Securing Your Software: Thick Client Application Security Strategies
Viren Punjabi
Apr 3, 2024
•
6 Min
Viren Punjabi
Apr 3, 2024
•
6 Min
TABLE OF CONTENTS
Share
Analyzing the target application
Calling out all the security researchers out there, let’s talk about Software Cracking, A.K.A. Thick Client Pentesting and application. A super interesting clue finding game revealing secrets of the target application. If you are observant and curious to solve mysteries then you’re in for a treat !
Before we jump in, let’s get the basics clear. It is highly recommended that you as a pen tester are aware of tackling different situations in windows. This is important because this will help you find your way around complex situations more effectively. You should Know your way around windows like what file types are being used, how processes execute, what files are required in foreground as well as what’s going in the background, How the registry works and so on.
Disclaimer: This blog post is provided for educational purposes only. The techniques and information discussed are intended to enhance understanding of security concepts and practices. The author does not condone or encourage any illegal or unethical activities. The reader is solely responsible for how they choose to use the information presented. The author accepts no liability for any misuse or consequences arising from the application of the techniques described in this blog post.
Let the hacking begin !
Let’s understand what methodology is used while working on live projects.
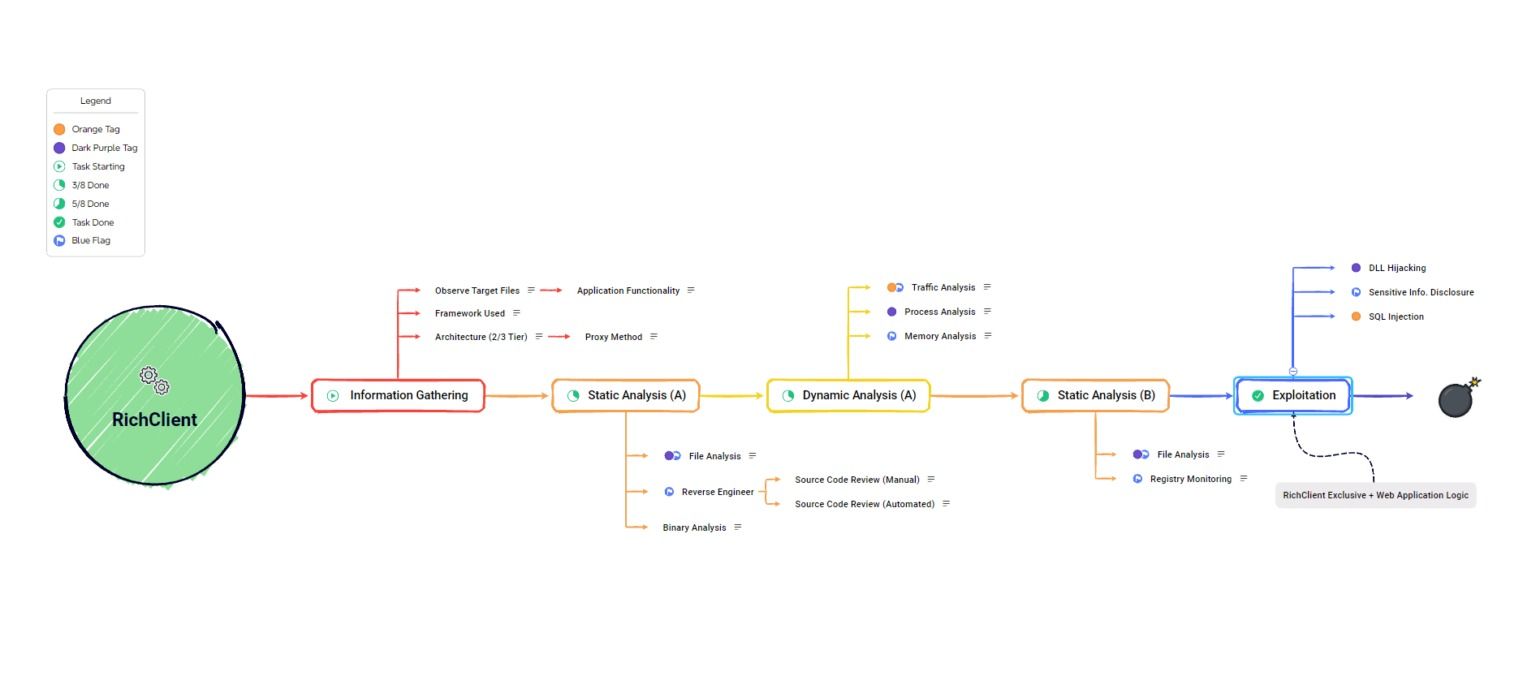
Thick Client Pen-testing Methodology
First things first; let’s get acquainted with our target. Manually interact with the files.
