SSL Pinning Bypass
Sukesh Goud
Dec 22, 2022
•
3 Min
Sukesh Goud
Dec 22, 2022
•
3 Min
TABLE OF CONTENTS
Share
Secure Socket Layer (SSL) and Transport Layer Security (TLS) ensure encrypted
Communication over the internet – specified as HTTPS. The security factors of SSL are based on the security certificates’ “Chain of Trust.” When a sender sent a message, the client checks the Server’s SSL certificate to confirm whether the certificate is issued by Trusted CA.
Certificate pinning forces your client app to validate the server’s certificate against a known copy. After pinning your server’s certificate inside your client app, your client should check the basic validity of the cert from the list above, as well as verify that the server’s certificate matches the pinned certificate.
SSL pinning bypass is a major step that needs to be done when we even start the dynamic analysis of HTTP requests for most of the mobile application nowadays as organizations are more concern about data privacy and secure transfer of data over the network from threads like Man-in-The-Middle (MiTM) attacks.
Frida is a framework that injects scripts to native apps to manipulate application’s logic in runtime which is a more dynamic approach for pentesting mobile applications.
python -m pip install Fridapython -m pip install objectionpython -m pip install frida-toolspip install Fridapip install objectionpip install frida-toolsapt install adbConnect device to adb:
If you do not enable- first goto settings >> Developer options and enable debugging mode in device so that adb can communicate with the device.

Install SSl pinning apk in device
Step:1 Download apk – go to directory open terminaladb install -r twitter_9.69.0_androidapksbox.apk
Step:2 Twitter installed in emulator
Step:3 Open the application and Observe that the application is a SSL Pinning

Frida Server Setup:
Download latest frida server:
Step:1 Click on this URL
frida-server-12.4.7-android-x86
frida-server-12.4.7-android-x86_64.xz
Step:2 Now we need to push our frida-server file into the device. Extract and Copy “frida-server-12.4.7-android-x86” file in adb folder rename file as “frida-server”
Step:3 following command → adb push frida-server /data/local/tmp/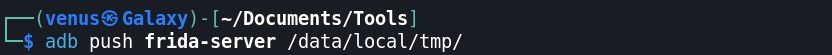
Step:4 Pushed this /data/local/tmp
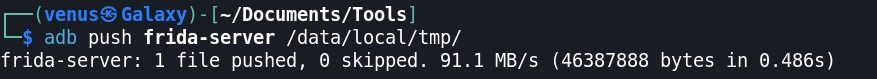
Step:5 Give permissions to frida-server → adb shell chmod 777 /data/local/tmp/frida-server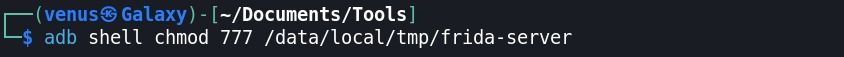
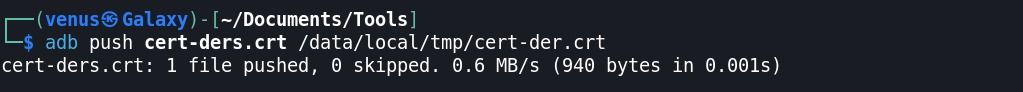
