Mastering MISP Part-1
Shreya Dhameliya
Sep 20, 2024
•
7 Min
Shreya Dhameliya
Sep 20, 2024
•
7 Min
TABLE OF CONTENTS
Share
MISP (Malware Information Sharing Platform) is an open-source threat intelligence platform that facilitates the collection, sharing, and management of cybersecurity data. It enhances collaboration among organizations, enabling proactive defense against cyber threats.

These features collectively enhance an organization’s threat intelligence capabilities and improve overall cybersecurity posture.
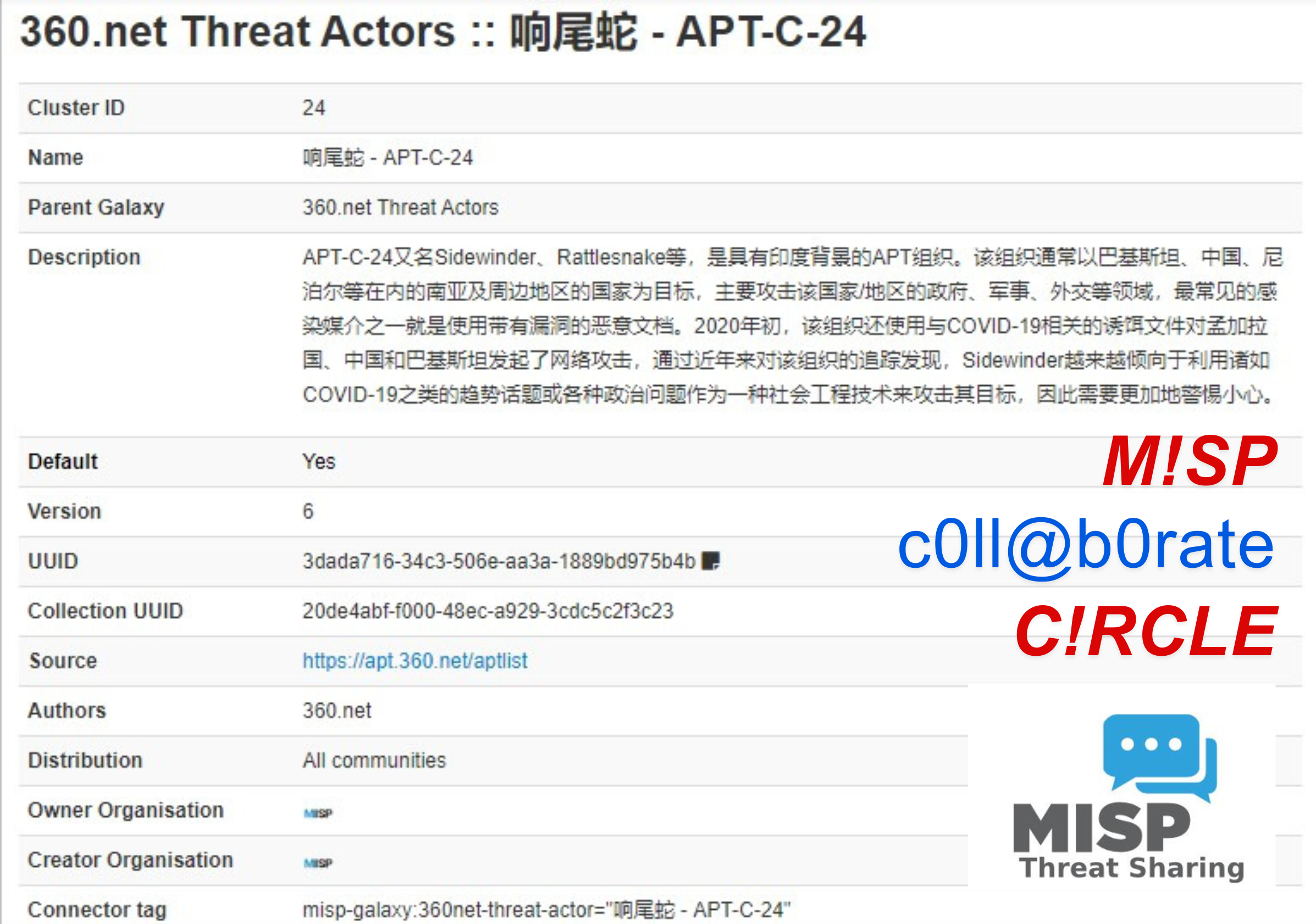
MISP is designed to be used by security analysts, incident responders, and threat intelligence analysts. These individuals typically use MISP within and across their own organisation, as well as between organisations and within broader threat intelligence sharing communities.
Both. MISP is a software application with a user interface. It also includes an API and can be interacted with programmatically. MISP runs on Ubuntu and Linux operating systems.
Organisations typically either self-host MISP on their own infrastructure, or use a hosted MISP provider such as CloudMISP.
Important Note:- Please execute commands only as a user, not as root.
Step: 1 First update & upgrade system using this command :
Linux Command:-
$sudo apt-get update -y && sudo apt-get upgrade -y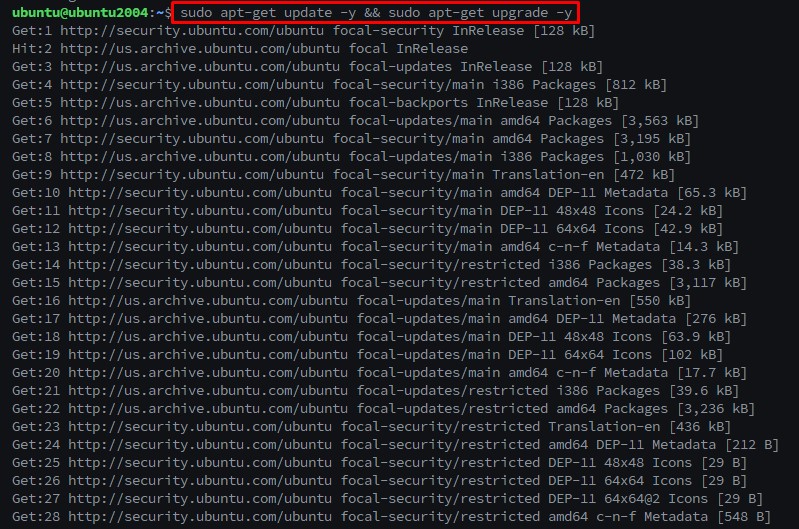
Step: 2 MISP requires Mysql-client available in our machine. Install Mysql-client using the below command.
