Cortex Configuration
Harsh Radadiya
Aug 19, 2024
•
3 Min
Harsh Radadiya
Aug 19, 2024
•
3 Min
TABLE OF CONTENTS
Share

Hardware requirements depends on the usage of the system. We recommend starting with dedicated resources:
Cortex has been tested and is supported on the following operating systems:
If you are using one of the supported operating systems, use this all-in-one installation script:
wget -q -O /tmp/install.sh https://archives.strangebee.com/scripts/install.sh ; sudo -v ; bash /tmp/install.sh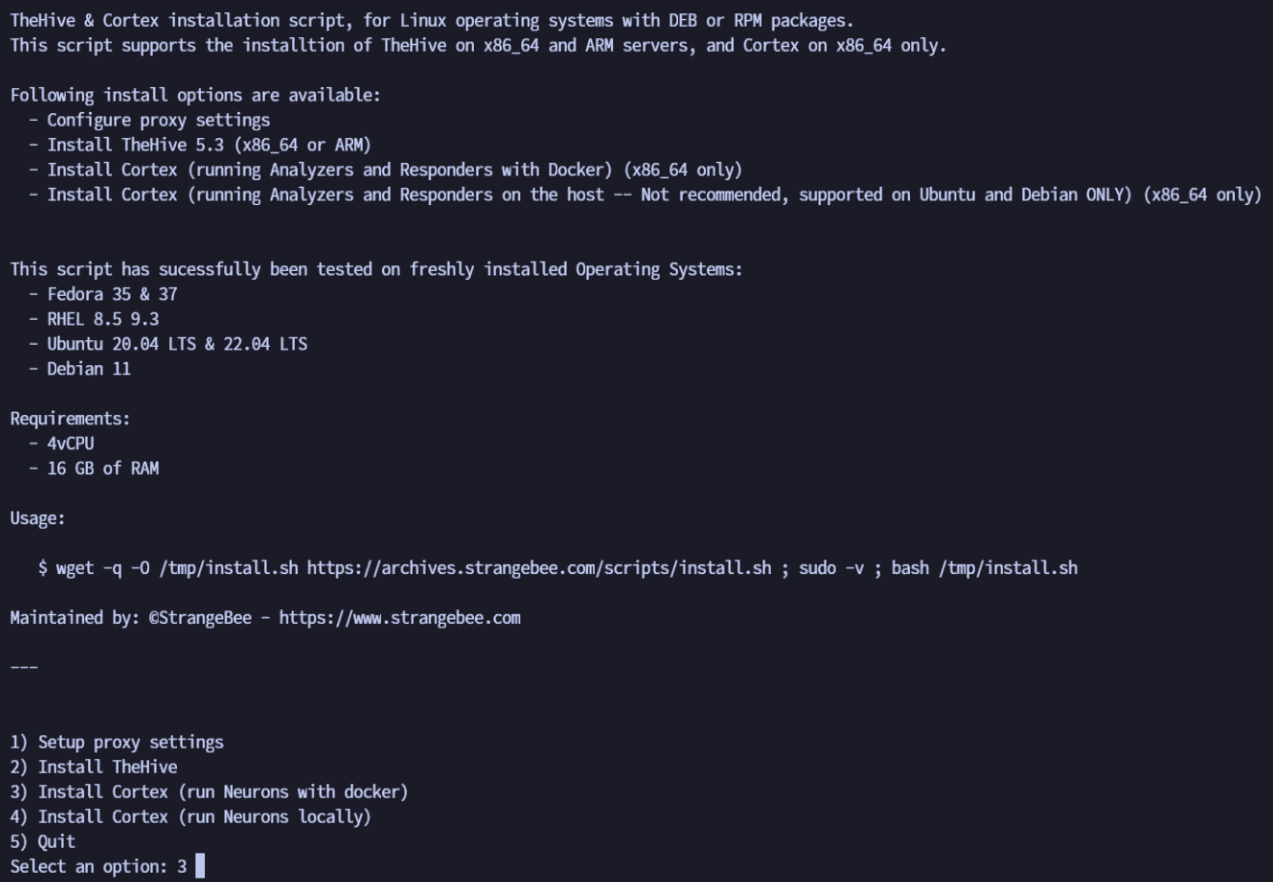
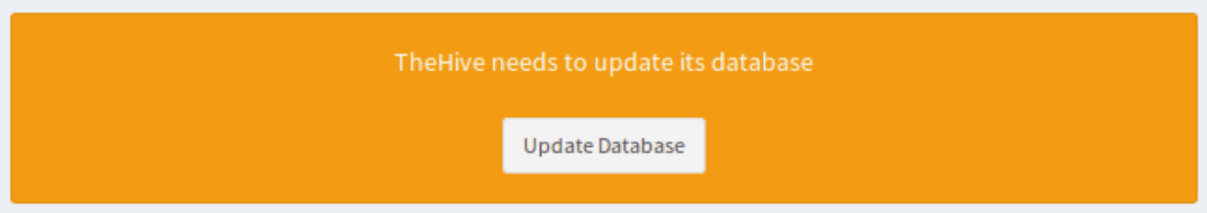
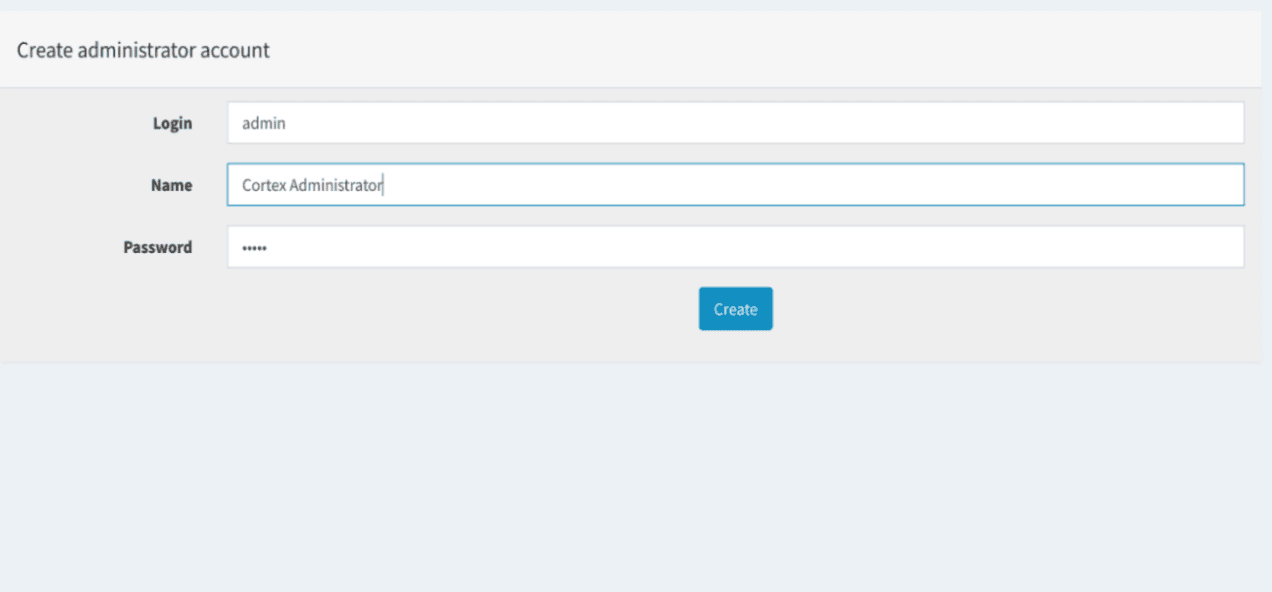
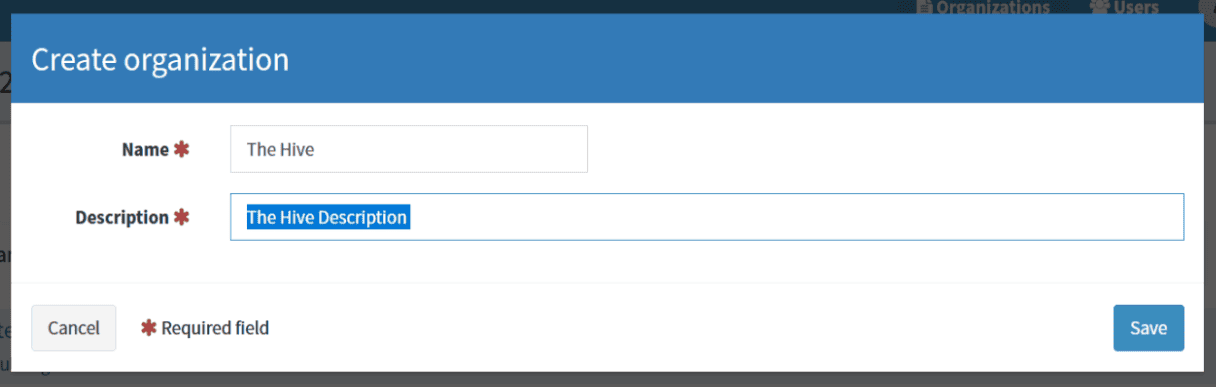
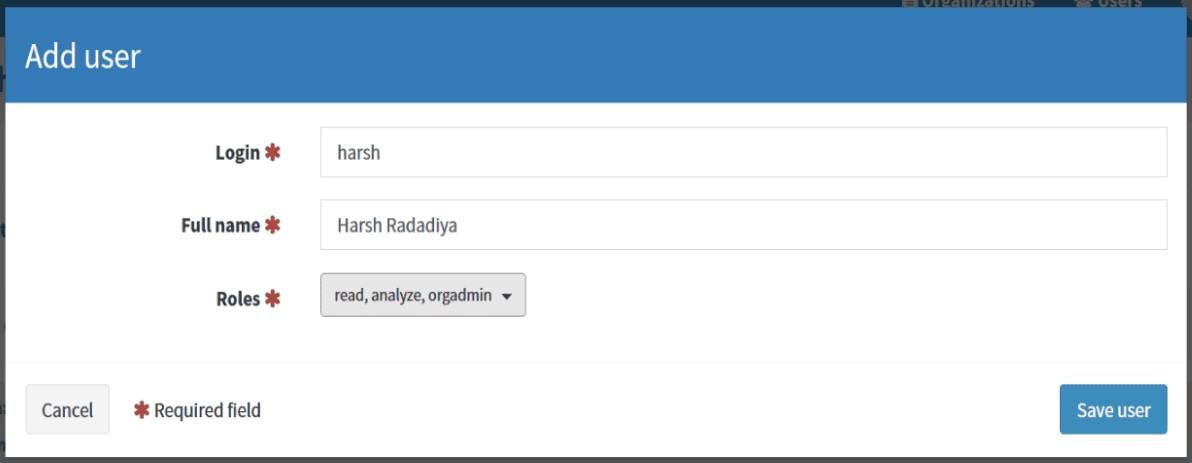
When Cortex is installed and configured, open your web browser and connect to :
http://<CORTEX_IP>:9001.

Share