Understanding Second-Order Attacks: A Comprehensive Guide
Bhautik Nasit
Aug 30, 2024
•
10 Min
Bhautik Nasit
Aug 30, 2024
•
10 Min
TABLE OF CONTENTS
Share
In the ever-evolving landscape of cybersecurity, attackers continuously devise sophisticated methods to exploit vulnerabilities. Among these, second-order attacks represent a nuanced and often overlooked threat. Unlike first-order attacks that target immediate system weaknesses, second-order attacks exploit deeper, often latent vulnerabilities that emerge over time. This blog delves into the intricacies of second-order attacks, exploring their mechanisms, real-world examples, impacts, and strategies for prevention and mitigation.
In cybersecurity, understanding the nature of threats is paramount to developing effective defenses. Second-order attacks are a category of cyber threats that capitalize on indirect vulnerabilities within a system. Unlike first-order attacks, which exploit immediate flaws, second-order attacks take advantage of weaknesses that manifest over time or through a series of interactions.
These attacks often require a deeper understanding of system behavior, user interactions, and the interplay between different components. As systems grow in complexity, the potential for second-order vulnerabilities increases, making them a critical focus for security professionals.
To grasp the concept of second-order attacks, it's essential to distinguish them from first-order attacks.
First-Order Attacks
Second-Order Attacks
Illustrative Example: Consider a web application that securely stores user passwords using hashing algorithms (a first-order security measure). A second-order attack might involve an attacker first compromising another part of the system to gain access to the hashed passwords and then using techniques like rainbow tables to reverse-engineer them, exploiting the initial security measure indirectly.
