Cloud Security Essentials: Avoiding AWS Misconfigurations
Lata Parmar
Oct 18, 2024
•
11 Min
Lata Parmar
Oct 18, 2024
•
11 Min
TABLE OF CONTENTS
Share
As organizations increasingly move their infrastructure to the cloud, AWS has become the go-to solution for businesses of all sizes. It offers powerful tools for storage, computing, and networking, enabling companies to scale seamlessly. But with this flexibility comes responsibility — and that’s where misconfigurations become a serious risk.
Misconfigurations often occur when users overlook security settings, enable broader access than necessary, or misunderstand the purpose of certain AWS services.
Misconfigurations in AWS environments often arise from a combination of factors:
Before diving into specific misconfigurations, it’s crucial to understand the AWS Shared Responsibility Model. In AWS, security is a shared responsibility between AWS and the customer:
Customer Responsibilities: Customers are responsible for securing everything in the cloud. This includes configuring services correctly, managing data security, setting permissions, and ensuring compliance.
IaaS-Infrastructure as Service | PaaS-Platform as Service | SaaS-Software as Service |
User Access Identity | User Access Identity | User Access Identity |
Data | Data | Data |
Application | Application | Application |
Operating System | Operating System | Operating System |
Virtualization | Virtualization | Virtualization |
Network | Network | Network |
Infrastructure | Infrastructure | Infrastructure |
Physical | Physical | Physical |
Cloud Client / Customer security responsibility
Cloud Provider security responsibility
Understanding these common risks is essential for organizations to safeguard their data and ensure compliance
Overview: Amazon Simple Storage Service (S3) is a scalable object storage service designed for data backup, archival, and analytics. It allows users to store and retrieve any amount of data from anywhere on the web.
Common Misconfiguration: Misconfigured S3 buckets are a frequent security concern. For instance, public access permissions can expose sensitive data. A common scenario involves using wildcard permissions, allowing users to perform actions they shouldn’t have access to.
Example:
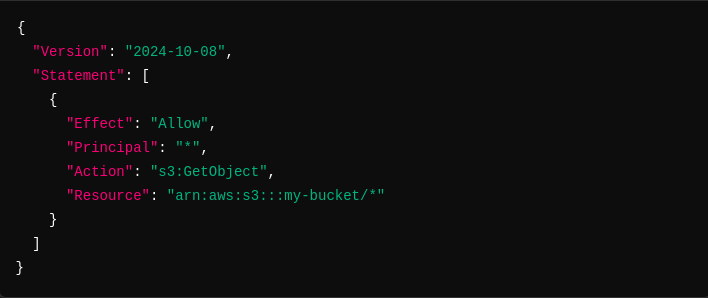
In the above policy, the wildcard * in the Principal field allows anyone on the internet to read objects in the my-bucket S3 bucket. Such misconfigurations can lead to data breaches, exposing sensitive information to unauthorized users.
Overview: AWS IAM is responsible for managing access to AWS services and resources. It enables you to create and manage users, roles, and policies securely.
Common Misconfiguration: One of the most dangerous IAM misconfigurations is the use of overly permissive policies, which can allow users or roles to perform unauthorized actions.
Excessive Permissions: Roles or users are often assigned blanket permissions like s3:* or ec2:*, granting them full access to all actions for that service. This lack of restriction enables users to perform unauthorized operations, such as modifying, deleting, or viewing sensitive data, making system-wide changes, or even shutting down critical infrastructure. This broad level of access can lead to accidental misconfigurations, privilege abuse, or easier paths for attackers to exploit the environment.
Forgotten or Unused Access Keys: Over time, IAM users may accumulate access keys that are no longer needed but are still active. If these keys aren’t regularly rotated or deactivated, they become a major security risk. If an attacker gains access to one of these old keys—via phishing attacks, malware, or even human error—they can use the key to access the AWS environment, bypass security controls, and perform malicious activities such as data exfiltration, modification of sensitive resources, or unauthorized infrastructure changes.
Example:

In this policy, the wildcard (*) in both the Action and Resource fields allows the IAM entity to perform any action on any resource. This is extremely risky and can lead to privilege escalation or unauthorized data access.
Enforce the Principle of Least Privilege: Only grant the specific permissions needed for each role or user. Instead of s3:*, limit access to necessary actions like s3:GetObject or s3:PutObject. Always define fine-grained permissions to minimize potential security risks.
Use IAM Access Analyzer: AWS’s IAM Access Analyzer helps you detect and identify overly permissive policies. This tool provides recommendations to restrict access based on the principle of least privilege.
Rotate and Remove Unused Access Keys: Regularly rotate access keys (every 90 days, for example) and immediately deactivate or delete any unused keys to reduce exposure risk. AWS IAM Credential Reports can help track which users have active keys and how long they've been in use.
Enable Multi-Factor Authentication (MFA): For privileged users, enforce MFA to add an extra layer of protection.
