Security Risk Management Pitfalls
Lata Parmar
Sep 23, 2025
•
8 Min
Lata Parmar
Sep 23, 2025
•
8 Min
In an era where digital transformation is accelerating, most organizations claim to be secure mainly because they’ve passed compliance audits. But ticking boxes isn’t the same as managing real-world risks.
For many early-stage SaaS companies and compliance-driven enterprises, security risk management is reduced to documentation, policies, and once-a-year activities like penetration testing. Although these measures are crucial, they can sometimes lead to a misleading feeling of safety.
Compliance frameworks such as SOC 2, ISO 27001, or HIPAA provide structure, but they do not protect organizations from emerging threats or human error. As a result, security programs often lack depth, context, and resilience.
This article explores the pitfalls organizations face in security risk management, focusing on the over-reliance on compliance as a security strategy, the lack of proactive operational measures, and the dilemmas CISOs encounter while aligning business priorities with real-world risks. It also highlights how top-performing organizations distinguish themselves through a more proactive, balanced, and business-aligned approach to security.
Organizations often fall into one of two extremes when it comes to security risk management and both carry serious consequences. Mature, compliance-focused companies may check all the boxes for regulatory frameworks yet miss the bigger picture by treating compliance as a destination rather than a continuous journey. Meanwhile, fast-growing SaaS startups frequently sideline security in Favor of rapid scaling, inadvertently building on insecure foundations. This section dissects the common but critical missteps each type of organization makes revealing how misplaced priorities, whether rooted in overconfidence or underinvestment, can quietly erode an organization’s security posture.
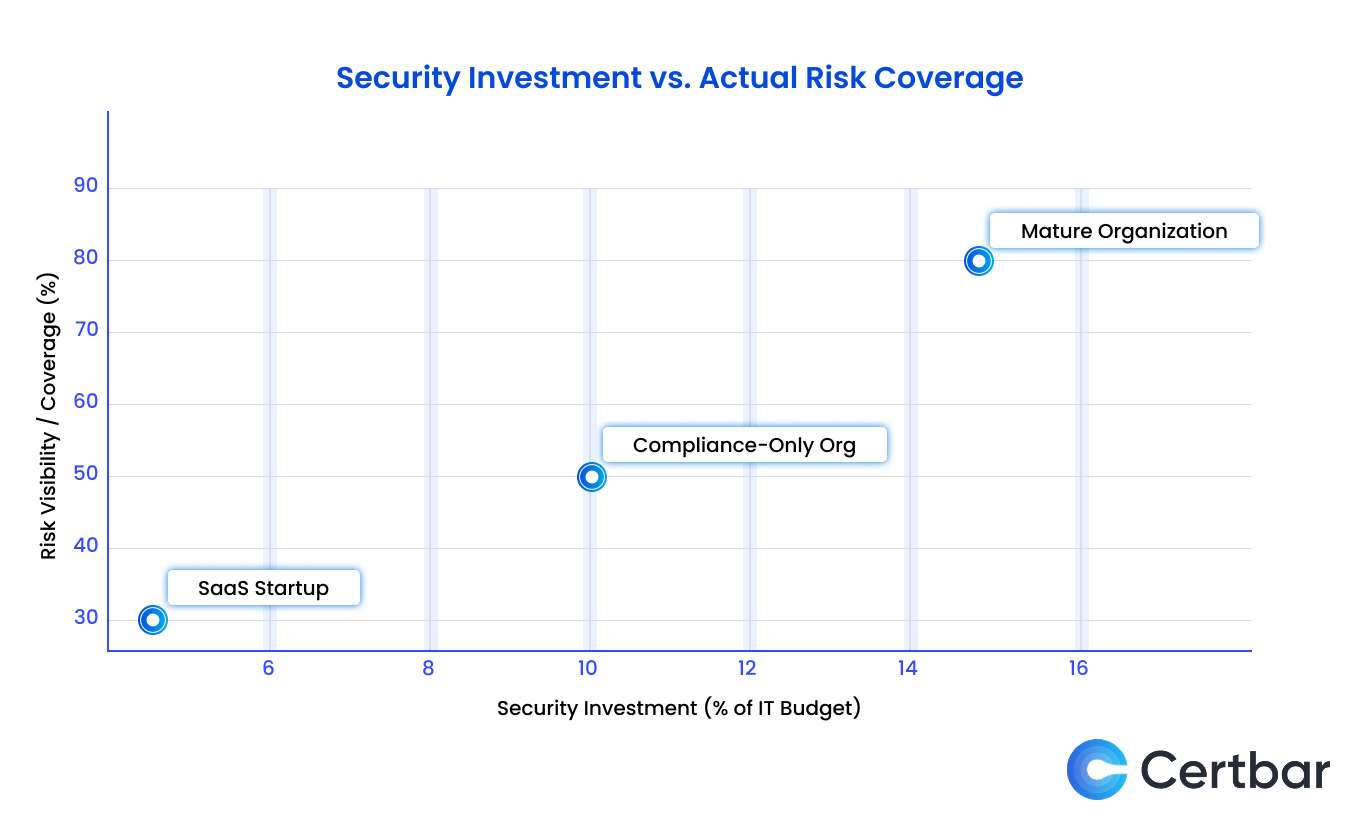
The “Security Investment vs. Actual Risk Coverage” bubble chart illustrates the correlation between an organization’s cybersecurity spending and its actual risk visibility, segmented by maturity levels. The chart shows that higher security investment leads to better risk coverage. SaaS startups invest around 5% of their IT budget and get 30% coverage. Compliance focused organizations invest 10% for about 50% coverage. Mature organizations invest more than 15%, achieving 80% coverage. It highlights that strategic, risk-based investment is key to improving security.
In many established organizations, especially those operating in regulated industries, security efforts are often anchored in achieving and maintaining compliance. While this is an important step in the right direction, relying solely on compliance frameworks as a security strategy introduces serious limitations. These companies may appear secure on paper but are often exposed to real-world risks that compliance audits don’t catch. Below are the most common pitfalls observed in such environments:
