Flex Your SOC Muscles with SIEM & SOAR
Harsh Radadiya
Mar 24, 2025
•
4 Min
Harsh Radadiya
Mar 24, 2025
•
4 Min
In today’s rapidly evolving threat landscape, organizations must be proactive in defending against cyberattacks. With security incidents growing in complexity and frequency, relying solely on traditional security measures is no longer sufficient. Security teams are often overwhelmed with massive volumes of alerts, struggling to distinguish real threats from noise. This is where Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) come into play, acting as the backbone of modern security operations. By integrating SIEM’s powerful analytics with SOAR’s automated response capabilities, businesses can build a resilient security posture, minimizing threats before they escalate into full-blown breaches.
At Certbar, we believe that cybersecurity is like building muscle—the more you train and optimize your security operations, the stronger your defense becomes. SIEM helps detect threats with real-time visibility, while SOAR automates incident response, reducing the burden on security teams and ensuring rapid mitigation. In this article, we’ll explore how combining these two technologies can revolutionize security operations, enhance threat intelligence, and enable organizations to respond to cyber threats with agility and precision.
For a deeper dive into building a robust security framework, be sure to check out my previous article on the SOC Maturity Model.
Ready to flex your SOC muscles? Let’s dive in!
Organizations face evolving cyber threats, expanding attack surfaces, and overwhelming security alerts, demanding a proactive, automated approach. SIEM and SOAR form the backbone of modern SOCs, working like a dumbbell with two key pillars. SIEM ensures security visibility by collecting and analyzing data, while SOAR automates responses, reducing analyst fatigue and improving efficiency. Together, they enhance detection, streamline operations, and accelerate threat mitigation.
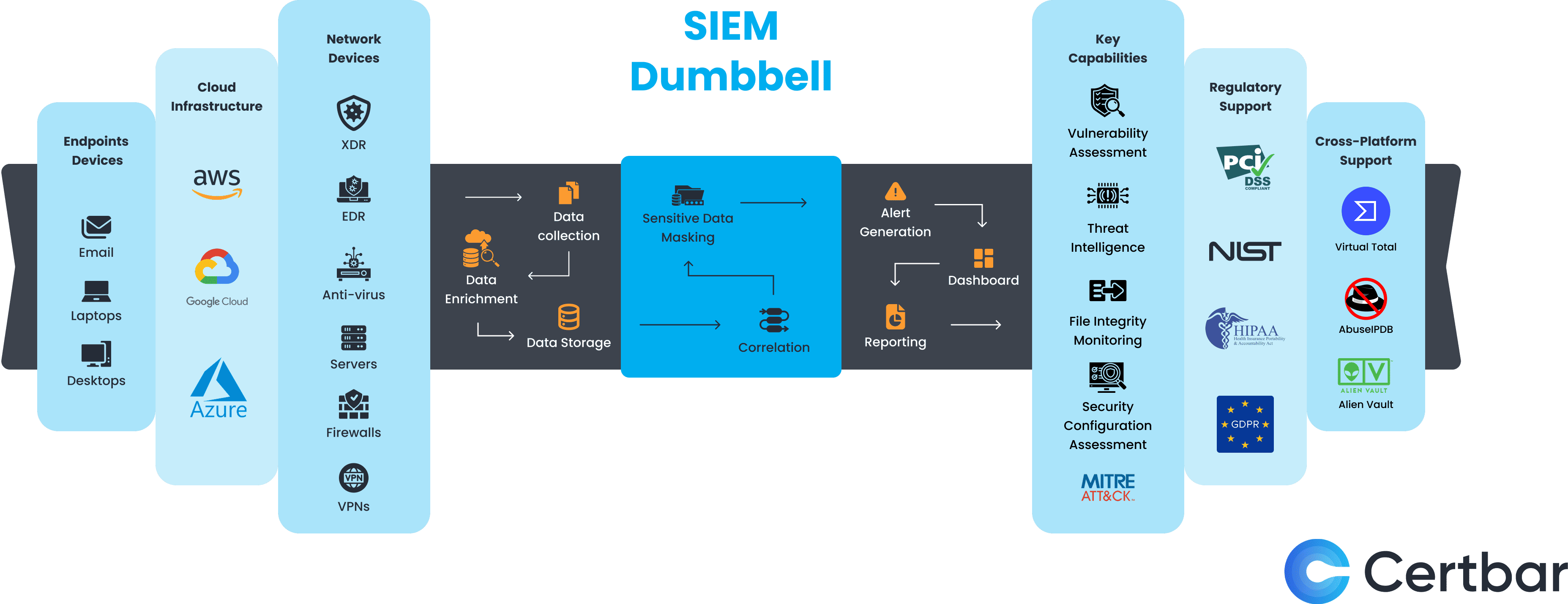
The first part of the cyber defense dumbbell is SIEM, which is responsible for collecting security data from multiple sources, analyzing it, and generating alerts based on identified threats. It provides security teams with real-time visibility into potential risks and enables better decision-making through correlation and reporting.
