s comprehends Kubernetes & its utilization and has hands-on practical experience in Kubernetes Penetration Testing.
Our Approach & Methodology
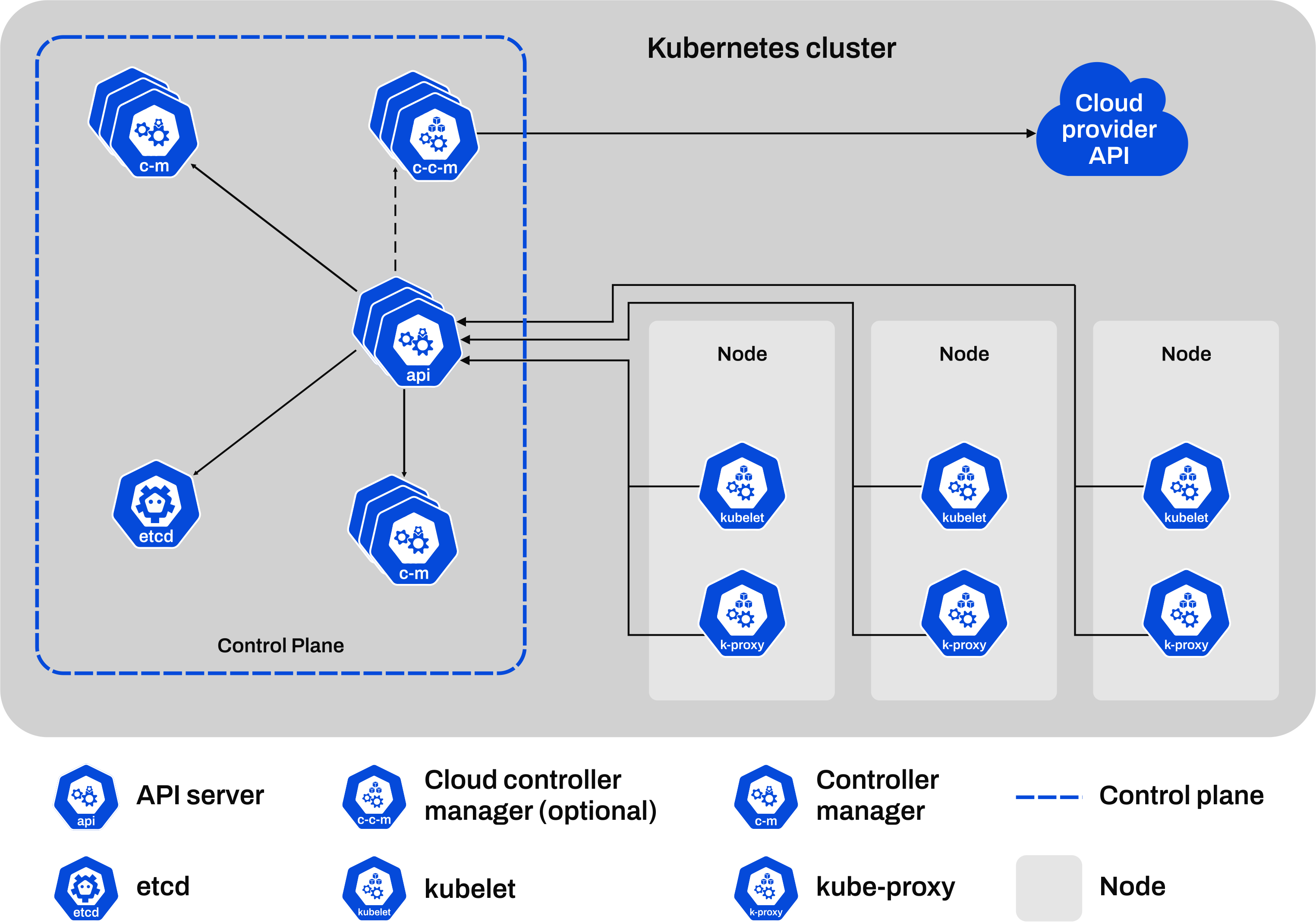
Top Runtime Vulnerabilities of Kubernetes Security
We covered two examples of risky misconfigurations that can be abused by attackers. The most commonly identified misconfigurations while pentesting kubernetes are:
Framework assaults: During runtime, Kubernetes foundation components including the etcd, API server, and regulators all present their own assault surfaces.
Intricacy: The progressing well-being of a Kubernetes cluster has many moving parts. Containers that are compromised should be immediately disconnected, halted, and supplanted with solid ones while the wellspring of the assault is found and remediated.
Test Cases
Pod Enumeration
API Misconfigurations
Cryptography Issues
Secrets Management
RBAC Misconfiguration
Multi-tenancy Isolation
Report
Fix Verification
Take control of your cyber security, choose our ultimate protection
Experience unbeatable cyber security with Certbar Security
Contact us today to learn more