Linux Command:-
$sudo apt-get install mysql-client -y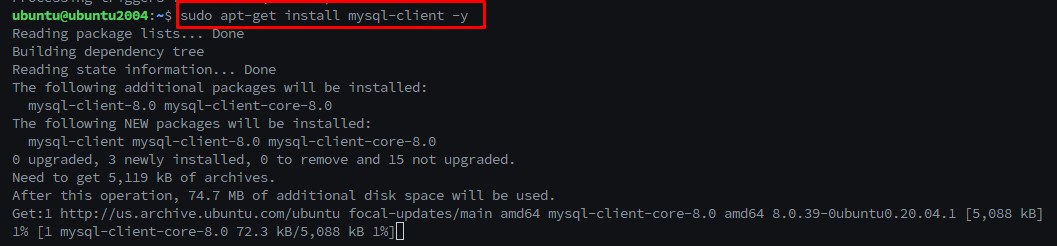
Step 3 : To install MISP on fresh ubuntu 20.04.1, all you need to do is the following. Just remember one thing this is an automated bash script that can’t run with Root privileges run this script with Non-root users.
● Install MISP with install.sh
Linux Command:-
Curl https://raw.githubusercontent.com/MISP/MISP/2.4/INSTALL/INSTALL.sh -o misp_install.sh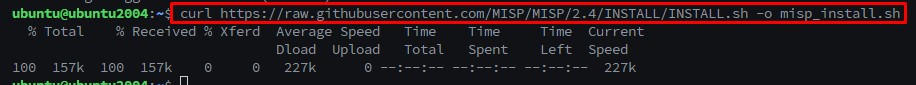
Step 4 : Change the permission of file misp_install.sh and make it executable. To do this run the following command. The script will need some time to install MISP on your Ubuntu platform.
Linux Command:-
$chmod +x misp_install.sh
$./misp_install.sh -A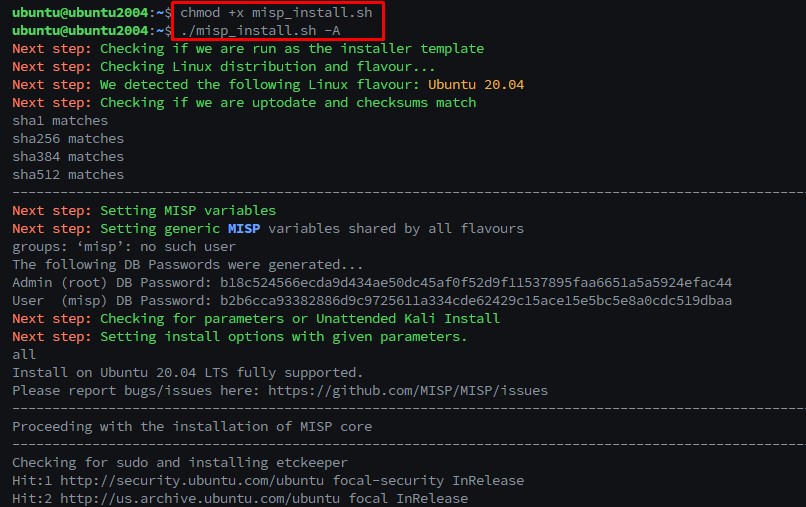
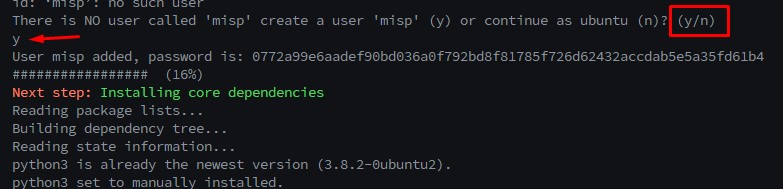
● In the middle of installation Enter “Y” to create MISP user.
Step 5 : Now, we are going to add a rule to firewall this will allow port 80/tcp and 443/tcp.
Linux command:-
$sudo ufw allow 80/tcp
$sudo ufw allow 443/tcp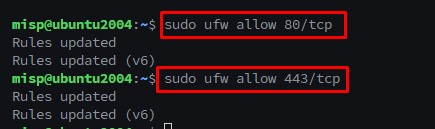
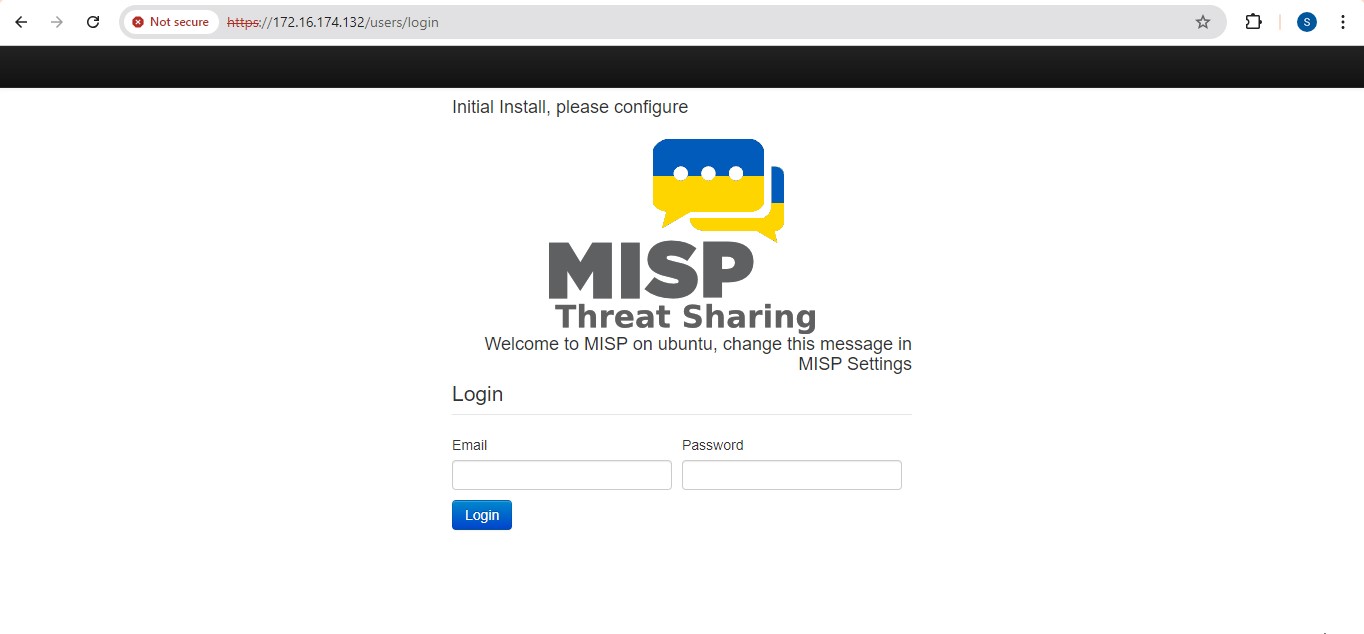
Step 6 : After, the installation of MISP we can use a browser to connect to MISP.
