How Wazuh Simplifies Threat Detection for SOC Teams
Shrey Shah
Nov 29, 2024
•
3 Min
Shrey Shah
Nov 29, 2024
•
3 Min
TABLE OF CONTENTS
Share
In the ever-evolving landscape of cybersecurity, Security Operations Center (SOC) teams face an uphill battle in detecting and mitigating threats. To stay ahead, organizations need robust tools that simplify threat detection without compromising on effectiveness. Wazuh, an open-source SIEM tool, delivers on this promise with its exceptional capabilities, empowering SOC teams to detect, analyze, and respond to threats efficiently.
This blog delves into how Wazuh's features streamline threat detection and highlights practical examples of how it has improved our security posture.
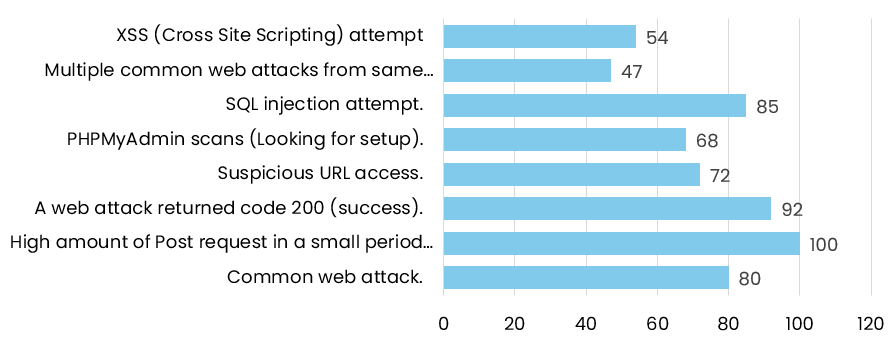
1. Web App Attacks:
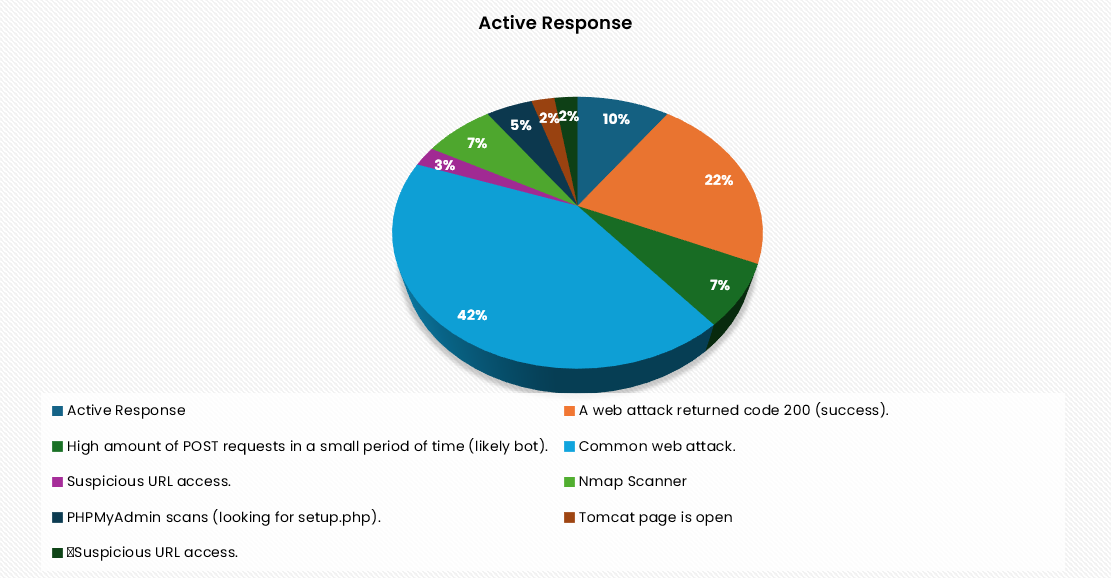
2. Active Response:
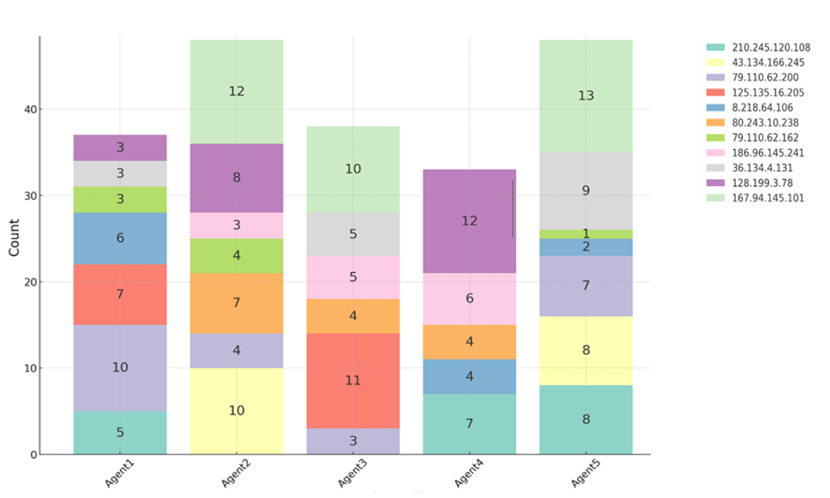
3. Agent-Wise Analysis:
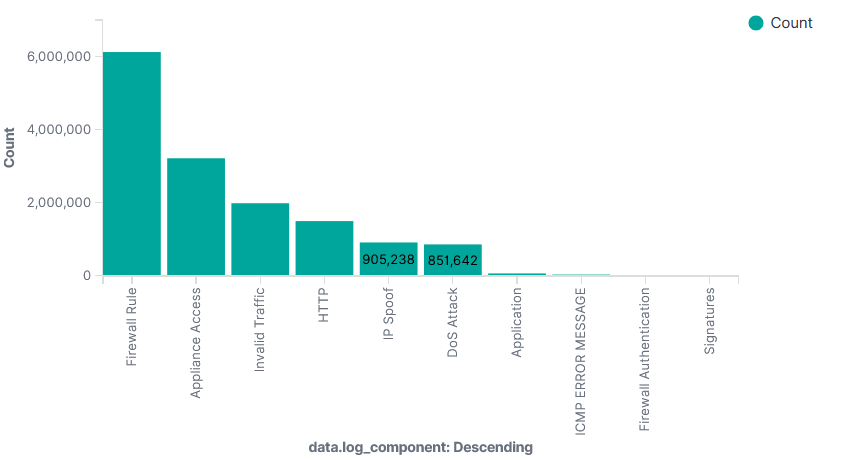
4. Firewall Security Insights:
Log Component Sophos Firewall
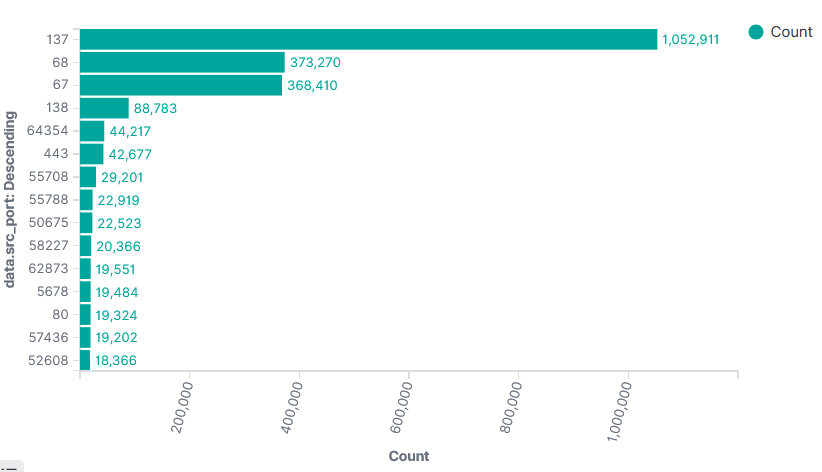
Top 15 Source Port Sophos Firewall
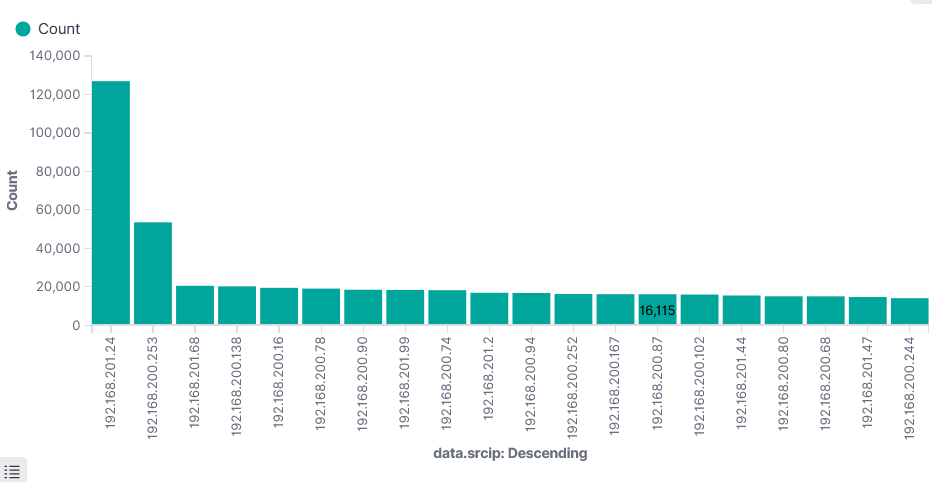
Top 20 Source IP Invalid Traffic Deny
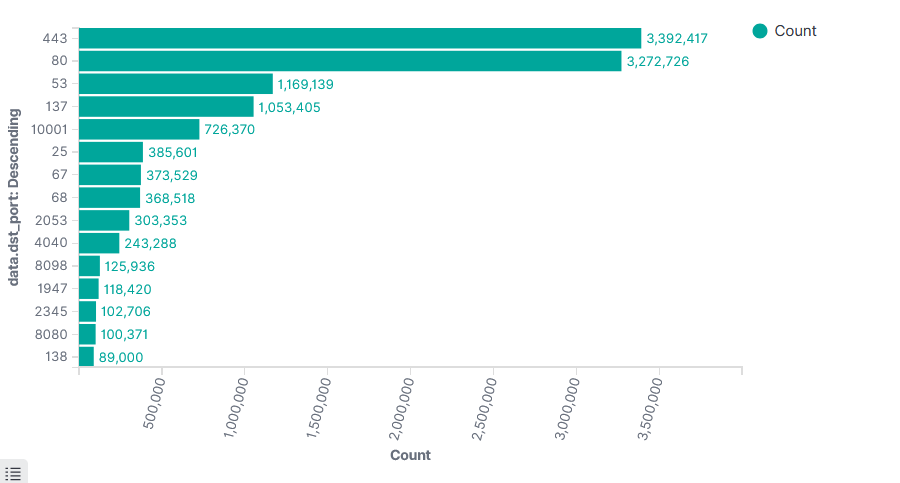
Top 15 Destination Port Sophos Firewall
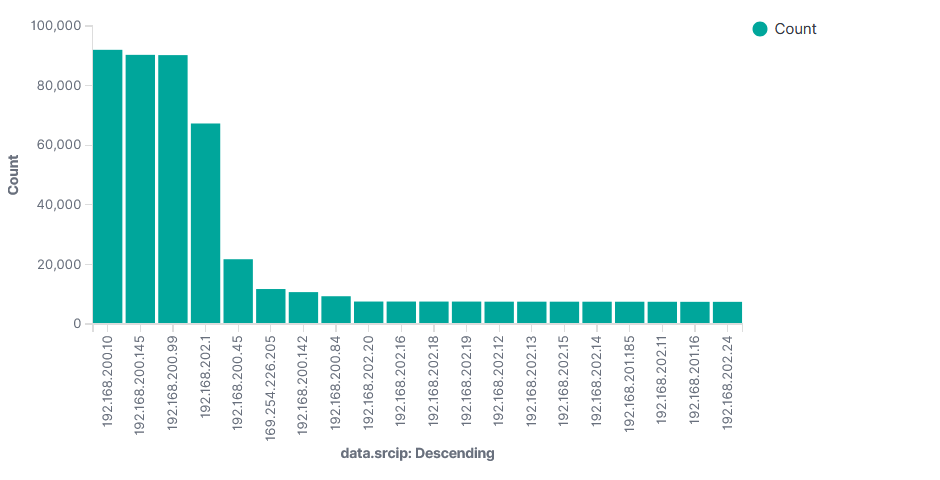
Top 20 Source IP Spoof Deny
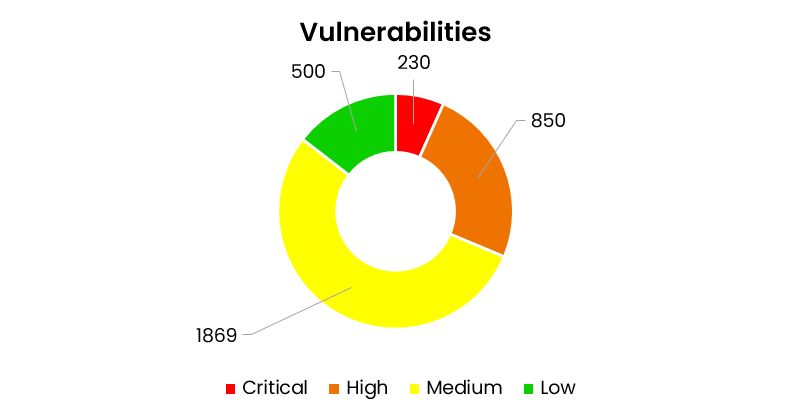
5. Vulnerability Management:
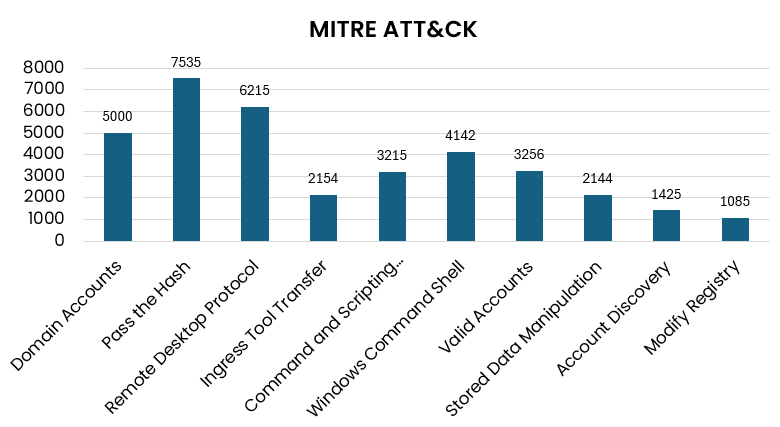
6. Mitre Techniques Visualization:
Wazuh collects and analyzes logs from a wide range of devices, applications, and systems. It supports various log formats, including JSON, syslog, and custom formats, ensuring seamless integration with your existing infrastructure.
Key Capability: Detect anomalies and malicious activity through real-time log analysis using pre-built and custom decoders.
Wazuh integrates with external threat intelligence sources, enabling SOC teams to correlate indicators of compromise (IOCs) with internal logs. This proactive approach ensures timely identification of potential threats.