Many organizations equate passing security audits such as SOC 2, ISO 27001, or HIPAA with being secure. Once the audit report arrives with a green light, security conversations fade until the next cycle. This approach views compliance as a one-time task instead of an ongoing effort. However, real attackers don’t care about certifications they exploit live, unmonitored systems, poorly configured endpoints, and human behaviour. Compliance provides a snapshot of minimal controls; true security requires adapting to threats that evolve far beyond what’s covered in audit criteria.
Early-stage SaaS startups are built on the principles of speed, agility, and innovation. In their pursuit to capture market share and validate product-market fit, these companies often deprioritize security not out of negligence, but out of urgency. However, this rush to scale can lead to avoidable security oversights that, if left unaddressed, can erode customer trust, invite regulatory scrutiny, and undermine business continuity.
In the startup world, speed is currency. Founders and engineering teams are laser-focused on building MVPs, shipping features, and delighting early adopters. While this mindset accelerates growth, it often pushes security down the priority list. Security becomes a “post-launch” concern addressed only after a breach, investor pushback, or customer inquiry. This results in fragile systems with minimal security controls, technical debt that compounds over time, and a foundation that becomes exponentially more expensive and complex to fix as the business matures.
In today’s security landscape, there's a dangerous misconception: that being compliant automatically means being secure. While compliance frameworks like ISO 27001, SOC 2, HIPAA, and PCI-DSS are essential for establishing governance and trust, they are only a starting point, not the destination. Many organizations, however, treat them as a finish line.
Statistics show that 80% of companies follow a reactive, checklist-driven approach to security. They race to pass audits, collect certificates, and mark off controls believing that once the paperwork is in order, their systems are secure. However, this leads to a misleading sense of security. Real-world attackers don’t check whether your ISO binder is up-to-date they look for the gaps that paperwork doesn’t catch: untested incident response plans, misconfigured IAM roles, outdated software, and unaware employees.
These organizations often delay or completely overlook critical activities such as:
Regular vulnerability assessments and penetration testing (VAPT)
Drills and testing of incident response plans
Continuous monitoring of infrastructure and cloud environments
Tight IAM controls and privilege management
This “minimum effort for maximum compliance” mindset leads to vulnerabilities festering undetected until a breach occurs.
In contrast, the remaining 20% of organizations adopt a proactive and risk-centric approach. They don’t just do SOC 2 or VAPT once a year they embed these practices into their operations. For them:
Security is an ongoing process, not an annual audit.