Understanding how second-order attacks operate is crucial for effective defense. These attacks typically follow a multi-step process, leveraging the interplay between different system components or user actions.
Stages of Second-Order Attacks
Key Characteristics
Common Vectors
To illustrate the concept of second-order attacks, let's examine some real-world scenarios where such attacks have been executed or could potentially occur.
Case study of authy - 2FA Bypass
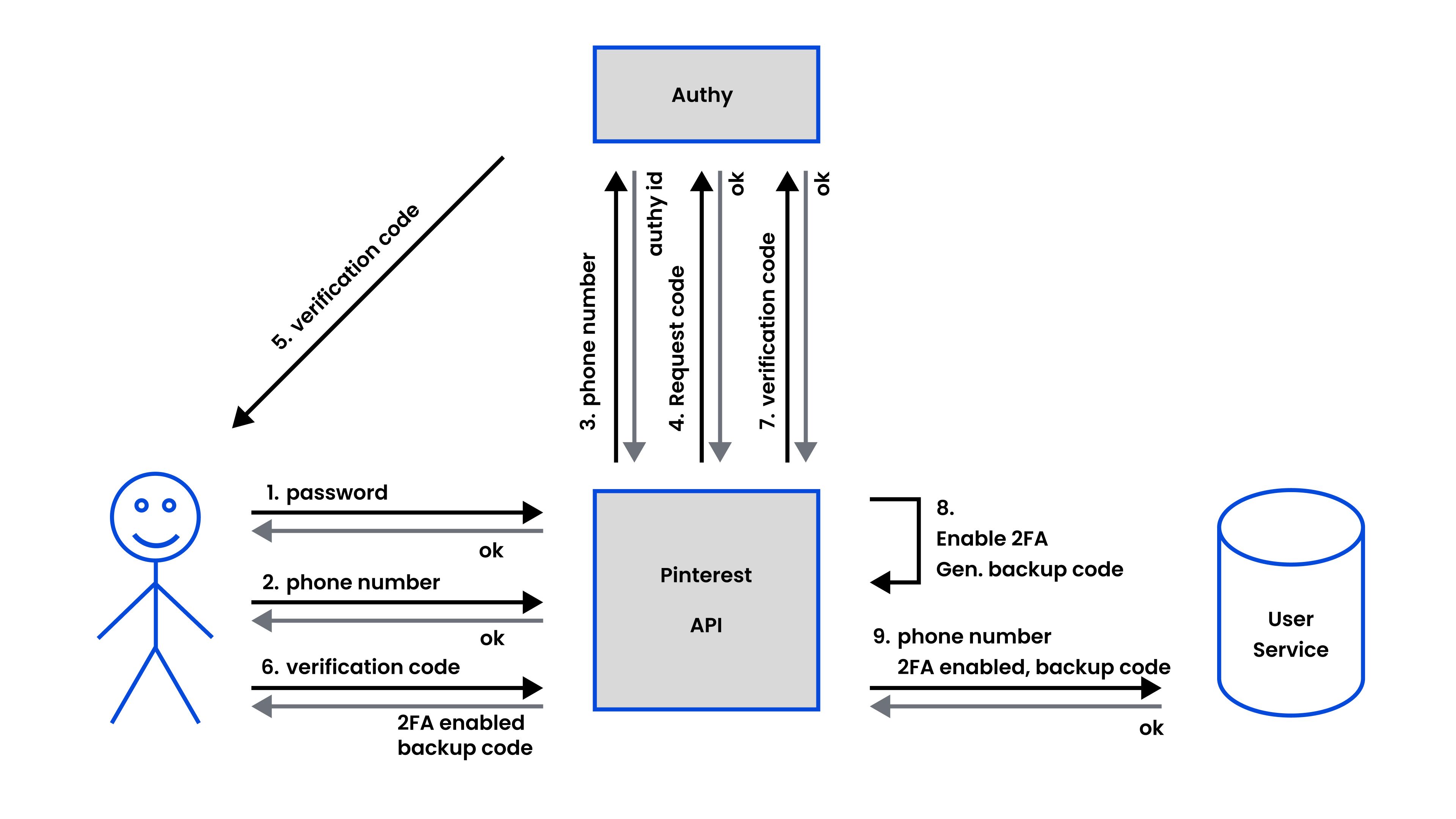
Let’s see what’s cooking here
There are two API calls:
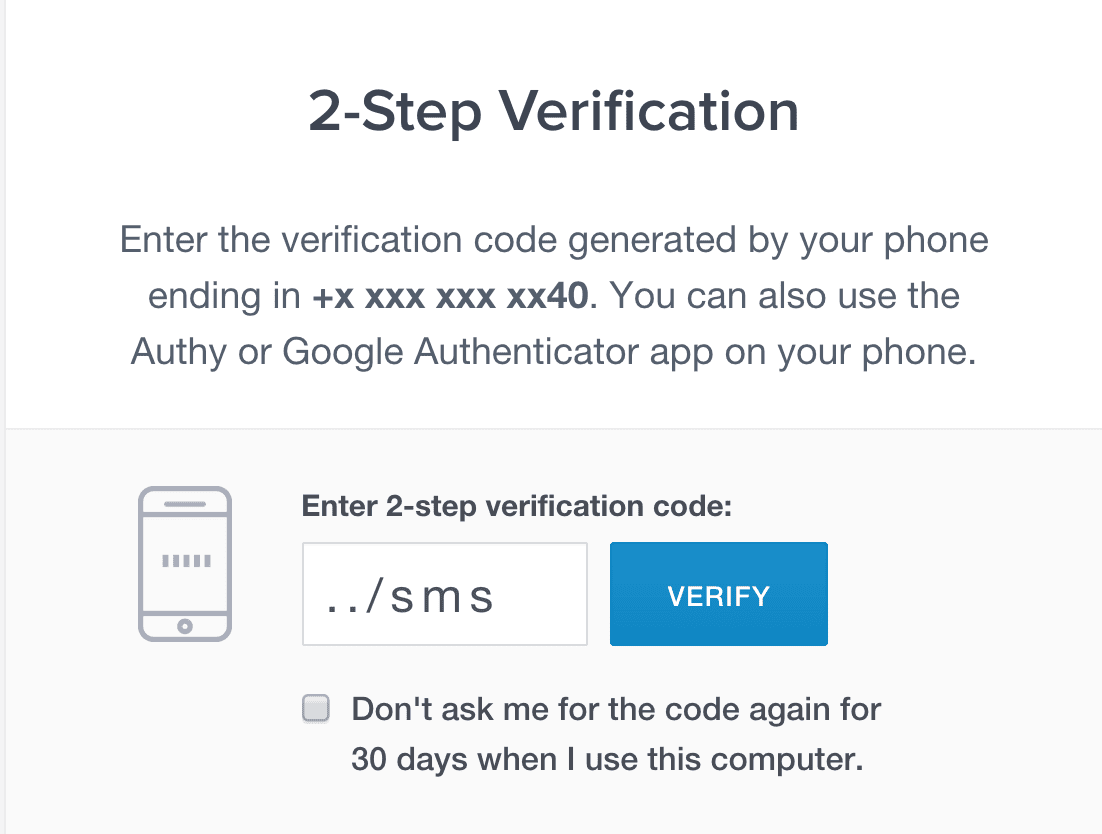
Yes, the attacker was able to bypass 2 factor authentication on any website using Authy with something as simple as ../sms in the token field!
Second order SQLi
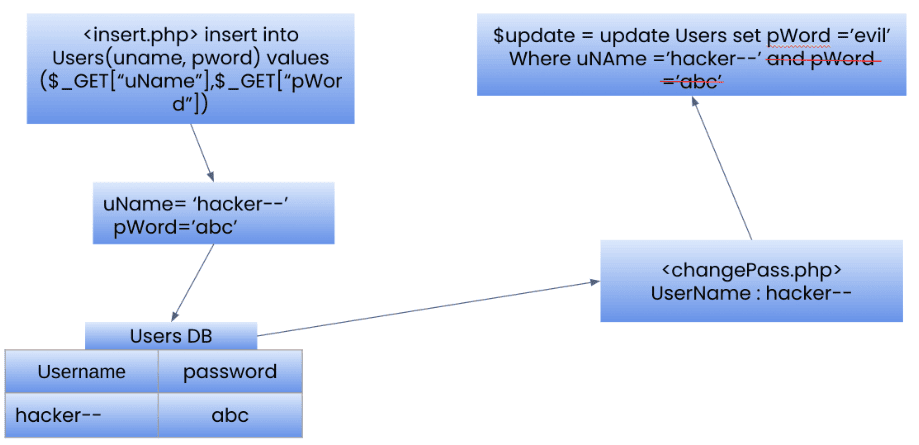
User Registration (insert.php)
Database Entry
Password Change Request (changePass.php)
Second-Order SQL Injection Exploitation
Result
XSS
You can also get the concept within the Stored XSS vulnerabilities, which is also defined by PortSwigger as second-order XSS, due to the payloads being executed on different pages rather than the exploited request’s response.
Scenario: Consider a web application that has two main components: a user registration form and a user profile display page.
In conclusion, second-order attacks represent a subtle yet dangerous security threat that can compromise systems long after initial user input is stored. Unlike first-order attacks, their delayed execution makes them harder to detect and mitigate. However, by adopting robust input validation, secure coding practices, and vigilant monitoring, organizations can defend against these insidious vulnerabilities. Regular security audits, developer training, and the principle of least privilege further enhance protection. Ultimately, a proactive and comprehensive approach to security is essential to safeguarding against the potentially severe impacts of second-order attacks.
Share