● By Default, MISP is listening on loopback address or Base URL To access MISP on your browse the following URL :
● https://172.16.174.132/users/login
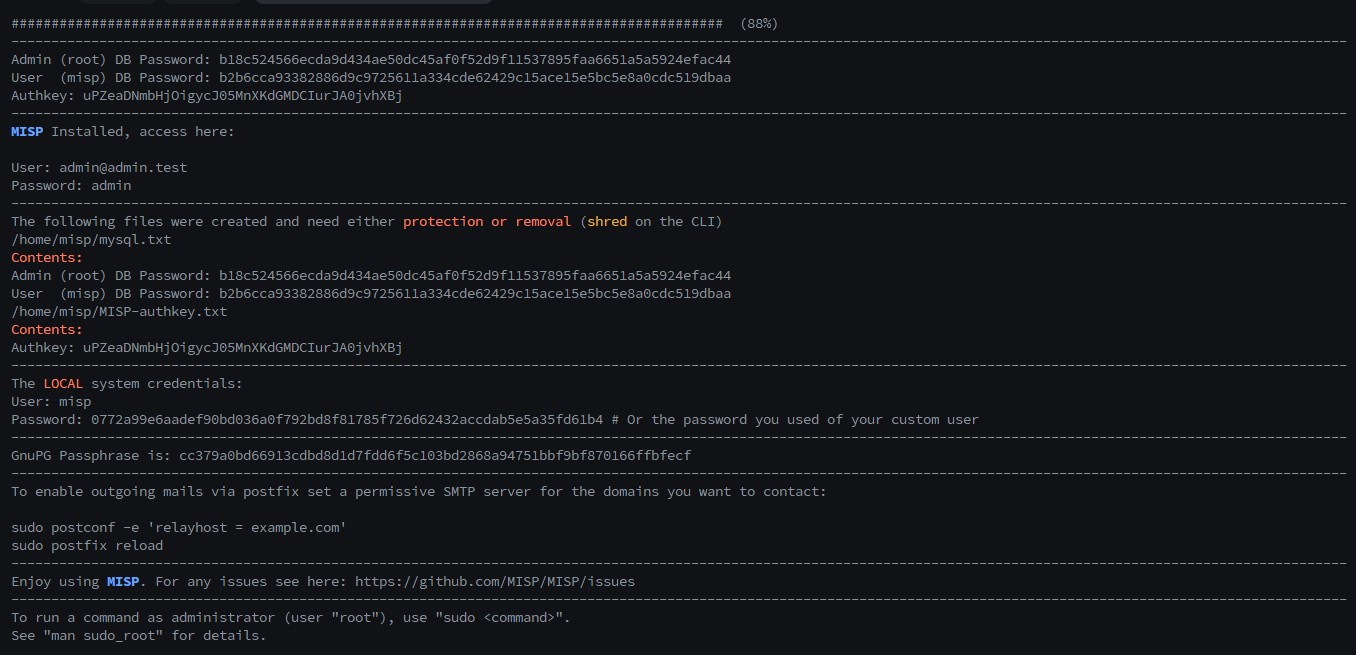
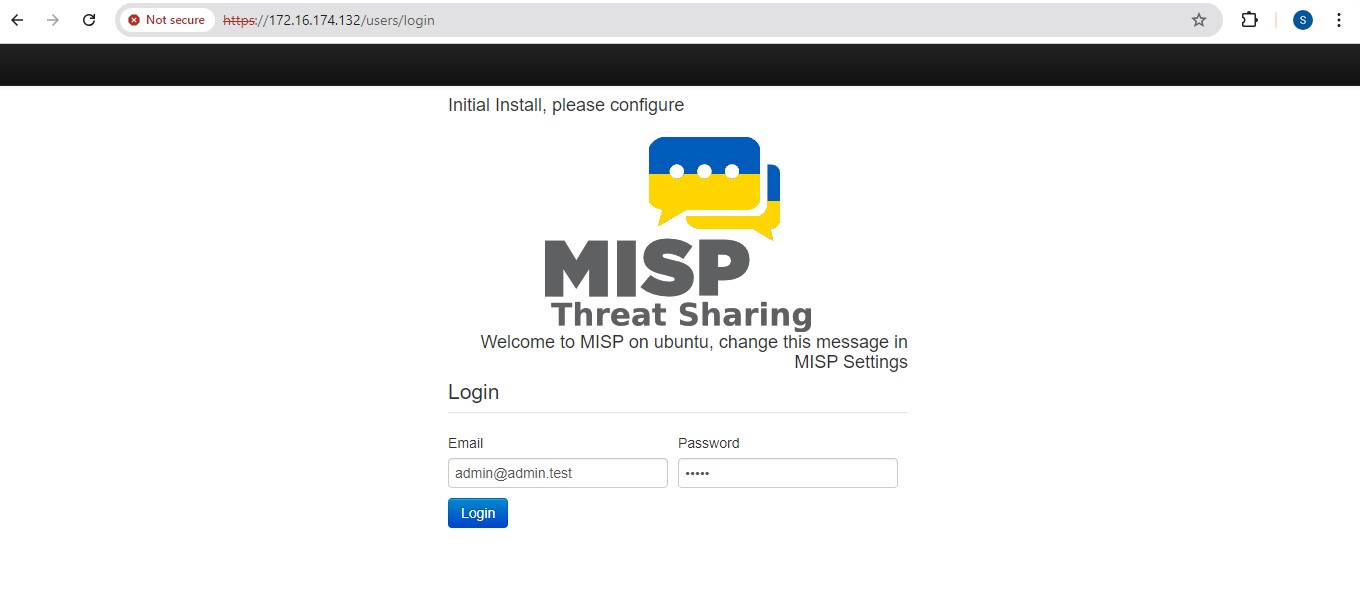
Default Credentials :-
For the MISP web interface -> [email protected]:admin
For the system -> misp:Password1234
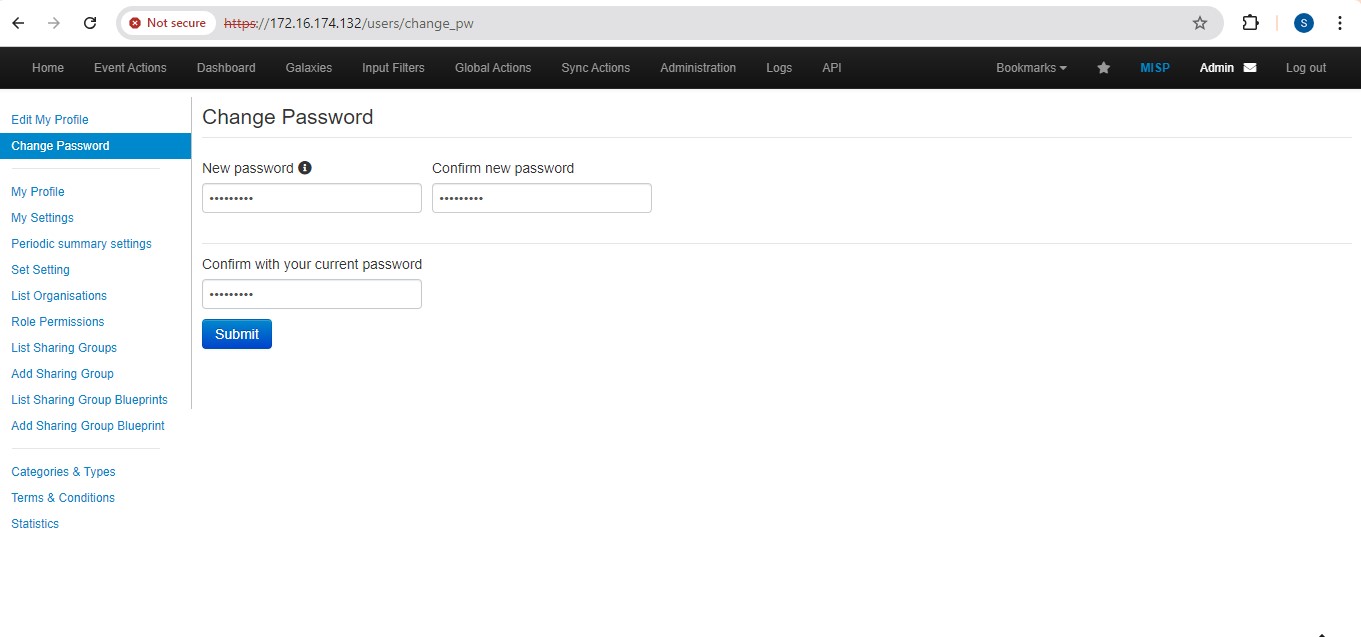
Enter new Password
The password must be in standard form. Minimum Length of password is at least 12 words that contain upper case & lowercase alphabet, special character and a numerical value.
