Hacking the Cloud: A Deep Dive into Azure Pentesting
Divy Kansara
Oct 8, 2024
•
5 Min
Divy Kansara
Oct 8, 2024
•
5 Min
Initially, we will be discussing the basics of how Azure assigns roles and how azure works.?
Azure is a cloud computing service operated by Microsoft for application management via Microsoft-managed data centers. It supports many languages, tools, and frameworks, including both Microsoft-specific and third-party software and systems.
Some Terminology Regarding Azure
Some Architecture regarding Azure.
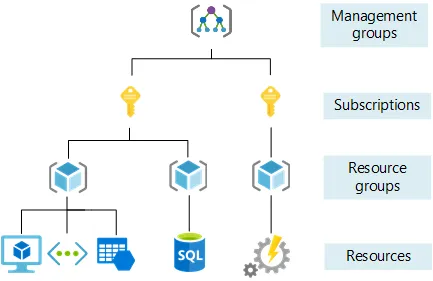
Management Group
Subscriptions
Resource Groups and Resources
Azure RBAC Roles
Azure RBAC Assignment
Azure AD Roles
You only know the domain name of a company that you will perform the penetration test, for example RetailCorp and Microsoft, based on this information, we can obtain some useful information from here. These are listed below;
Tenant Name
Tenant is represents an organization in Azure Active Directory and it’s an instance ID. You can query the validity of the user’s login information and tenant name on the following endpoint.
https://login.microsoftonline.com/[email protected]&xml=1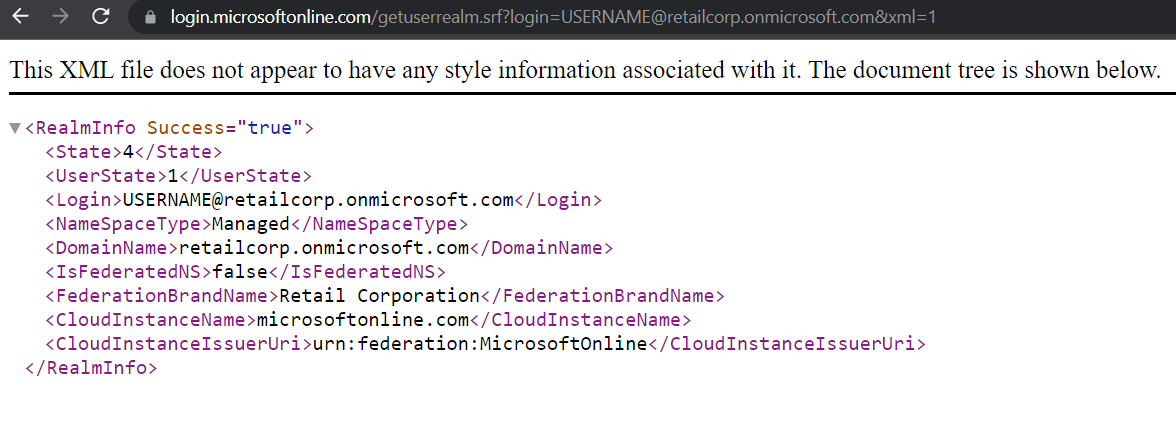
Tenant ID
https://login.microsoftonline.com/retailcorp.onmicrosoft.com/.well-known/openid-configuration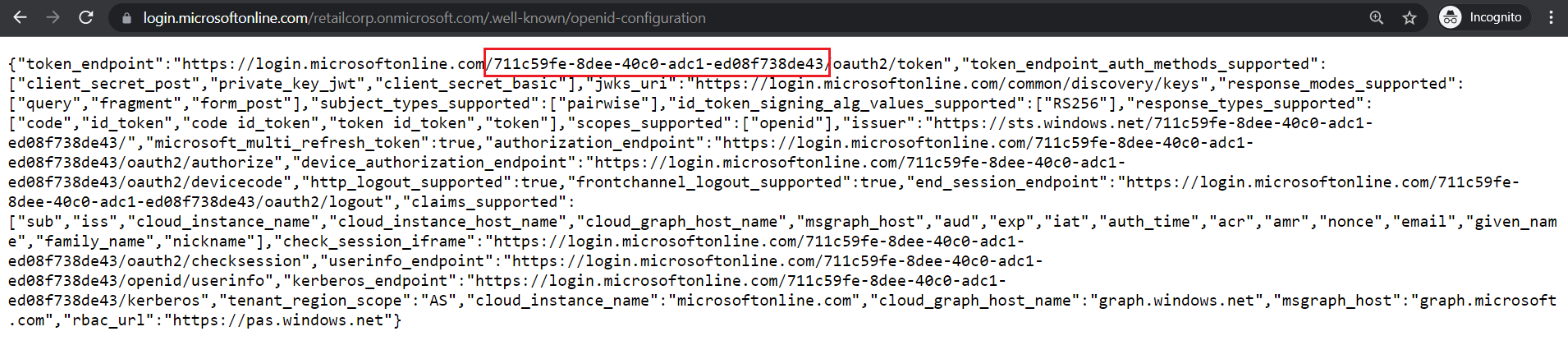
We can also use tools like AADInternals (https://github.com/Gerenios/AADInternals) for finding the above!