VAPT and threat modelling are regular activities, not reactive obligations.
Internal audits and red team exercises are conducted in-house to complement third-party assessments.
Security is aligned with business goals, ensuring long-term resilience not just short-term compliance.
These companies understand that compliance can help validate good security practices, but it should never replace them. True security is dynamic, evolving with threats not locked in checkboxes.
Today’s Chief Information Security Officers (CISOs) operate in one of the most high-pressure executive roles constantly juggling business alignment, evolving threats, and stretched resources. They’re expected to speak the language of the boardroom while simultaneously defending the organization in the trenches of cyber warfare. But this dual responsibility creates persistent dilemmas that don’t have easy answers.
Dilemma 1: Balancing Budget vs. Threat Coverage
CISOs are often asked to “do more with less.” Security leaders know what’s needed to protect the organization advanced detection, zero-trust architectures, dedicated monitoring but often face budget constraints from leadership who see security as a cost center.
"I know we need 24/7 SOC coverage, but with our budget, I’m barely covering working hours."
This dilemma forces security teams to prioritize risks and sometimes accept known gaps, making difficult trade-offs between critical coverage and available resources.
Dilemma 2: Meeting Compliance vs. Building Resilience
Boards frequently push CISOs to “get the certification” to unlock new customers or markets. While certifications like SOC 2 and ISO 27001 are important, compliance does not equal resilience. CISOs must decide how much to invest in passing audits versus building real operational defense capabilities like threat hunting, purple teaming, or incident simulations.
The risk? Organizations may appear secure on paper but fall apart under real-world attack scenarios.
Dilemma 3: Investing in Tools vs. Training People
The cybersecurity market is flooded with tools promising silver-bullet solutions. Boards are eager to invest in platforms that promise ROI but security is ultimately a people problem. CISOs struggle with whether to:
Buy yet another tool to automate detection, or
Invest in training employees, building internal security champions, and enhancing awareness.
Without the right skills, even the best tools are underutilized or misconfigured adding more complexity without more coverage.
The Hidden Cost: Side Effects of CISO Dilemmas
When these dilemmas go unresolved, two major side effects emerge:
Team Burnout
Security teams are constantly firefighting. Endless alerts, a lean headcount, and the emotional toll of always being "on call" lead to burnout, attrition, and mistakes. Fatigued teams struggle to innovate or think long-term.
Gaps in Visibility
Fast-moving business units spin up new tools or environments without informing security resulting in shadow IT and unmanaged assets. Without full visibility, CISOs can’t protect what they don’t know exists.
CISOs walk a tightrope trying to protect the business while justifying every dollar, decision, and delay. They’re defenders, diplomats, and strategists all in one. The smartest ones know: Security is about prioritizing what matters most, not trying to protect everything equally.
Many organizations believe they are making solid progress in cybersecurity by investing in SOC, VAPT, and IAM but the reality often tells a different story. Security Operations Centers focus heavily on collecting logs, yet struggle with timely threat detection and response. Vulnerability testing is often limited to one-off, compliance-driven exercises that miss ongoing risks. Identity and Access Management, now the first line of defense, is frequently misconfigured, with users having more access than needed or even retaining access after leaving the company. Meanwhile, security awareness programs remain basic and uninspiring, leaving employees unprepared for real-world attacks. This imbalance creates a dangerous gap: companies are building walls, but leaving the doors wide open. A truly effective security strategy needs to be continuous, balanced, and people aware not just tool-driven.
For too long, security has been treated as an exercise in documentation something to prepare for audits, not adversaries.
But C-level leaders know the real risks don’t show up in compliance reports. They emerge in the blind spots: under-tested systems, misconfigured access, and employees unaware of the threats they face.
As this article has outlined, security maturity isn’t about how many frameworks you follow it’s about how well your people, processes, and technology can adapt under pressure. That means shifting focus:
True security doesn’t slow the business down it protects its ability to grow, adapt, and recover.
And that’s something frameworks can’t deliver on their own.
If your security program needs to move from checkbox-driven to capability-driven, let’s talk.
Contact us to align your security strategy with real-world risk and build a program that actually works when it matters most.
Share