For example – Strong@12345
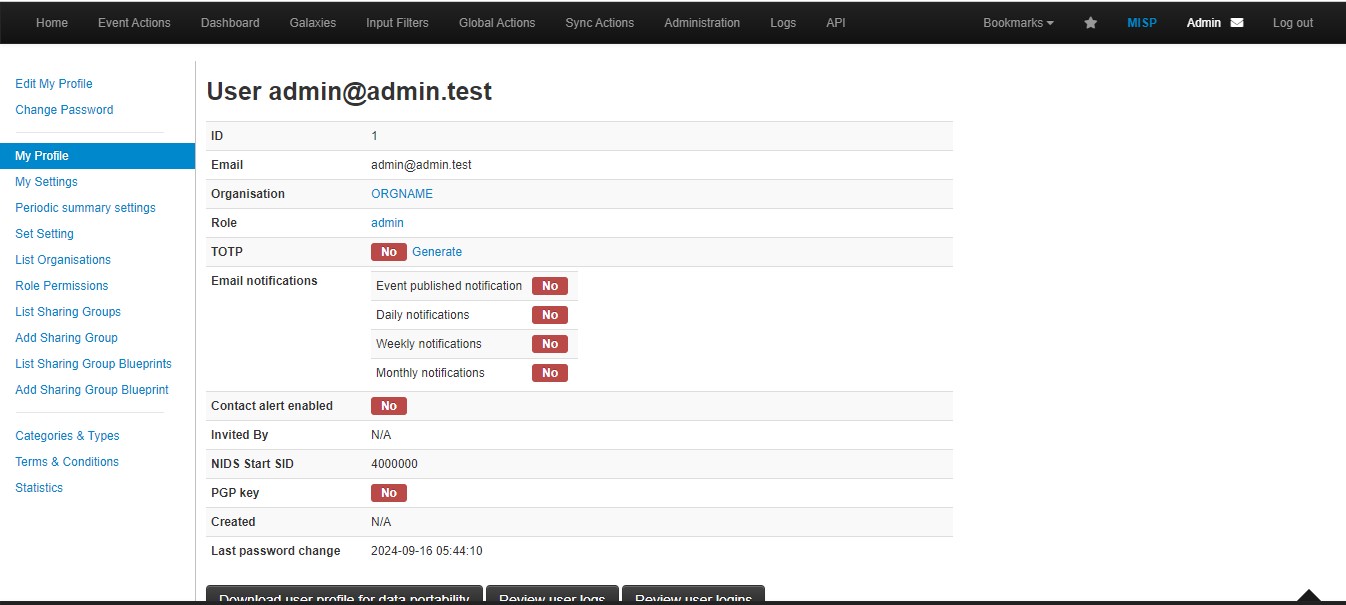
To enable feeds you will need to login to MISP console with the superuser account which is [email protected] account.
This one is a little bit special, as we can go into the “Sync actions” tab to build our panel.
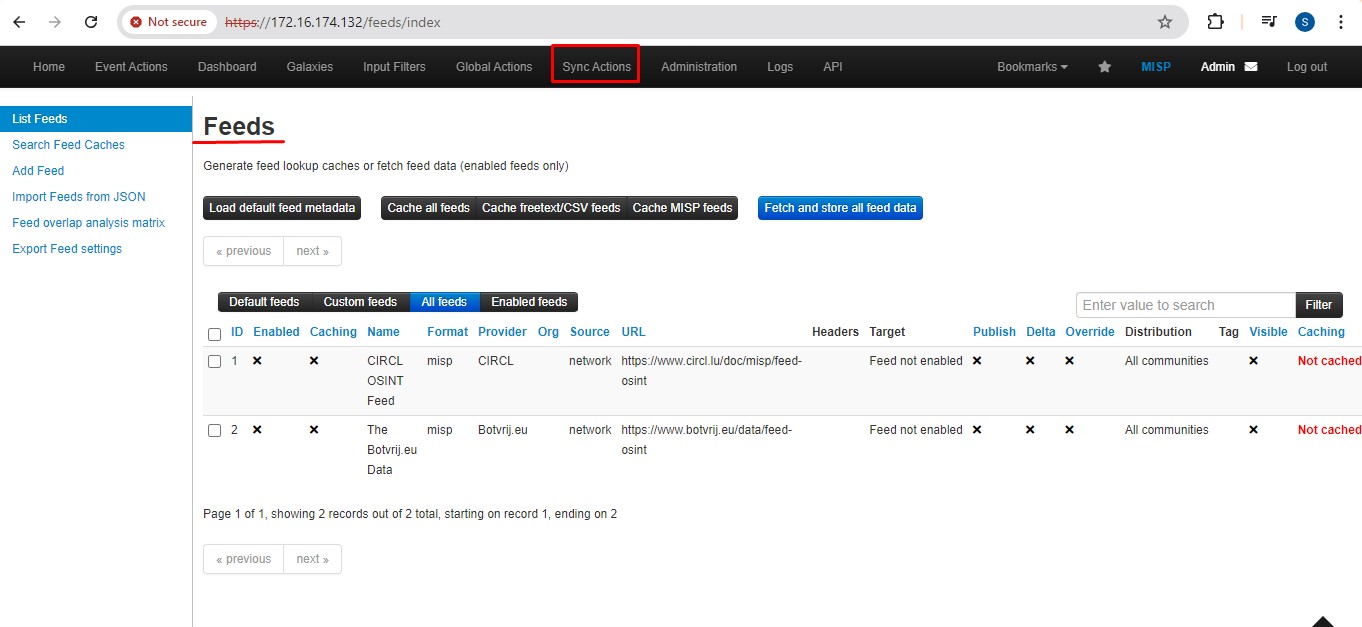
When entering the Sync actions tab, select the list feeds tab.