Key Capability: Block known malicious IPs, domains, and file hashes with updated threat intelligence.
SOC teams often juggle compliance and security. Wazuh simplifies this by offering built-in compliance modules for frameworks like GDPR, PCI DSS, and HIPAA, helping organizations achieve regulatory compliance while enhancing security.
Key Capability: Automate compliance reporting and enforce security policies.
Wazuh’s FIM capability helps track unauthorized changes to critical files, a common indicator of compromise in cybersecurity incidents.
Key Capability: Detect file modifications in real-time to uncover potential breaches.
With cloud-native integrations, Wazuh provides robust monitoring of cloud environments like AWS, Azure, and Google Cloud, along with proactive vulnerability assessment.
Key Capability: Identify misconfigurations and vulnerabilities in cloud and on-prem environments.
Our SOC team recently detected a high volume of failed login attempts on a critical application. Leveraging Wazuh's real-time alerts, we identified this as a credential-stuffing attack. Wazuh's correlation rules helped us:
Outcome: Reduced the time to detect and respond from hours to minutes, minimizing business impact.
Phishing emails with malicious attachments targeting employees were flagged by Wazuh's threat intelligence integration. The decoders analyzed attachment hashes and matched them with known malware signatures.
Outcome: Proactively blocked phishing emails before they reached employees, improving our email security.
During a routine vulnerability scan, Wazuh identified several misconfigured AWS S3 buckets. By leveraging its cloud security capabilities, we remediated these vulnerabilities and reduced exposure to potential breaches.
Outcome: Enhanced cloud security posture by securing sensitive data.
Share