Unmasking Clickjacking: Stay Informed, Stay Protected
“Hey there, internet explorers! Have you ever clicked on something online and ended up somewhere you didn’t expect? You might have fallen victim to a sneaky trick called clickjacking. Don’t worry, we’re here to shed some light on this topic and help you to navigate the web safely. Let’s kick things off with a simple explanation of what clickjacking is and how you can protect yourself from it.”
Introduction to Clickjacking :
Clickjacking is a sneaky technique used by cybercriminals to trick you into clicking on something without realizing it. Imagine you’re browsing a website and you see a button that looks harmless, like “Play” or “Download.” But behind the scenes, there’s another hidden button or link that the attacker want you to click on, maybe to install malware or give away your personal info, Clickjacking, also known as a “UI redress attack”.
How Clickjacking Works?
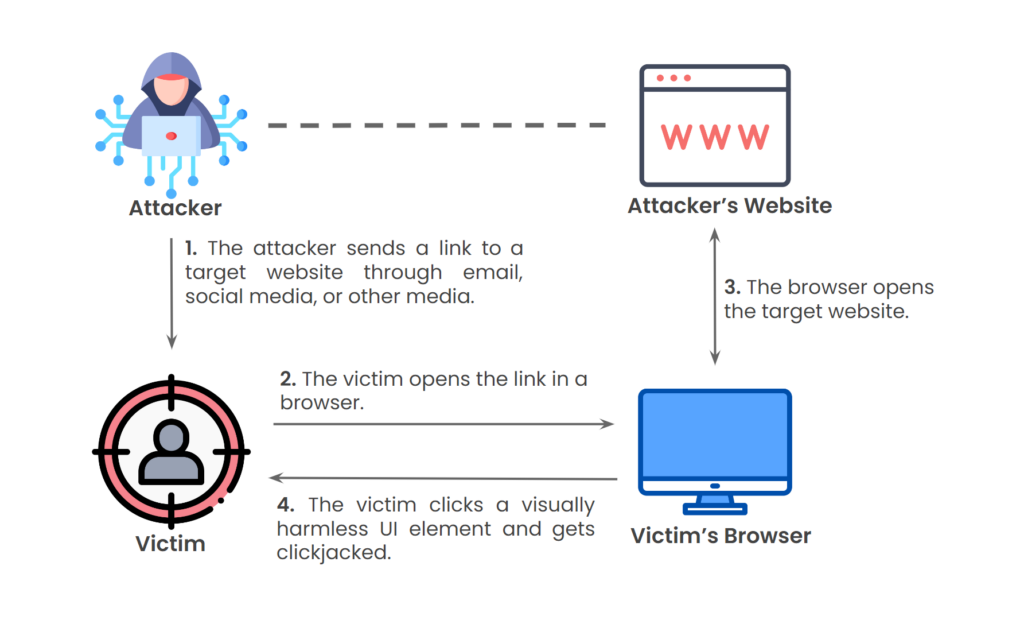
Clickjacking works by tricking you into clicking on something without knowing it. Here’s how they do it,
- Invisible Layers :- Imagine you’re looking at a webpage with buttons and links. But behind the scenes, the attacker put an invisible layer on top of the page, like an invisible sheet of glass. You can’t see it, but it’s there.
- Hiding the Trap :- Now, they put their own buttons or links on top of the invisible layer. These buttons look harmless, like “Play” or “Download,” but they’re actually traps. When you click on them, you’re actually clicking on something hidden under the page.
- Tricking Your Clicks :- When you click on what you see, you’re actually falling into the trap. It’s like thinking you’re pressing one button while actually pressing another. You are doing things that you didn’t mean to, like downloading malware or giving away your personal info.
- Sneaky Actions :- The attacker can make these hidden buttons do all types of sneaky things, like redirecting you to a malicious website, making you share sensitive information, or even taking control of your device.
