Wireless Warfare: Evil Twin vs Rogue Access Points

Table of Contents
Ever connected to what you thought was a safe Wi-Fi network, only to realize it’s a trap? It’s a world of evil twins and rogue access points. Imagine being in a cafe, eager to connect to “Free Cafe Wi-Fi,” only to find out it’s not what it seems. Or stumbling upon a mysterious Wi-Fi router at work or in public, secretly stealing your data. These digital imposters are everywhere, waiting to rescue you.
What is Evil Twin Attack ?
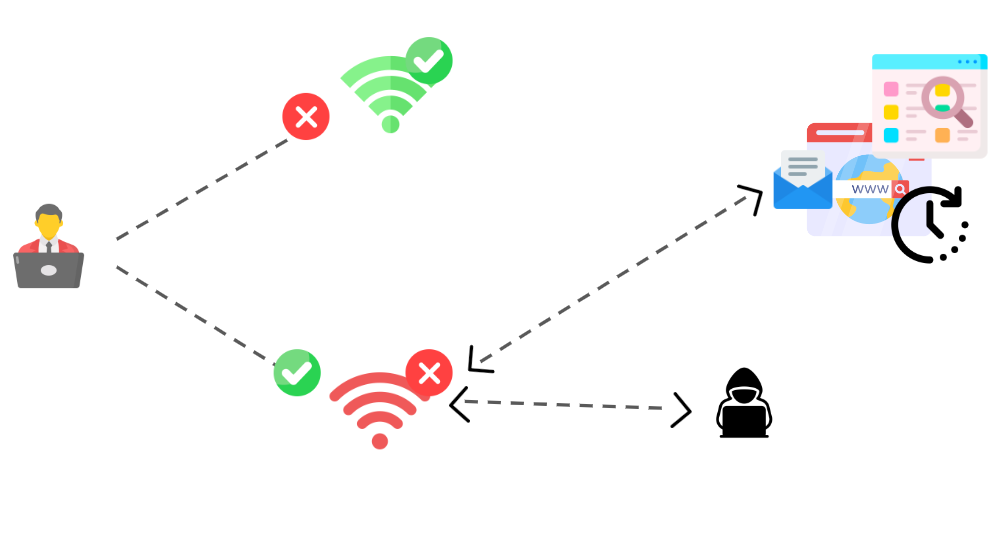
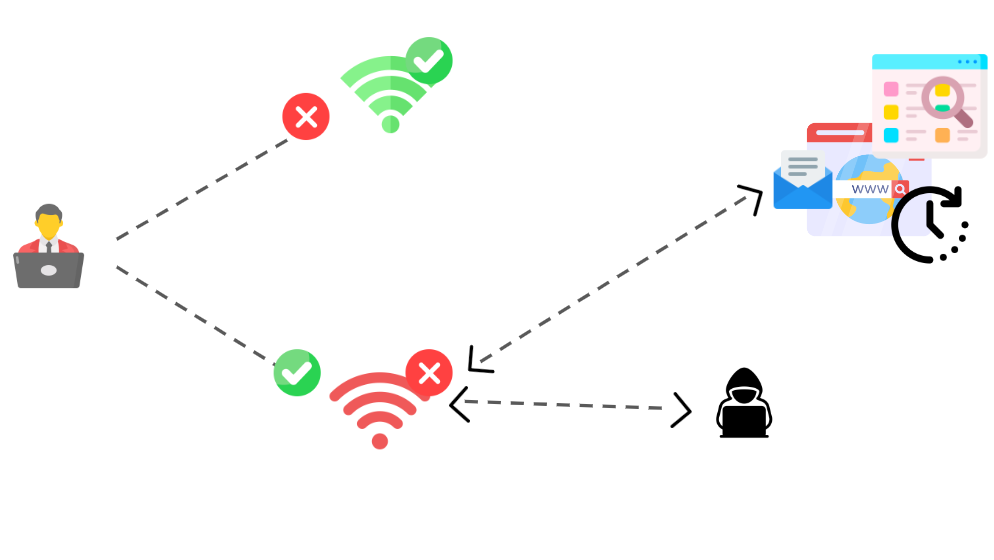
An evil twin attack occurs when a hacker installs a phony wireless access point in the hopes that users will connect to it rather than the real one. All data that users exchange with the network when they connect to this access point passes through a server under the control of the attacker. With a smartphone or other internet-capable gadget, some easily accessible software, and an attacker, it is possible to construct an evil twin. Evil twin attacks are more prevalent on unsecured public Wi-Fi networks, where your personal information is at risk.
Why are evil twin attacks so dangerous?
Evil twin attacks are dangerous because when they succeed they provide hackers with access to your device. This means that, if a user performs financial activities while using the evil twin Wi-Fi, they will be able to obtain login credentials and other confidential information. Furthermore, the hackers might infect your device with malware.
Evil twin Wi-Fi attacks often don’t leave behind telltale signs that might reveal their true intentions. Many victims won’t challenge them when they carry out their main duty of giving victims access to the internet. Users might become aware that they have been the victim of an evil twin assault only after discovering that someone else has taken unwanted acts on their behalf.
Example Of Evil Twin Attack
Someone chooses to go to their neighborhood coffee shop. After taking a seat and enjoying their coffee, they join the public Wi-Fi network. They have no reason to be suspicious because they have connected to this access point before without any issues. This time, though, a hacker has created a malicious network with the same SSID name. Their imaginary network is stronger than the real network of coffee shops because they are sitting closer to the gullible target. As a result, despite it being marked as “Unsecure,” the target connects to it.