From there find feeds such as CIRCL osint and check feeds tab.
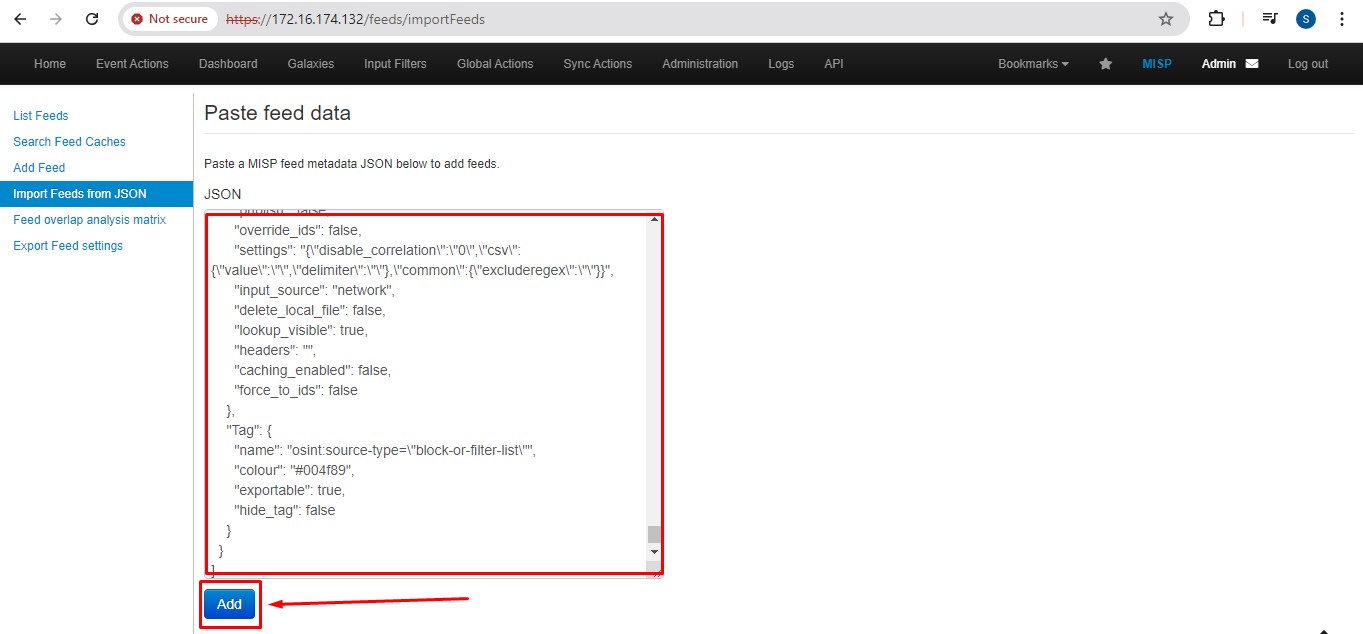
If you want to import feeds from a JSON file, navigate to the appropriate tab.
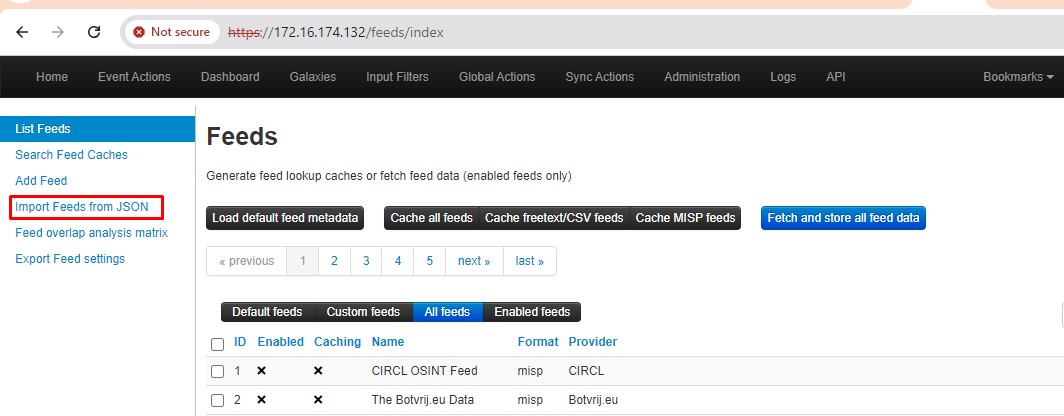
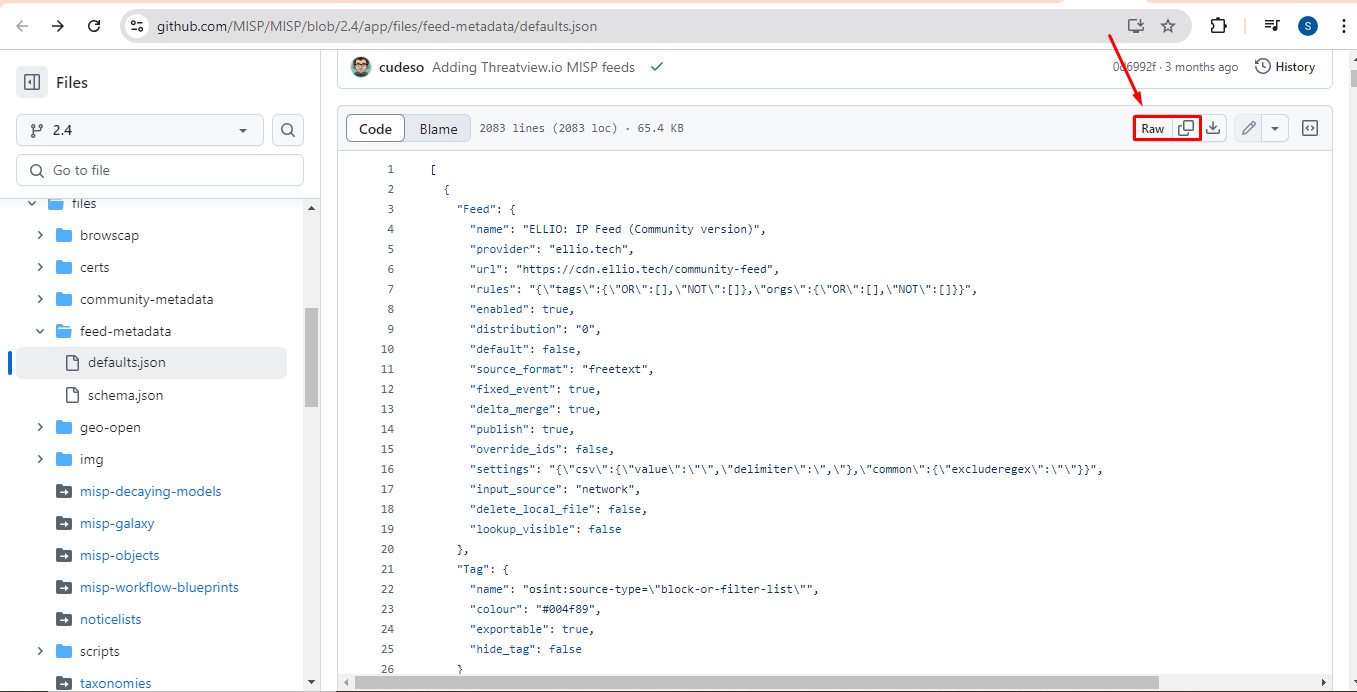
Here, you can see the option to import feeds. You can add a JSON feed file to download additional feeds.
