Smali Code Analysis for Android Hacking

Part 1
What is Smali Code?
Smali is a low-level programming language used to create, edit and analyze Android application bytecode. It serves as an intermediate representation of Android application functionality and is human-readable, though more complex than high-level languages such as Java or Kotlin.
JVM, JDK, JRE, and DVM are all related to Java or Android development, but they serve different purposes. Here’s an explanation of each:
JVM (Java Virtual Machine)
- A JVM is a virtual machine that enables a computer to run Java programs.
- It interprets Java bytecode and executes the instructions on the underlying hardware.
- JVM abstracts the underlying hardware and operating system, providing platform independence for Java applications.
DVM (Dalvik Virtual Machine)
- DVM was the original virtual machine used in Android devices to execute Android application bytecode (Dalvik bytecode).
- It was designed specifically for mobile devices with limited resources.
- DVM used a register-based architecture and supported optimizations such as just-in-time (JIT) and ahead-of-time (AOT) compilation.
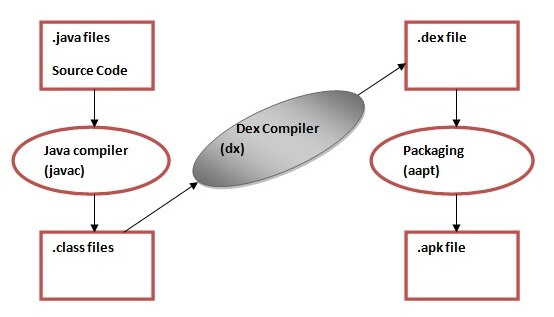
https://www.javatpoint.com/dalvik-virtual-machine
Purpose of Smali
Smali is primarily used to manipulate Android application bytecode, which is run by Dalvik Virtual Machine (DVM) or Android Runtime (ART).
It allows developers and researchers to understand, modify and analyze Android applications at a low level, often used in reverse engineering tasks.
Syntax and Structure
- Smali syntax resembles assembly language and is composed of mnemonic instructions and directives.
- Instructions represent bytecode operations such as method invocation, variable manipulation, control flow, and exception handling.
- Registers (e.g., v0, v1) are used to store data during method execution.
1. Registers
Smali code uses registers (eg, “v0,” “v1”) to store and manipulate data during Android app execution. This register is denoted by the prefix “v” followed by a number and can be compared to a variable in other programming languages.
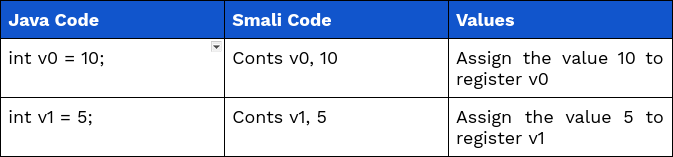
Example:
Smali, control statements are used to change the flow of execution in a method. Common control statements include branching, conditionals, and loops. Here are examples of various control statements in Smali:
2. Smali Instructions
2.1 conditional branches
Smali, conditional branches are used to control the flow of execution based on conditions. Here’s an example of Smali code demonstrating conditional branching:
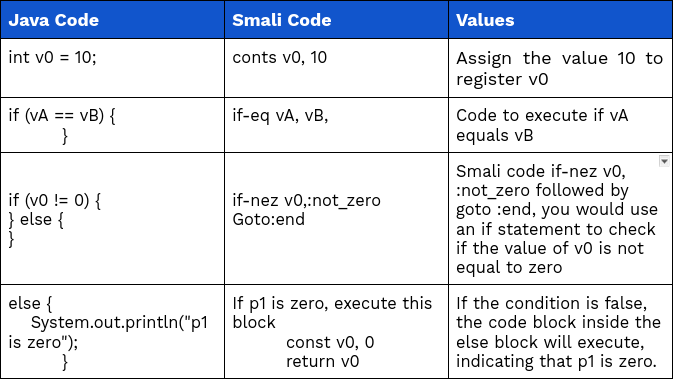
2.2 Return
Smali, the return instruction is used to return control from a method. Here’s an example of Smali code demonstrating the use of the return instruction.
3. Smali Labels
In Smali, labels are markers within the code that serve to indicate specific points or addresses. They are essential for controlling the flow of execution, particularly in conditional statements, loops, and branch instructions.
Example 1: Smali code
Example : Java code
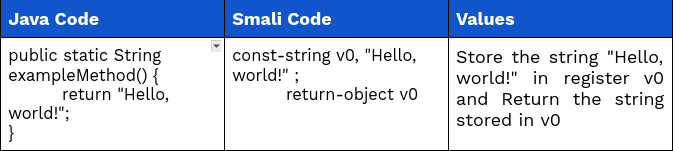
4. Smali Method and Field References
In Smali code, method and field references are used to interact with methods and fields of classes within the bytecode and method reference specifies the class name, method name, and method signature.
Example: Smali code
Example: Java code
Finally ,
How to Root Detection Bypass in Smali code
Conditional statements
To implement a simple root detection bypass logic in Smali, you can use conditional statements to check if specific indicators of root access are present. If these indicators are detected, you can bypass the root detection mechanism. Here’s a basic example:
Example: Smali Code
Example: Java Code
Boolean values
In Smali code, 0x0 and 0x1 are often used to represent boolean values, where 0x0 typically stands for false and 0x1 stands for true. You can use these values to implement root detection bypass logic. Here’s a simple
Example: Smali Code
Example: Java Code
How to Authentication bypass
simple Smali code logic for authentication bypass with input validation, returning boolean values 0x0 and 0x1 (equivalent to false and true in Java):
Example: Smali Code
Example: Java Code
Securing Smali code involves protecting the sensitive logic, resources, and data within your Android application. Here are some general practices to help secure your Smali code:
Remediation:
- Obfuscation: Use obfuscation tools like ProGuard to rename classes, methods, and variables in your Smali code. This makes it difficult for reverse engineers to understand your code.
- Encryption: Encrypt sensitive data such as API keys, cryptographic keys, or other secrets before embedding them in your Smali code. Use encryption libraries available in Java to encrypt and decrypt data at runtime.
- Avoid Hardcoding Sensitive Data: Avoid hardcoding sensitive data directly into your Smali code. Instead, consider storing sensitive information in secure storage locations like Shared Preferences or encrypted databases.
- Secure Network Communications: Ensure that your app communicates securely over the network by using HTTPS for web requests and implementing proper SSL/TLS configurations.
- Permissions: Review and reduce the permissions requested by your application. Request only those permissions that are necessary for the functionality of your application.
- Input Validation: Validate all user inputs to prevent common security vulnerabilities such as injection attacks, buffer overflows, or SQL injection.
- Secure Code Review: Perform regular security code reviews to identify and address potential security vulnerabilities in your Smali code.
- Use ProGuard Rules: Configure ProGuard to optimize and obfuscate your code further. Write specific rules to keep certain classes, methods, or fields unchanged if necessary.
- Keep Libraries Updated: Ensure that you’re using the latest versions of libraries and dependencies in your project to benefit from security patches and updates.
- User Authentication and Authorization: User authentication and authorization: Implement secure user authentication and authorization mechanisms to control access to sensitive features or data in your application.
- Secure File Storage: Store sensitive files securely using appropriate file permissions and encryption techniques.
- Code Signing: Sign your APK files with a digital certificate to ensure the integrity and authenticity of your application.
That’s all for this blog, I hope you enjoyed reading this and the next blog start hands-son part 2 Reverse Engineering APK an Android app