SIEM gathers data from three critical sources:
Once data is collected, SIEM follows a structured workflow:
Beyond alerting, SIEM provides a comprehensive dashboard, reporting capabilities, and compliance alignment with frameworks such as PCI DSS, HIPAA, NIST, GDPR, and MITRE ATT&CK, ensuring organizations remain compliant with regulatory standards.
Contact us for a free consultation.
In today’s rapidly evolving cyber threat landscape, organizations need more than just detection and alerting they need full visibility and actionable intelligence. At Certbar, we don’t just rely on traditional security monitoring; we go beyond by implementing deep request inspection, sensitive data masking, and intelligent payload handling to ensure enhanced security without compromising operational efficiency.
A strong Security Operations Center (SOC) isn’t just reactive—it’s proactive, adaptable, and precise. Our capabilities are designed to provide detailed attack visibility, automated security enforcement, and intelligent data handling, ensuring that our SOC operates at maximum efficiency while safeguarding sensitive data.
One of the key limitations in traditional SIEM deployments is incomplete log capture. Many security tools only collect basic metadata, such as source IPs, timestamps, and HTTP headers, but fail to capture the full request and response body leaving security analysts with an incomplete picture of security incidents.
At Certbar, we address this challenge by capturing the full body of GET and POST requests and responses, providing security teams with detailed insights into attack payloads, authentication attempts, and injected malicious scripts.
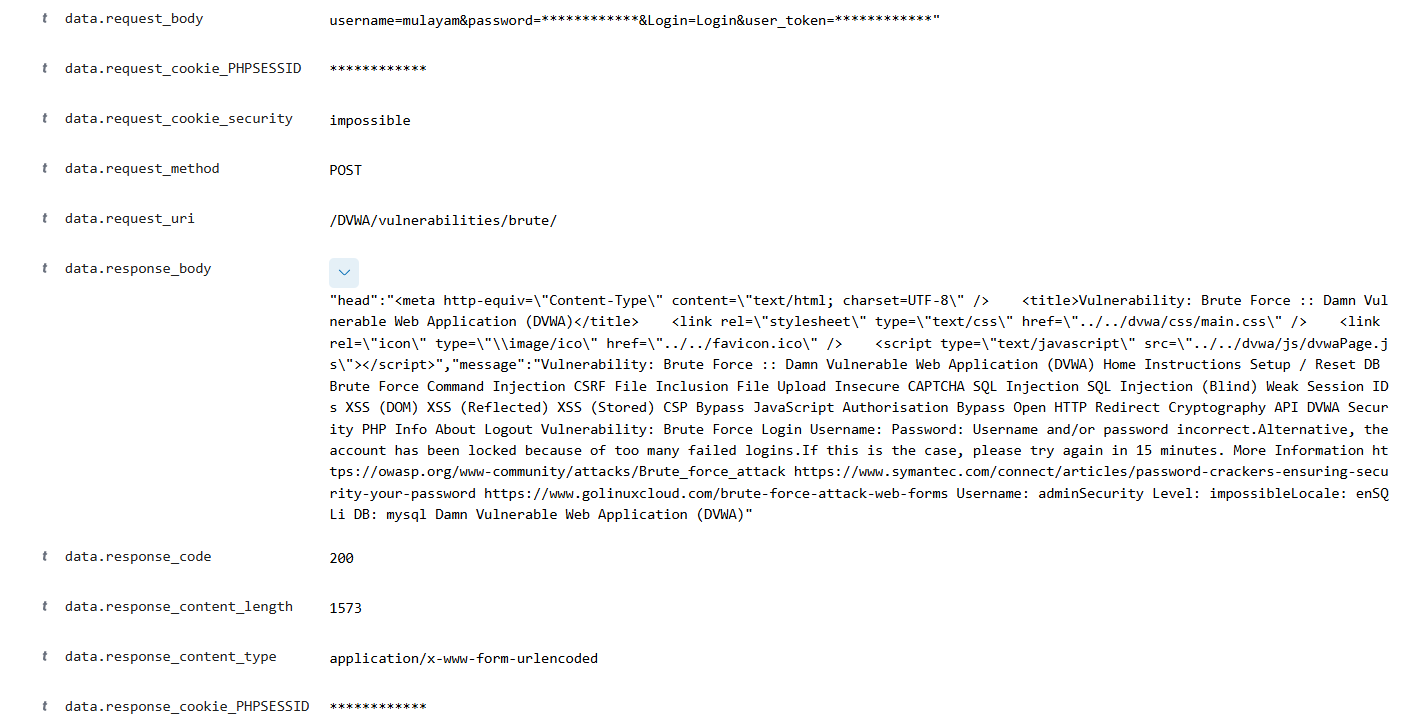
By capturing every request and response, our SOC ensures that attackers cannot hide their activity, giving security analysts full visibility into threats in real time.