After going online, the target pays their coffee charge by logging into their bank account. Hackers are able to access their banking information through the evil twin network as they are not utilising a VPN, or virtual private network, which would encrypt their traffic. It is only after they discover that there have been unlawful transactions made on their account, costing them money, that the victim realizes this.
How to protect yourself against Evil Twin Attacks
- Steer clear of unidentified or insecure Wi-Fi networks.
- Check with the network owner or use secure authentication techniques to confirm the legitimacy of the network.
- To encrypt your data and safeguard your privacy when using public Wi-Fi networks, use a virtual private network (VPN).
- Update the Wi-Fi network hardware and your devices with the most recent security fixes.
By using these preventive measures you can reduce your vulnerability to malicious two attacks and maintain the security of your online activity and data.
What is Rogue Access Point ?
To begin with, what is an access point? While access points connect to the Internet via a wired connection but share it wirelessly with many devices like your computer.
If you’re wondering why you’ve heard of routers but not access points, it’s because access points are usually included with routers. Routers are responsible for transporting packets, not for providing wireless Internet access.
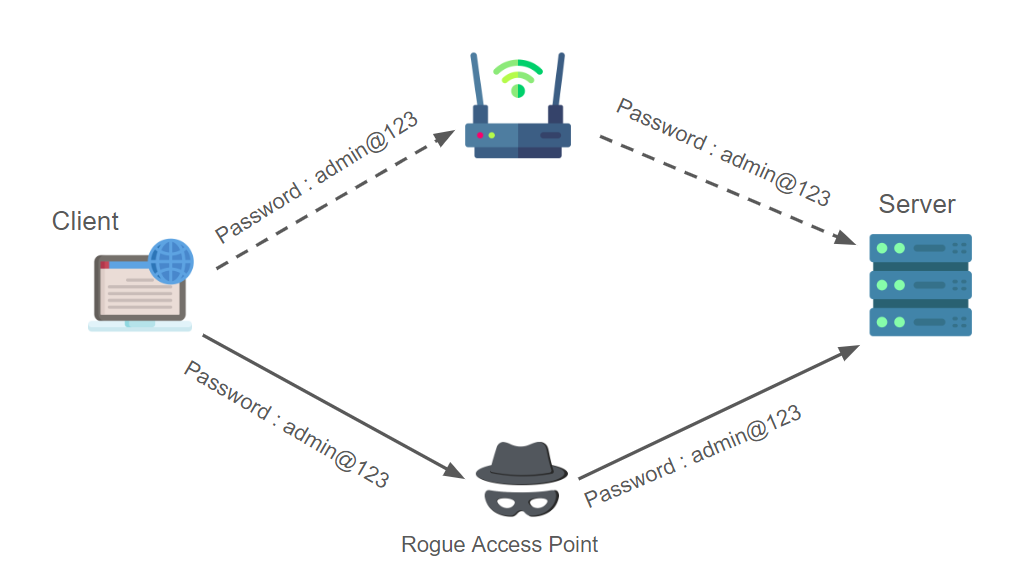
Any wireless access point that is placed on a network’s wired infrastructure without the permission of the administrator or owner and allows illegal wireless access to the network’s wired infrastructure is known as a rogue access point or rogue AP.
Why are rogue access points so dangerous?
A rogue access point provides unauthorized access to your network. They can be set by employees, visitors, or malicious actors without the knowledge or consent of the network administrator. This unauthorized access can lead to data breaches, theft of sensitive information and other security incidents.
Organizations operating in regulated industries, such as healthcare, finance, or government, face heightened regulatory compliance risks associated with rogue access points. Regulatory frameworks such as HIPAA, PCI DSS and GDPR impose strict requirements to protect sensitive data and maintain the integrity of network infrastructure. Failure to adequately address rogue access points can lead to compliance violations and regulatory penalties.
Example Of Rogue Access Point Attack
When we think of corporate networks, a corporate WLAN is an authorized and secure wireless portal to network resources. A rogue access device (AP) is any WLAN radio that is connected to a corporate network (often to some network switch) without authorization.
The majority of rogue access points that are installed by staff members—either intentionally or unintentionally—are actually Small-office home-office (SOHO) wireless routers, which are the same routers you most likely have at home. These are not the same APs that the organization’s IT department uses. When they are improperly configured or set up without any security, it creates another point of attack where someone can easily gain access to a highly secured network.
Given how the IT sector is now developing, rogue access points may be incredibly difficult to locate and effectively camouflaged. If the Raspberry Pi connected to your network switch was located in the back of the rack and hidden among hundreds of network wires, would you be able to quickly identify it? I’m positive you wouldn’t see it at all!
Rogue Access point vs Evil Twin – what’s the difference?
- An unauthorized access point that is connected to a network in order to provide a backdoor from the outside into the official network is known as a rogue access point.
- An evil twin, on the other hand, is a duplicate of a genuine access point. Its goal is a little different: it attempts to trick gullible people into joining to the fictitious network in order to steal data.
- We discussed how rogue access points are typically installed for convenience and are not always malevolent. The users’ inexperience when they set them up is what makes them dangerous. Evil twins, on the other hand, intentionally set up to look like a genuine access point and actively attempt to fool users.
While they are not identical, the evil twin is considered a form of rogue access point.
Now that this blog post has come to a conclusion, keep in mind that awareness is your best defense against the hidden dangers of the evil twin and rogue access points. Remain alert, educated, and cautious when navigating the internet world. Let’s work together to make the internet a safer place for everyone. Visit us for more information of certbar.