This will help us get a better understanding of the application’s functionality. We need to observe what each button does when interacting with them. Keep an eye out for what file extensions are being used, we also need to figure out what framework the application is developed on, We also need to know what architecture the application is built on (2 tier or 3 tier) that will further help us in deciding what proxy method to be using while further analysing our target. Knowing whether the application is proxy aware or non-proxy aware helps us decide how to approach the target further.
Once all that is figured out we will start with performing a static analysis. Starting by doing file analysis, we’ll use the sigcheck tool to check the digital signature and certificate status and use the file command in Linux. Knowing whether the DLL(s) are signed or unsigned is a good piece of information to know as it can lead to DLL Hijacking possibility which F.Y.I. is a severe vulnerability and reveal some sensitive information or clues.
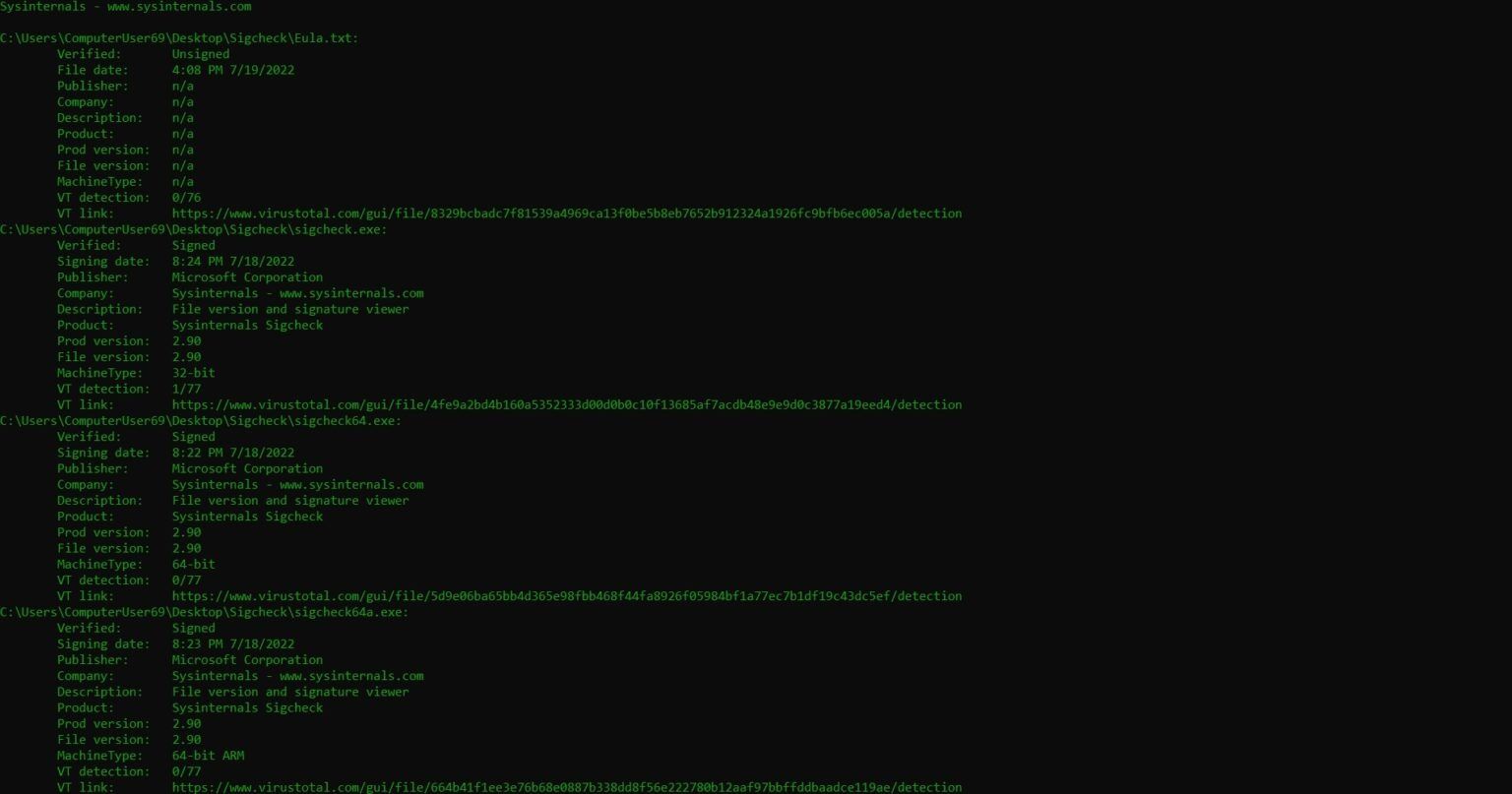 Sigcheck
Sigcheck
Looking at an application’s manifest is also a good starting point, a tool called Resource Hacker might come in handy here.