Step:6 Push the certificate into the device and into the same location as the frida-server, name it cert-der.crt
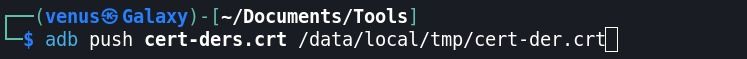
Step:7 Pushed this /data/local/tmp
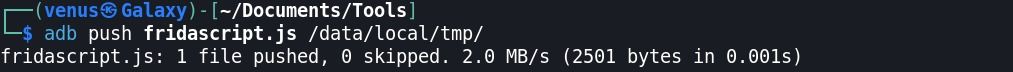
Step:8 Click on this URL, You can save this code as fridascript.js in the same folder as adb → adb push fridascript.js /data/local/tmp/ 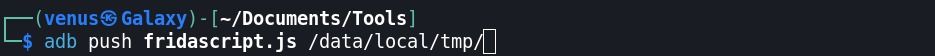
Step:9 Pushed this /data/local/tmp
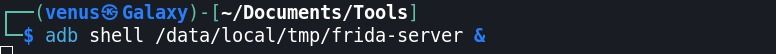
Step:10 Check and run frida server in device → adb shell /data/local/tmp/frida-server &
Step:11 Following command → frida-ps -Uai 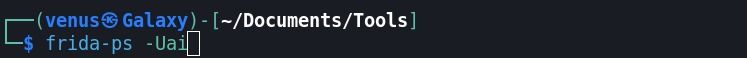
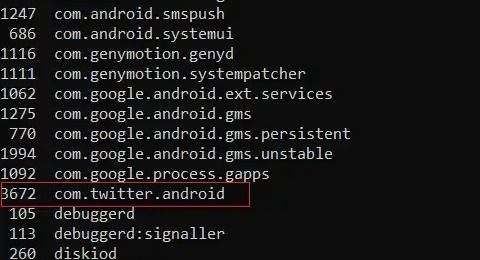
Step:12 Find your application’s package name
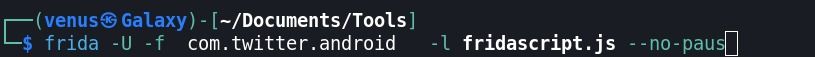
Step:13 Following command → frida -U -f com.twitter.android -l fridascript.js –no-paus
Step:14 Your command to inject the fridascript.js script into the native application
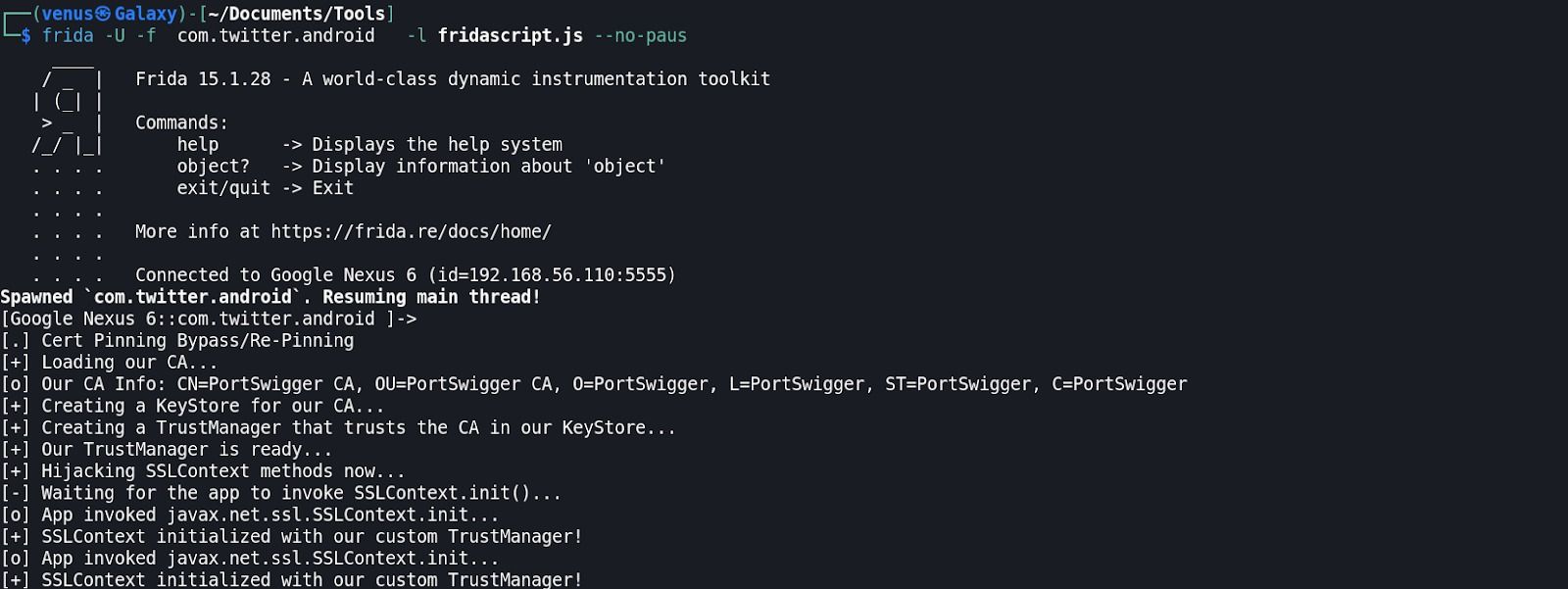
Step:15 BOOM Bypassed!!. We are intercepting traffic into BurpSuite
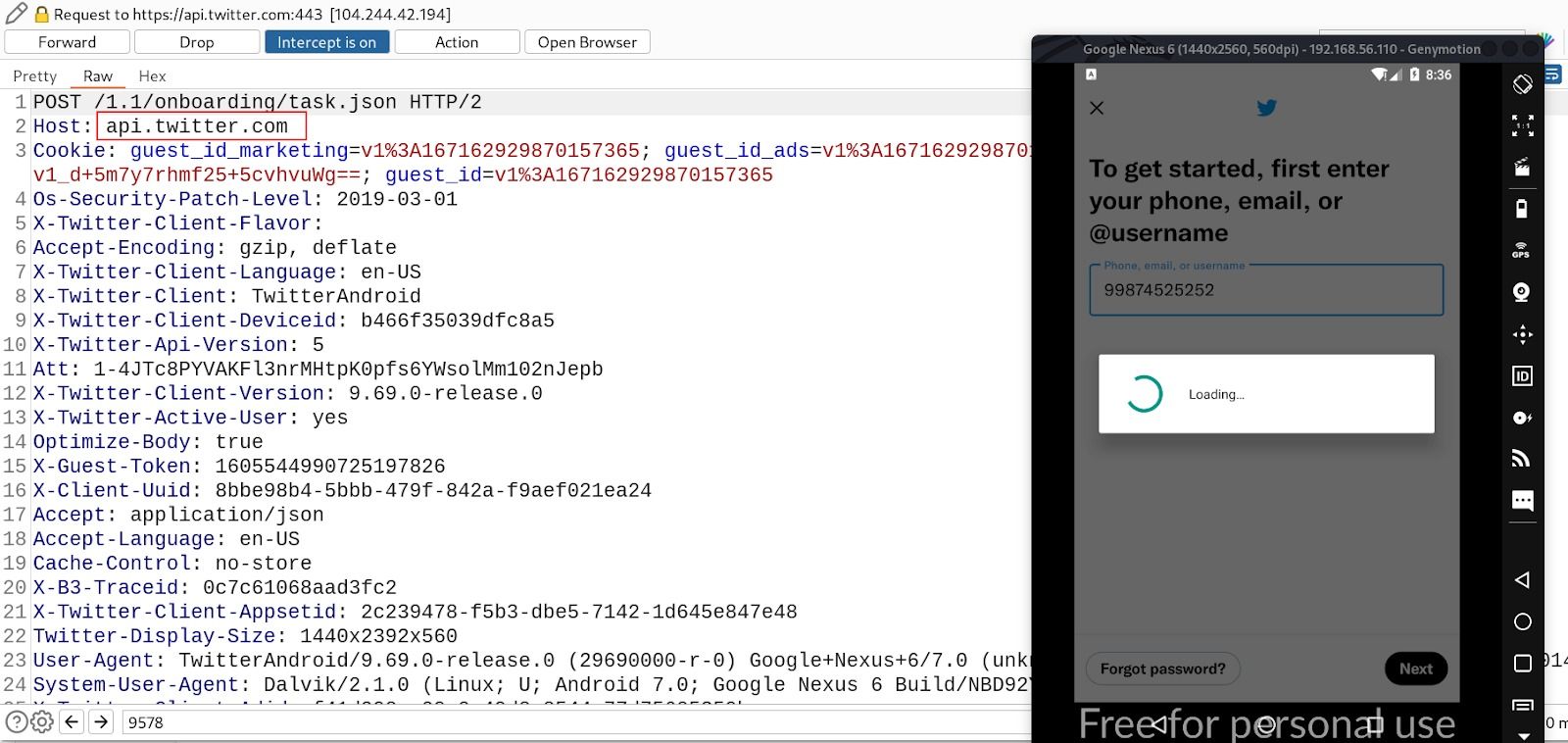
That’s all for this blog, I hope you enjoyed reading this. In future, I will right one more blog that will include some other techniques.
Click here to see the reference
Share