Building SOC from Basic to Advance+
Harsh Radadiya
Feb 3, 2025
•
5 Min
Harsh Radadiya
Feb 3, 2025
•
5 Min
In today’s fast-evolving digital world and cyber criminals powered by AI, log monitoring is no longer a luxury it’s a necessity. This is where SOC (Security Operations Center) plays a critical role to pro-actively safeguard businesses from cyber threats.
SOC acts as the command center for proactively defending your IT Infrastructure by:
Collecting logs from various sources. (i.e. Firewalls, WAFs, CloudWatch, AD, Sys Logs, etc.)
Setting correlations between logs to track the attackers movements in your infrastructure.
Investigating incidents through IOCs. (Enriching your logs with SOAR)
Helping businesses to continuous monitor, audit configurations of IT assets, detecting anomalies, and responding to potential security threats.
Our guide help you understand the different phases of maturity and how CISOs and CIOs shall invest in building or outsourcing the security operations center process. Also, answers questions that may have arise from our previous research on "Cost of Data Breach in 2025" a forecast from our analytics and observation that correlates with IBM's Report summarizing 2024.
The guide explains four maturity levels and cost associated to SOC ranging from Basic to Advanced+, allowing companies to select a security framework based on their budget, resources availability and time constraints. Each plan outlines the difference in cost, capabilities, manual & automated efforts between SOC Team and Automation, helping businesses determine their current stage and the future plans.
Building a strong SOC requires a strategic approach, progressing from basic security measures to advanced analytics driven threat intelligence. Each SOC maturity stage enhances an organization's ability to detect, respond, and mitigate cyber threats more efficiently, ensuring comprehensive protection at every level.
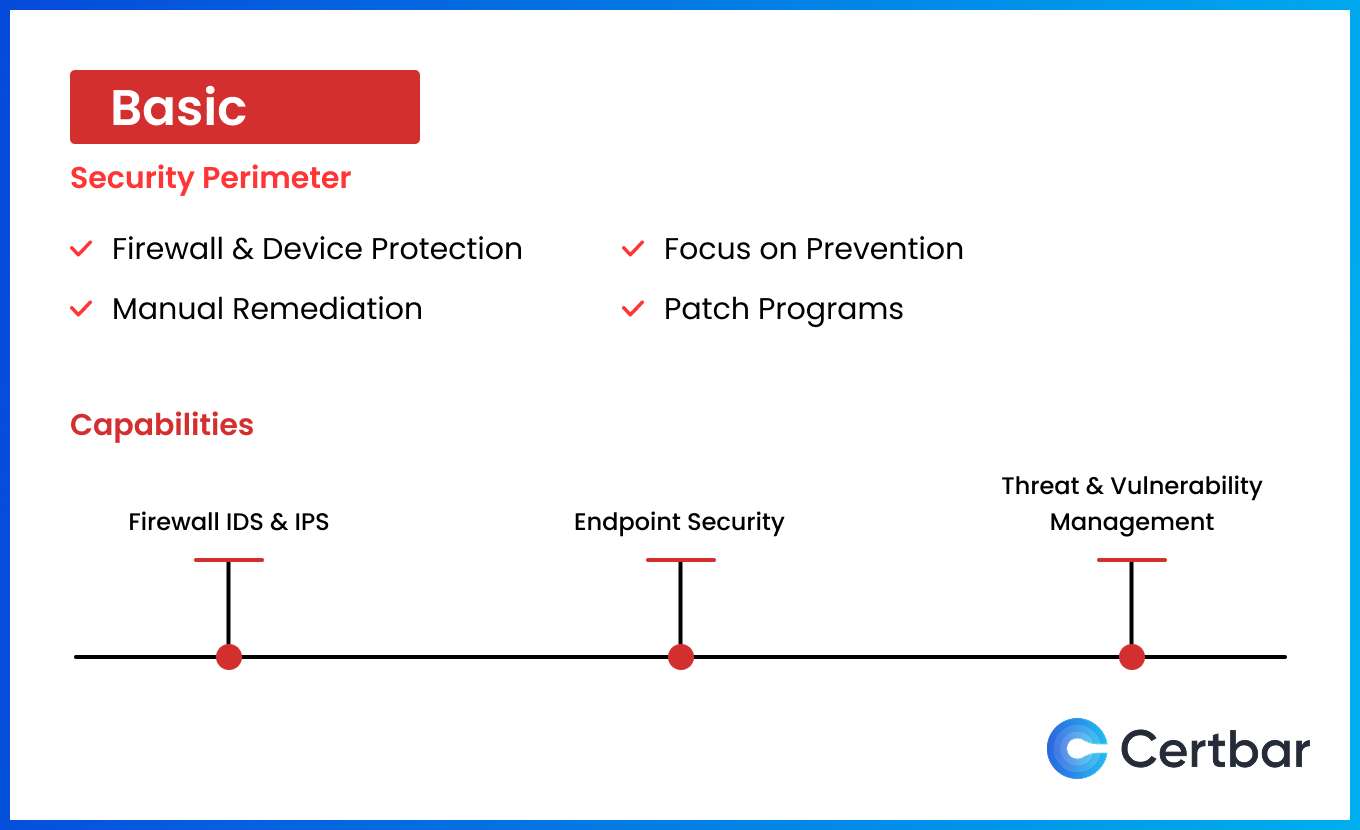
The security perimeter serves as the first and most crucial level of defense against cyber threats. Though these perimeters are capable to provide incident and event logs for unauthorized access and filter malicious traffic before it reaches internal systems, they follow different structures and mechanisms to audit them manually. Monitoring these logs manually and manual remediation adds a burden on your team, exhausting IT teams resources, time and energy to detect and resolve security gaps before they escalate.