We can use MicroBuster to look for services used by RetailCorp.
Let us first find out the services used by the target tenant:
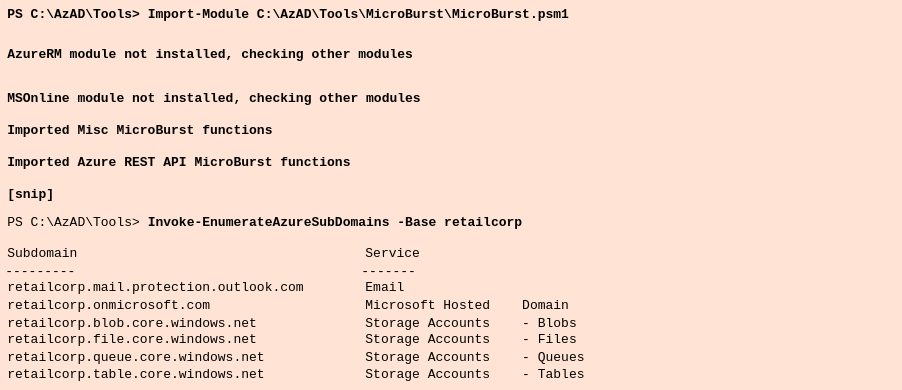
Domains
We can use the following commands to detect the subdomains of the domain on Azure.
Import-Module .\\AADInternals.psd1 -Verbose Get-AADIntTenantDomains -Domain microsoft.comEmail IDs
python.exe o365creeper.py -f emails.txt -o validemails.tAzure services
Accessibility of which services using on Azure by Azure AD users must be checked. Depending on the determination of which services and memberships can be used, different attack surfaces can be created.
Import-Module MicroBurst-master\\Misc\\Invoke-EnumerateAzureSubDomains.ps1
Invoke-EnumerateAzureSubDomains -Base defcorphq -VerboseAccessing to the Azure AD environment can be achieved in many ways. The main ones of them are given below
In this blog, we demonstrate how to gain initial access by leveraging publicly available Azure Blob storage.
Public Azure Blobs
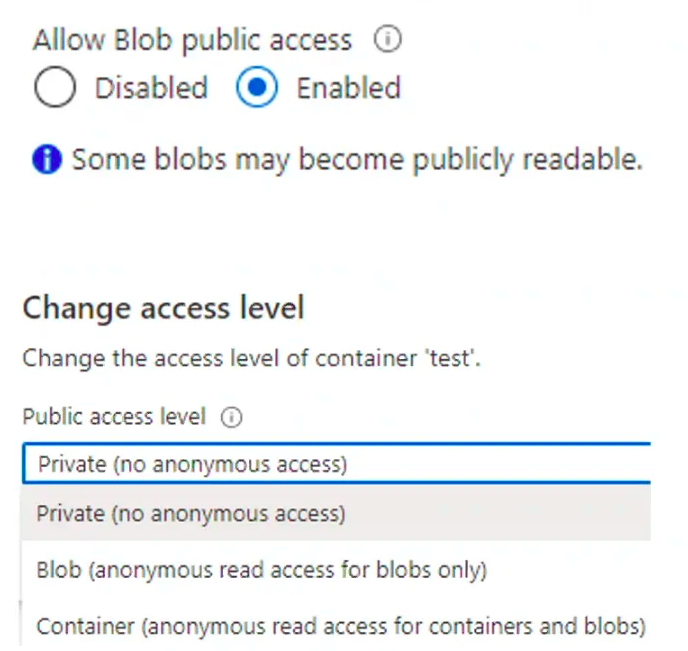
Invoke-EnumerateAzureBlobs -Base retailcorpThis script will try to find the anonymous readable blobs/containers inside the domain.
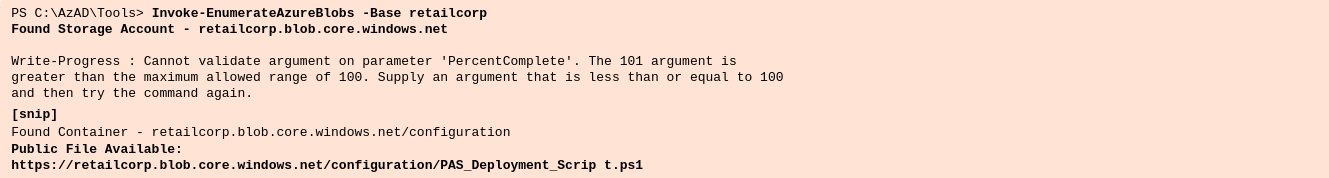
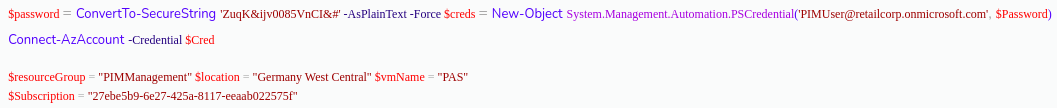
There is a script available in a container called 'configuration'. Let's check out its contents!
The script seems to be a VM deployment script and it contains a username and password in clear-text in very first lines!
Stay tuned for the next part, where we'll dive into privilege escalation and lateral movement in Azure.
Share