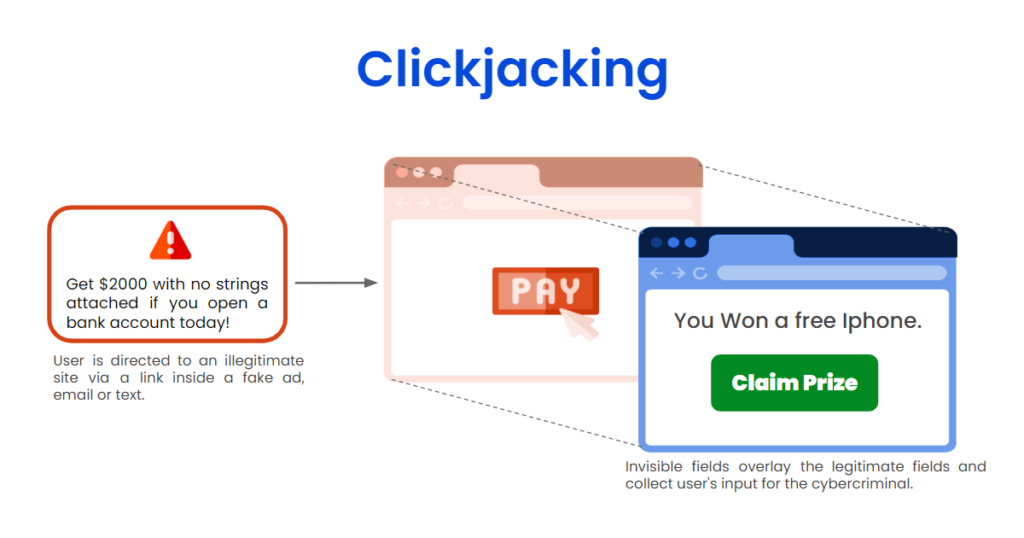
Example of Clickjacking :

In this example we can see two page, One page is with “Pay” button and another page with “Claim Prize” button, a page with pay button is created by an attacker which is actual page and another page which have claim prize is iframe, we can say iframe as a fake page. when user visit this site user can see only a page which have claim prize button, Claim button will show on top of the pay button, when user click on Claim Prize button user think user will win an iphone free but behind the claim prize button Pay button will Pressed and user will loss money.
How Users can be affected ?
Clickjacking attacks can do more than hijack cursor clicks. They can also be used to capture information, steal money, invade user privacy, and more, such as
- Steal login credentials (passwordless authentication can thwart this)
- Transfer money illegally
- Make unintended purchases
- Expose user location
- Activate a user’s microphone or camera
- Download malware
- Capture more social media followers (likejacking)
- Steal browser cookies (cookiejacking)
- Access files on the user’s hard drive (filejacking)
- Promoting the attacker’s content on a social network
- Tricking the user into submitting sensitive credential information
- Performing a privileged action on behalf of the user (Create or Delete accounts, etc.)
Why clickjacking is a significant threat to users and organizations?
- Clickjacking can be used with other attacks to do really bad things, like stealing money, changing account settings, or accessing private data without permission,
- Organizations can suffer damage to their reputation and finances if their website is used for clickjacking. Customers lose trust, and companies might face legal trouble and lose money.
- Clickjacking is hard to detect, Antivirus software might not catch it, making it tough for users and organizations to protect themselves.
- Clickjacking can happen on computers, phones, and even smart devices. This means anyone can be a target, making the problem widespread and serious.
Real-World Examples :
- Fake Like Buttons on Facebook
Cybercriminals created fake like buttons on Facebook. When users clicked on what looked like harmless buttons, they were actually liking or sharing malicious content without knowing it.
Impact :- This led to the spread of scams and malware on Facebook, affecting many users. People’s profiles were used to promote scams or spread harmful links, damaging their online reputation.
- Tricky Videos on YouTube
Attackers posted videos on YouTube with invisible buttons hidden on top. When users watched these videos and clicked anywhere on the screen, they were actually clicking on those hidden buttons.
Impact :- Clicking on these hidden buttons could lead users to malicious websites or prompt them to download malware. It made people cautious about clicking on videos they weren’t sure about.
- Bogus Contests and Offers
Scammers created fake contests or offers on websites. When users tried to participate or claim a prize, they were actually clicking on hidden buttons that redirected them to fraudulent websites or prompted them to reveal personal information.
Impact :- Many people fell victim to these scams, leading to financial losses or identity theft. It showed how easily people could be tricked into clicking on things that seemed too good to be true.
- Fake Banking Pages
Attackers created fake login pages for banking websites. They used clickjacking to overlay these fake pages on top of legitimate ones. When users entered their login credentials, they were actually giving them to the attackers.
Impact :- This resulted in financial losses for unsuspecting users whose accounts were compromised. It highlighted the importance of verifying the authenticity of websites before entering sensitive information.
Mitigation :
- X-Frame-Options Header :- Websites can tell browsers not to let their pages be shown in hidden frames, stopping clickjacking.
- Content Security Policy (CSP) :- Websites control what content they can load. With strict rules, they can stop bad content from being loaded, reducing clickjacking risks.
- Frame-busting Script :- Websites use code that breaks out of hidden frames, ensuring their content is only shown in regular windows.
- User Awareness Training :- Teaching people about clickjacking helps them spot suspicious links and buttons, staying safe online.
- Browser Security Features :- Up-to-date browsers block pop-ups and protect against clickjacking.
- Regular Security Audits :- Website owners check for vulnerabilities that could be used in clickjacking attacks, fixing any issues to keep users safe.
- Two-Factor Authentication (2FA) :- Adding an extra login step makes it harder for attackers to access accounts, even if they trick users with clickjacking.
Here we are ending of this blog but “Remember, this knowledge is your best defense against clickjacking. Stay vigilant, stay informed, and keep clicking wisely. Together, we can make the web a safer place for all. Happy surfing, and may your clicks always lead you exactly where you intend them to go.”
“Stay safe online, friends. Keep your clicks sharp and your instincts sharper. Until next time, happy browsing!”