Overview: Amazon EC2 provides scalable virtual servers (instances) to run applications in the cloud. These instances are flexible and powerful, but they are only as secure as the configurations you apply to them. A common security risk involves how access is controlled to these instances via Security Groups.
What are Security Groups?
Security Groups in AWS act like virtual firewalls for your EC2 instances. They define which inbound and outbound traffic is allowed to and from your instance. Security Groups are crucial for controlling access to your EC2 instances and other AWS resources. The rules can be set based on IP ranges, protocols, and ports.
Common Misconfiguration:
1.Open Ports in Security Groups Security groups manage inbound and outbound traffic for EC2 instances. Leaving unnecessary ports open can pose serious security risks.
2.Public IP Addresses for Private Instances Instances that don’t need public internet access are sometimes mistakenly assigned public IP addresses.
3.Outdated or Insecure AMIs Using outdated Amazon Machine Images (AMIs) can expose instances to known vulnerabilities.
4.Weak Authentication for SSH or RDP Access to EC2 instances often occurs via SSH or RDP, and weak authentication methods can be exploited.
Example:
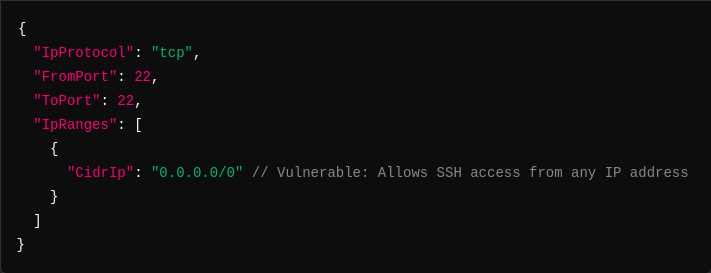
Change "CidrIp": "0.0.0.0/0" to a specific IP range, such as "CidrIp": "203.0.113.0/32 (example)", to restrict access to your office’s IP or a specific VPN range. This approach enhances security by limiting who can connect to your EC2 instance, thus reducing the risk of unauthorized access.
Use More Restrictive CIDR Blocks in Security Groups:
Rotate SSH Keys Regularly:
Implement AWS Systems Manager:
Monitor Access with AWS CloudTrail:
Overview :AWS Cognito is a service that enables you to add user sign-up, sign-in, and access control to your web and mobile applications easily. It supports both authentication (verifying user identities) and authorization (controlling what resources users can access).
Cognito provides two main features:
Cognito User Pools: A managed user directory that allows you to create and manage users, handle user authentication, and implement advanced security features like multi-factor authentication (MFA).
Cognito Identity Pools: Provides temporary AWS credentials to allow users to access AWS resources such as S3 or DynamoDB. It supports both authenticated and unauthenticated (guest) access.
Cognito also supports identity federation, allowing users to sign in with external identity providers like Google, Facebook, Apple, or enterprise systems using SAML.
Misconfiguration :
Misconfigurations in AWS Cognito can introduce security vulnerabilities that compromise user data and access control. Below are the most common misconfigurations:
1.Weak Password Policies
2.Overly Broad Permissions for Identity Pool Users
3.Unverified User Access
Enforce Strong Password Policies: Set strict password requirements (length, complexity) to reduce the risk of weak passwords.
Follow the Principle of Least Privilege: Ensure that Identity Pool users are only granted the minimum necessary permissions to perform their tasks.
Require User Verification: Enforce email or phone verification to confirm the identity of users before granting access to sensitive resources.
Enable Multi-Factor Authentication (MFA): Require MFA for all users, especially for sensitive or administrative accounts, to provide additional security.
Set Reasonable Token Expiration: Configure token expiration times to minimize the risk of long-lived tokens being misused.
To detect and prevent misconfigurations in AWS environments, several key tools are essential. AWS Config monitors resource configurations for issues like public S3 buckets and insecure IAM roles, while AWS Inspector scans EC2 instances for vulnerabilities. AWS Trusted Advisor provides real-time security recommendations, and AWS Security Hub centralizes findings from services like GuardDuty for a comprehensive security overview.
Third-party tools such as Prisma Cloud offer real-time monitoring, and Pacu helps simulate attacks to identify vulnerabilities. Dome9 automates security policy enforcement.
For automated detection and remediation, AWS Lambda can fix misconfigurations like public S3 permissions, while AWS CloudWatch triggers alarms for unusual access patterns. AWS Config Rules allow for custom rules that can automatically correct issues, enhancing overall security.
Misconfigurations in AWS pose significant security risks, exposing sensitive data and enabling unauthorized access. Common issues, such as misconfigured S3 buckets and overly permissive IAM policies, often arise from a lack of awareness or rushed deployments. To mitigate these vulnerabilities, understand the AWS shared responsibility model and implement best practices like the principle of least privilege, regular audits, and stricter access controls. While AWS provides robust security tools, the responsibility for proper configuration rests with you. Stay proactive, automate security checks, and prioritize the security of your cloud environment.
Share