Next we will start to reverse engineer the application. This is super important because if this is done right it will help us discover major secrets about the target and thus play a major role in the pentest process. Tools like dot peek and Gidhra are the perfect match. We need to de-obfuscate the application to understand what’s going on and then start looking for sensitive information.
We need to keep our eye out for key and IV used for encryption. If you are successful and finding one then kudos for finding some legendary information. There are chances you will find some credentials (if stored) within code that’s good, bonus points for that. I mean for us not them 😉 for them it’s not good. Anyways, let’s move ahead. Oh and one more thing you can also automate the process but that’s not recommended for obvious reasons.
 dot peek
dot peek
We now are ready to start phase 3 that is dynamic analysis. We’ll start interacting with the application and observe how the software behaves and figure out how to proceed further. Analyzing how the data is traveling can help us reveal some juicy information. We’ll use a tool called Wireshark to monitor the network activity done between software and server. While observing the packers we might find API keys, credentials or even SQL queries opening the possibility for SQL injection.
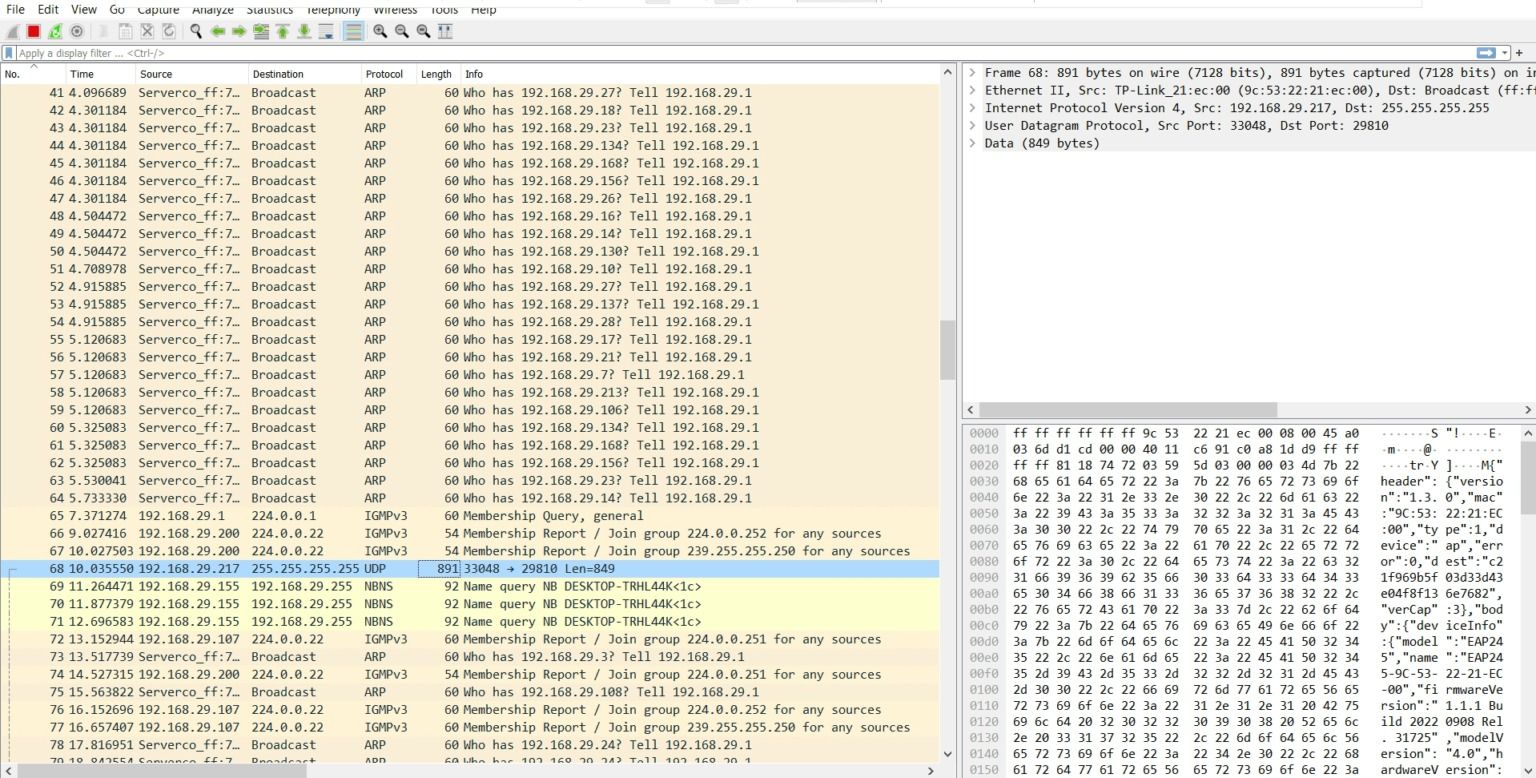 Wireshark
Wireshark
Once that’s done we’ll start with process analysis. We’ll start a tool called ProcMon and then interact with the application. We will start the application and observe what files are being loaded by the application, what files are called to help the application’s background tasks or where the data is being stored. You’ll find many different file types being used. Using a filter will help you save a lot of time and narrow down on files you need to focus on.
DLLs are needed to run in the background and are almost called by every software. Keep a note of what files are being called and from which location. Location is important because it will help us figure which DLL to hijack. We can now craft a payload to spoof that leading to RCE or reverse shell. Pro tip-(don’t try to spoof DLLs being called from system32 if you are not sure of what you are doing). It’s not limited to DLL files only, there can be other clues revealing sensitive information or help us figure out the next step. Being observant is necessary to find a lot of things that might be hiding in plain sight.