As cyber threats grow more sophisticated, businesses must shift from reactive security to intelligent, automated defense strategies. SIEM and SOAR are no longer just tools for log collection and incident response; they are essential components of a resilient, business-driven security strategy. By integrating automation, AI, and machine learning, organizations can enhance threat detection, accelerate response times, and minimize operational disruptions.
Security teams face alert overload, complex attack vectors, and compliance challenges. AI-powered SIEM filters false positives, while SOAR automates response workflows, ensuring rapid containment of threats. This combination reduces manual workload, enhances SOC efficiency, and allows security teams to focus on proactive threat hunting and risk mitigation.
To stay ahead, organizations must align SIEM & SOAR with business objectives, regulatory requirements, and operational goals. A security strategy built on automation, intelligence, and seamless orchestration not only strengthens defenses but also drives efficiency and scalability. Those who embrace AI-driven security automation today will lead the cybersecurity landscape of tomorrow.
Organizations can no longer rely on manual processes and disconnected security tools to defend against modern threats. SIEM and SOAR together create a unified security framework that enhances threat detection, automated response, and ensures regulatory compliance. By integrating real-time visibility and automated orchestration, businesses can significantly reduce incident response times and minimize alert fatigue.
SIEM provides the insights needed to detect and prioritize threats, while SOAR ensures those threats are mitigated swiftly and effectively. This strategic combination helps organizations streamline security workflows, optimize SOC efficiency, and strengthen overall cyber resilience. Adopting SIEM and SOAR is essential for building a proactive, intelligent, and well-orchestrated security strategy.
For expert guidance on implementing SIEM & SOAR to strengthen your security operations, contact us today.
Share

 Harsh Radadiya
Harsh Radadiya
 Mulayam Yadav
Mulayam Yadav