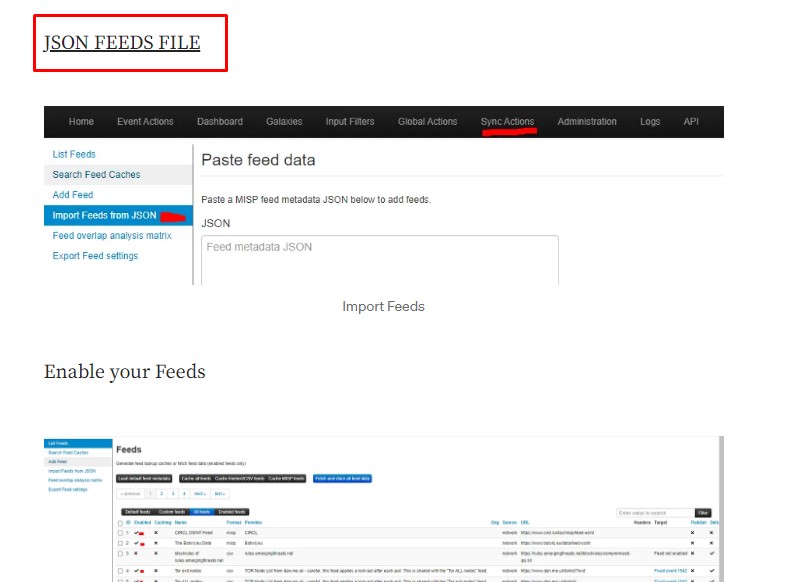
From the list provided here, you can obtain another JSON feed file to import additional feeds.
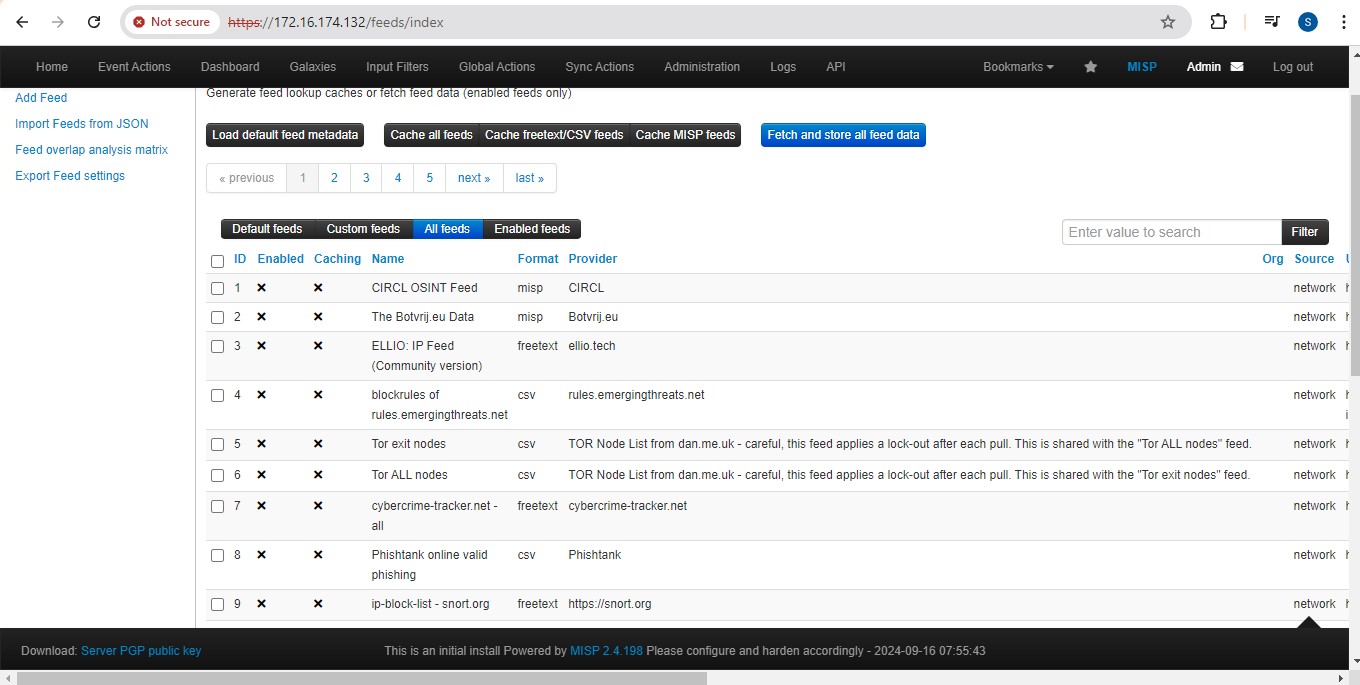
Here, you can view all the additional feeds available.