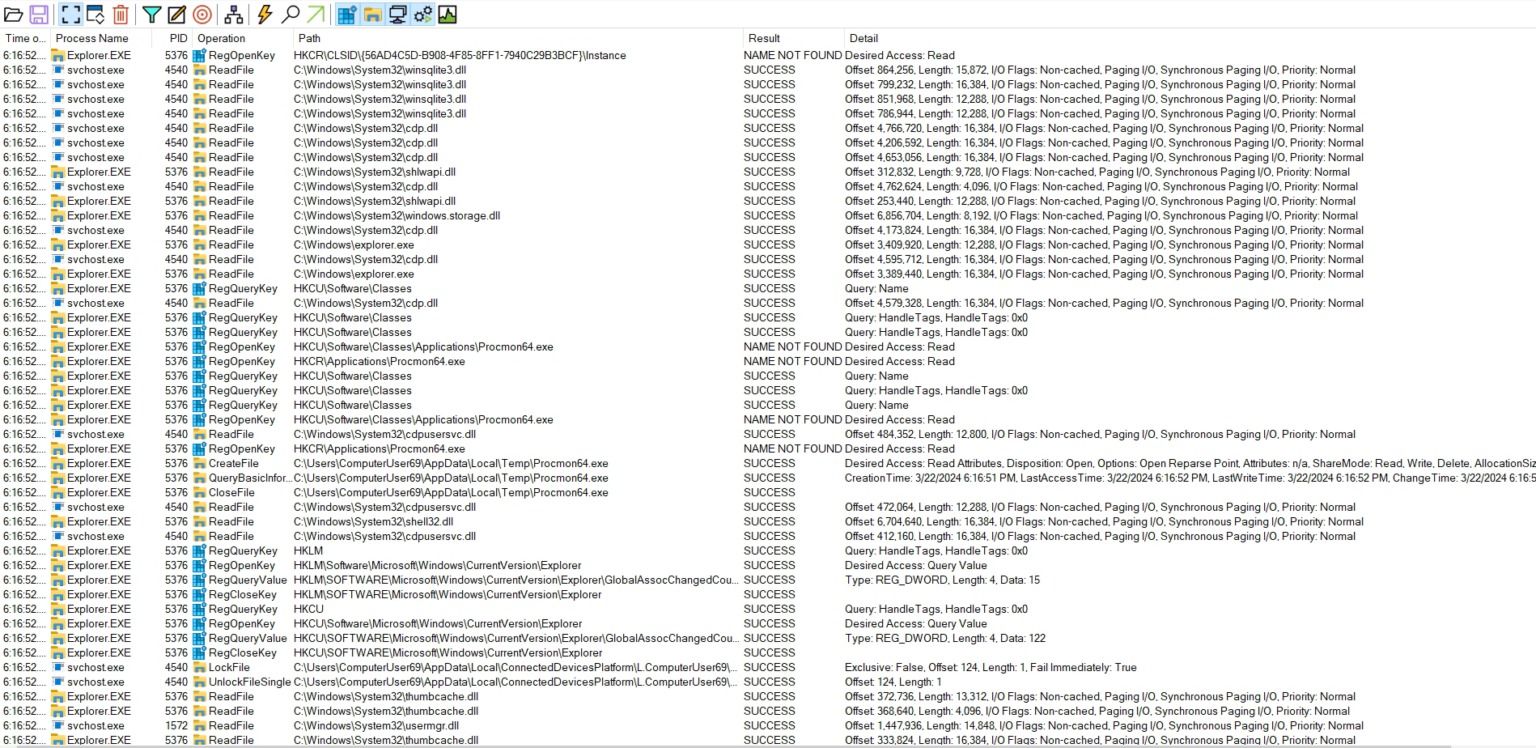 ProcMon
ProcMon
Oh, and don’t forget to do a memory analysis. Use tools like Process Explorer or Process Hacker to find out what is being loaded in memory at the time of execution. The tool can be daunting at start but give it some time; things will start to make sense. Look for registry keys, you might find some credentials or API keys being stored. Observe what information is being called when, this will help us figure out what and how to use that information.