In the initial stages when you have just started investing in cybersecurity it is perfectly normal to manually monitor logs and take appropriate actions to mitigate the risk. As an organization one should always choose the security perimeter with adequate notification to shorten the response gap. We recommend investing in the following when your are at level 1:
Contact us for a free consultation
SOC services also affect workload distribution between SOC team and automations providers with different products and your level of SOC model. The chart below illustrates how the proportion of SOC team work increases with higher investment stages:
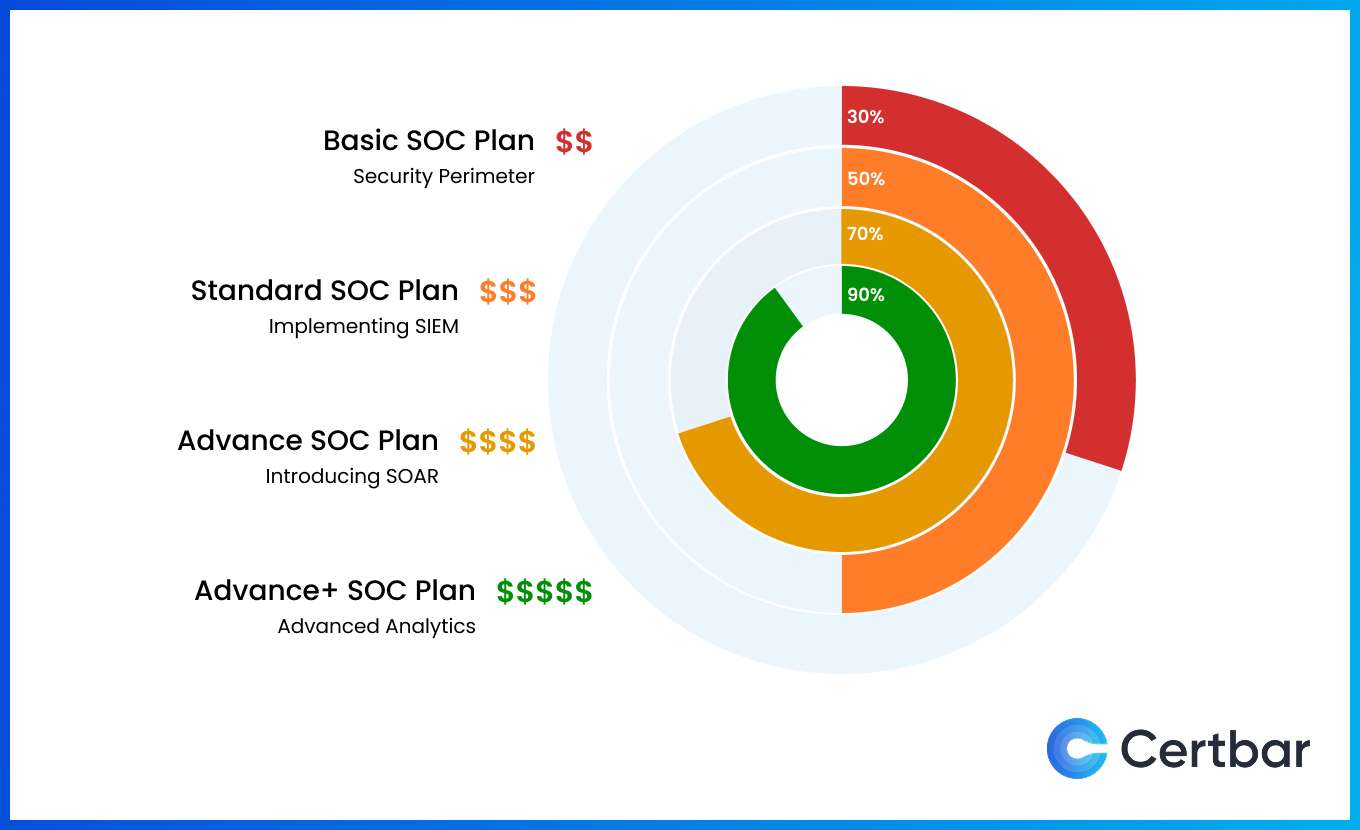
Standard SOC Plan ($$$) – 50% Automation, 50% Manual Efforts: The SOC team redirects all logs towards SIEM solution which manages, organizes, prioritizes & audit logs with given rules & decoders with in-built capabilities and prevents threats through manual configurations. Meanwhile, SOC team's task is searching logs for anomalies, performs correlation analysis, and creates custom rules/decoders. Also SOC team is responsible to assists in manually configuring security tools, preventing threats, blocking threats as identified, raising tickets, and supporting SOC in rule implementation. This plan is best suited for mid-sized companies that need structured log management and proactive threat detection while still playing an active role in security management.
Advanced SOC Plan ($$$$) – 70% Automation, 30% Manual Efforts: The SOC team automates SIEM services, configures SOAR, creates dashboards & KPIs, sends real-time incident reports via email, and develops standard & customized playbooks. Instead of creating rules & decoders the SOC team will be focused on combating actual and creditable threats. 70% of the rules/decoders are already created in this platforms to match a variety of security perimeters and the SOC team doesn't have to invest time and energy on improving visibility. The SOAR platform will help the SOC team in investigating if an attack is a false positive or not and assess internal threats. This plan is best for enterprises needing automated security monitoring while maintaining oversight on internal security incidents.