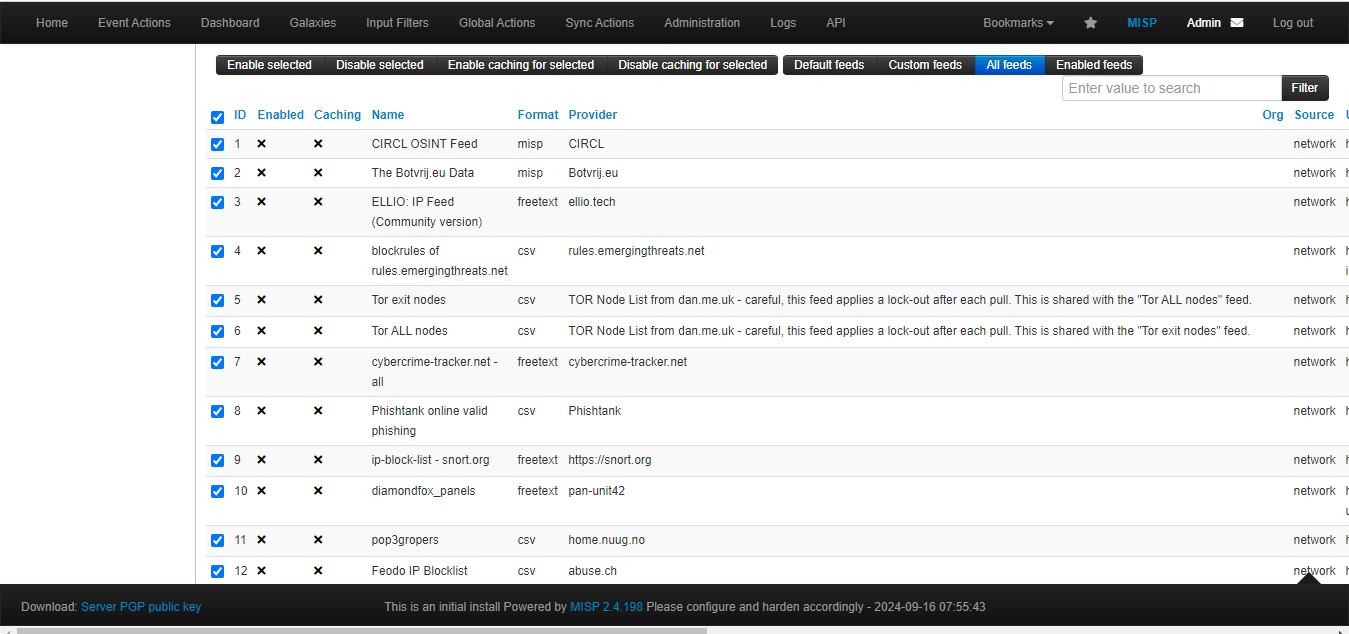
Now, you need to select all feeds and enable them.
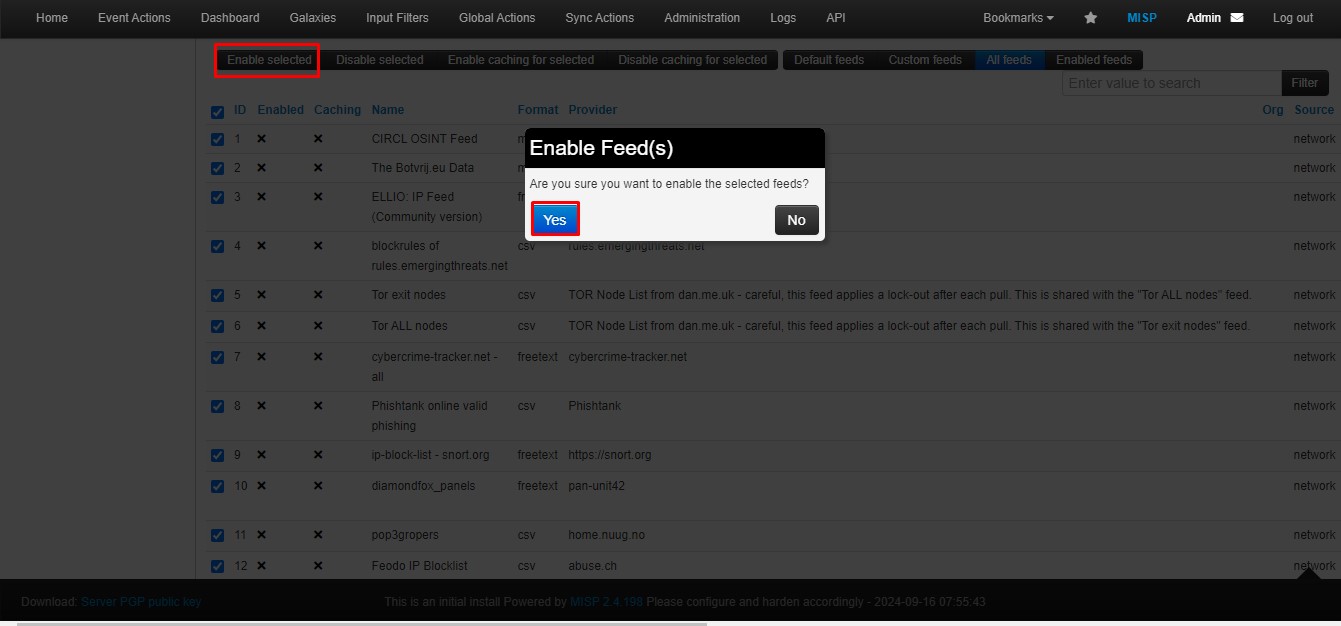
After that, go to Administration, then navigate to Jobs, and download all the feeds.
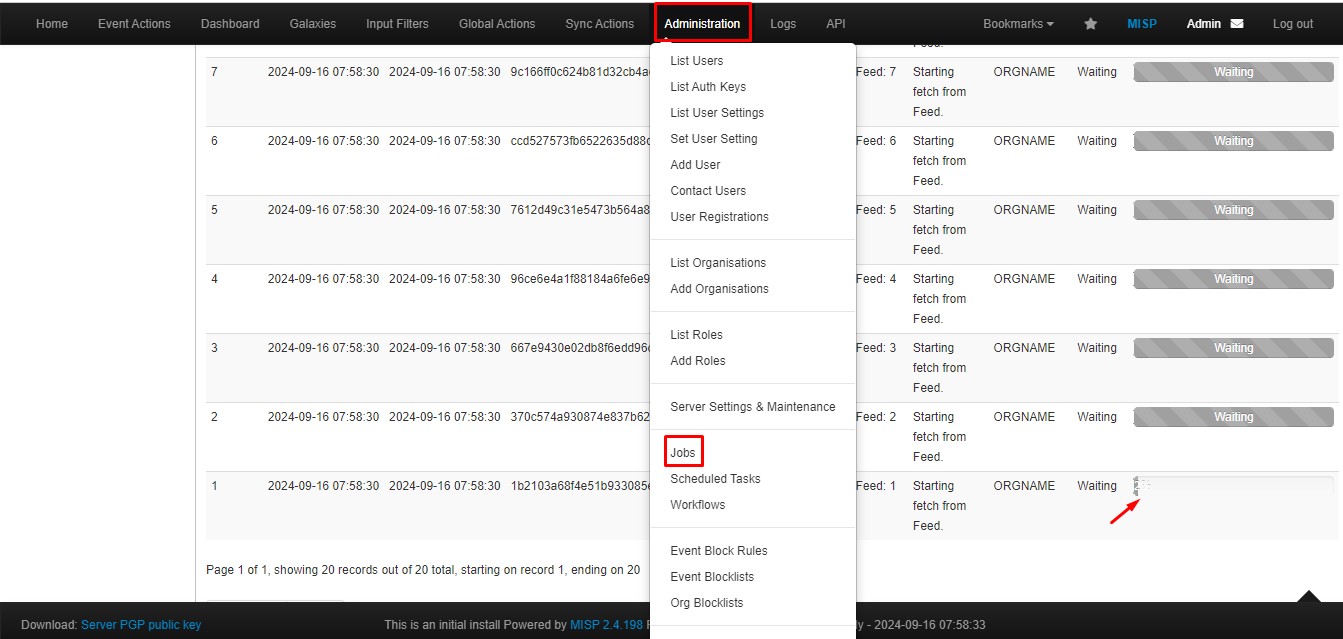
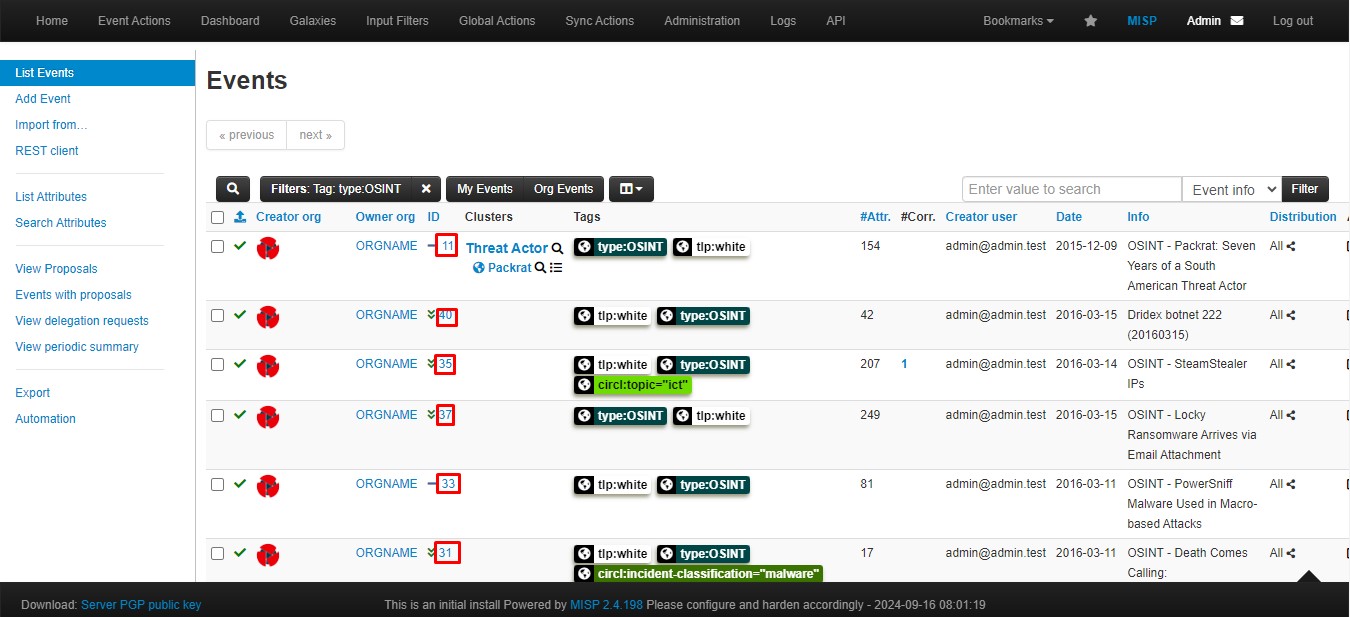
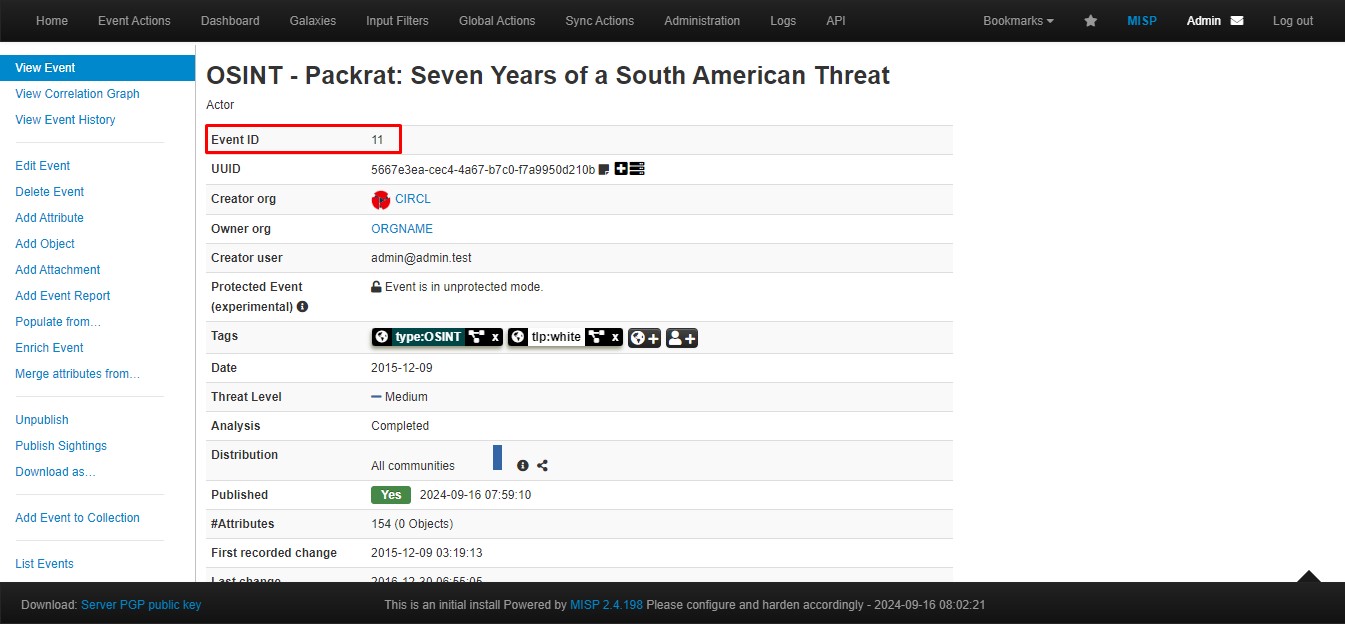
After downloading the feeds, you can list all events by going to List Events.
In summary, MISP (Malware Information Sharing Platform) is a powerful tool for organizations seeking to enhance their cybersecurity posture through effective threat intelligence sharing. By providing a structured framework for collecting, managing, and disseminating threat information, MISP facilitates collaboration among diverse entities, enabling them to respond proactively to emerging threats. Its rich features, including event sharing, feed management, and robust API integration, empower users to streamline their threat intelligence workflows and improve incident response capabilities. Embracing MISP not only fosters a culture of information sharing but also strengthens the collective defense against cyber threats in an increasingly complex landscape.

Share