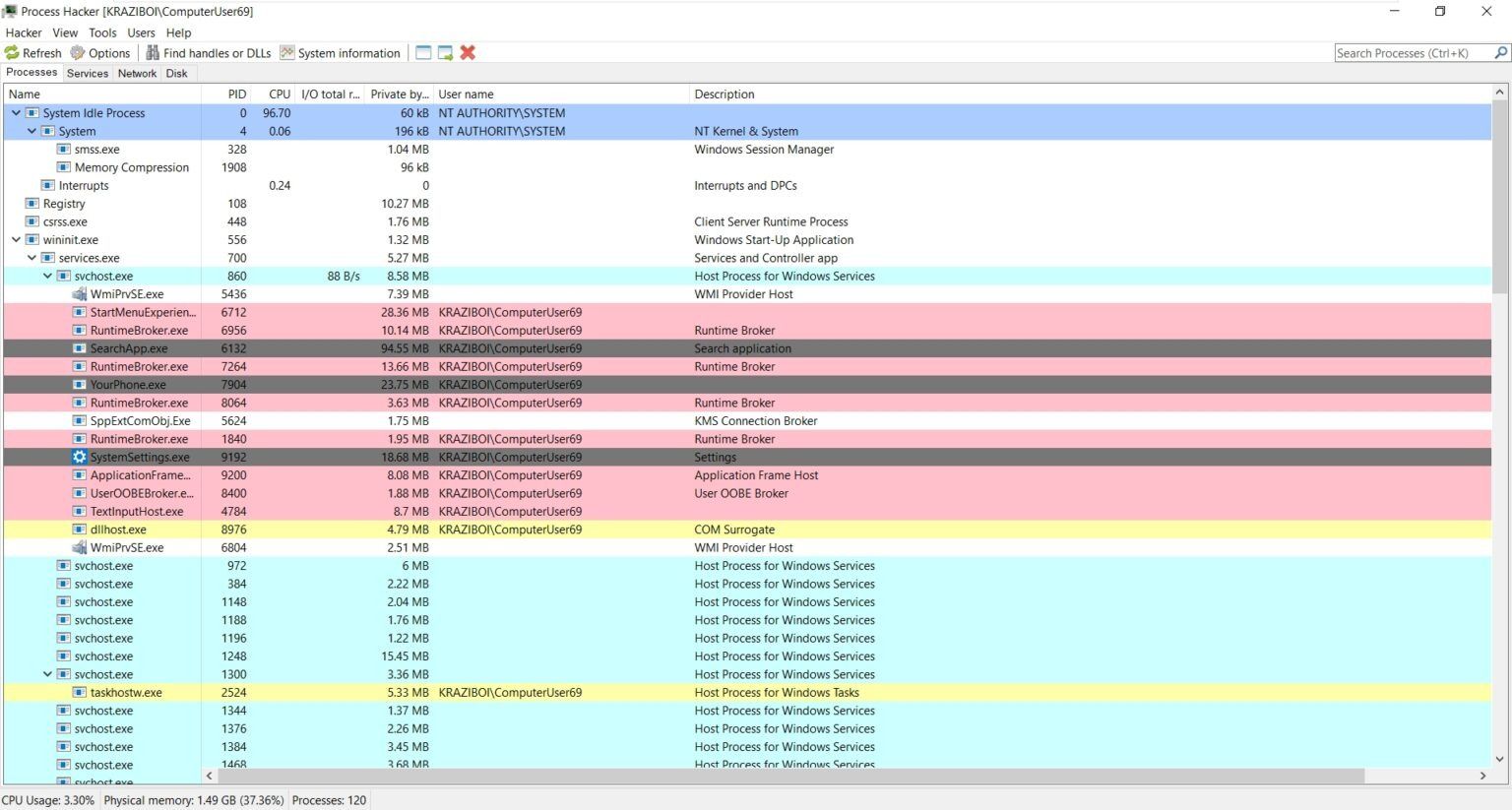 Process Hacker
Process Hacker
Tweaking around the registry can be risky so be extra cautious while using regedit.
So now that we have done static and dynamic analysis once we have some information in hand and have made some changes in background. Let’s do static analysis once again to observe any changes in application files. So we will come around situations where software is communicating with the server either to upload or download data, we’ll doing so means the credentials used for authentication might be stored somewhere.
 Registry Editor
Registry Editor
Now that we have enough findings we can begin exploiting each vulnerability in order to confirm them. We can for this instance try SQL injection, DLL Hijacking and use credentials and keys discovered earlier for our advantages.
That’s all folks ! We have gained some unique insights helping us handle a desktop application. Hope you learned something new. Just remember to be observant and alert and things will fall into place.
Good luck and happy hacking !
Share