This progression from basic to fully managed SOC services reflects how organizations can scale their cybersecurity efforts as their budgets and operational complexities grow. By outsourcing more responsibilities to SOC providers, businesses can reduce in-house workload, improve response times, and leverage the expertise of dedicated cybersecurity professionals.
Selecting the right SOC service involves aligning organizational needs, resources, and security objectives. Follow this steps to make an informed decision:
Evaluate Company Needs: Begin by identifying your organization’s security gaps, compliance requirements, and budget constraints. This helps pinpoint the specific services required, whether it’s perimeter security, SIEM services, or advanced threat intelligence.
Match SOC Services: Align your identified needs with a suitable SOC maturity level and service type. For instance, small businesses may benefit from basic monitoring, while larger enterprises might require fully managed SOC services with real-time threat resolution.
Consider ROI: Focus on long-term benefits such as improved incident response times, enhanced threat prevention, and overall cost-effectiveness. Investing in the right SOC service ensures a strong return on investment by reducing risks and minimizing potential damages from cyber threats.
By following these steps, companies can achieve a cost-effective and comprehensive security strategy that aligns with their size and risk profile.
Selecting the right SOC plan is a strategic decision that depends on a company’s security needs, budget, and available resources. From basic monitoring to fully managed SOC services, each level provides a structured approach to strengthening cybersecurity. As threats evolve, businesses can scale their security operations to ensure continuous protection while maintaining operational efficiency.
A well-planned SOC ensures that internal teams remain focused on core business functions without being overwhelmed by security tasks. By leveraging outsourced expertise, companies can enhance threat detection, response times, and overall security posture. Choosing the right SOC model allows businesses to stay ahead of cyber threats, ensuring long-term resilience and growth.
As a leading cybersecurity provider, we are here to help you secure your organization and stay ahead of emerging threats. To learn more about how we can protect your business, contact us today.
Share
 Mulayam Yadav
Mulayam Yadav