Bjorn - The one plug network pentesting suite
Viren Punjabi
Sep 3, 2025
•
4 Min
Viren Punjabi
Sep 3, 2025
•
4 Min
TABLE OF CONTENTS
Share
Tamagotchi, a quite renowned toy from Japan that has inspired the idea for another pentesting tool. Remember Pwnagotchi, the device that uses AI helping penetrate any wireless network externally, Bjorn shines when you are already inside the network.
The device follows the same architectural design as pwnagotchi i.e. “Raspberry Pi Zero W/WH” as the brains topped with an e-ink display that has a gamified UI to know what the Viking is up to. The build is straight forward with no complex wiring required.
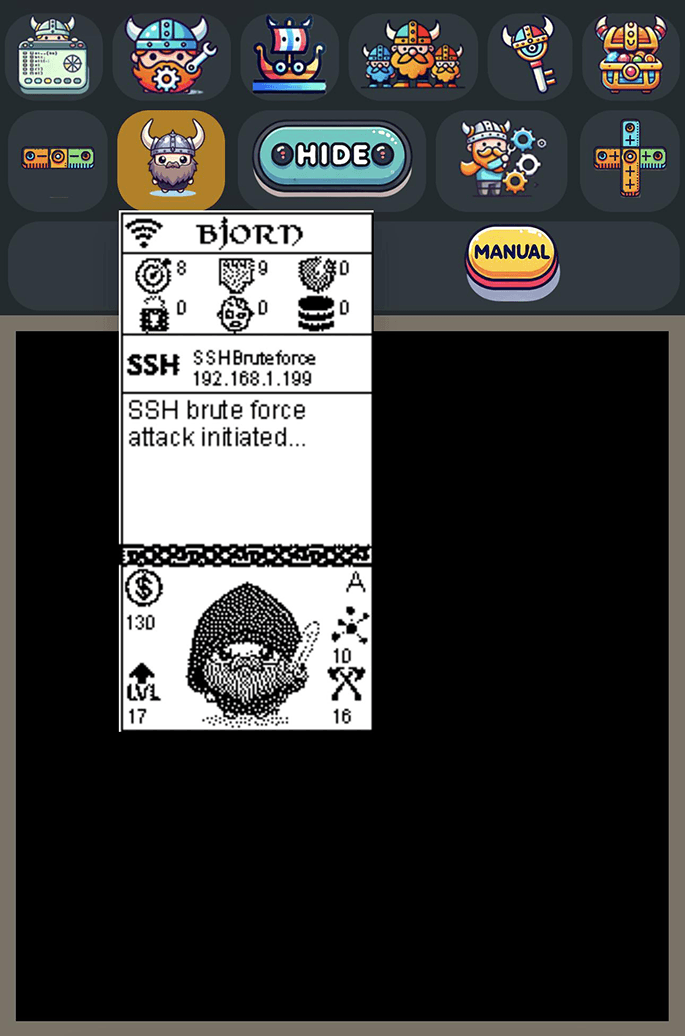
Do not make the mistake to underestimate the device by its form factor, it has Linux running inside and we know what a UNIX system when configured well with a nifty mindset can do.
Network Scanning: Identifies live hosts and open ports on the network.
Vulnerability Assessment: Performs vulnerability scans using Nmap and other tools.
System Attacks: Conducts brute-force attacks on various services (FTP, SSH, SMB, RDP, Telnet, SQL).
File Stealing: Extracts data from vulnerable services.
User Interface: Real-time display on the e-Paper HAT and web interface for monitoring and interaction.

It has some nice features but none of them seem that extraordinary, well the idea is to expand your security research and have a unique approach towards achieving the same goal of auditing a network as a typical pentester would do, firing Kali and running different scripts consecutively. The same can be achieved covertly making this implant-based device a perfect candidate for a stealthier approach.
Well talking about Linux in a box, Bjorn's arsenal can be highly customized by adding custom python scripts. The flavour is Raspi-OS with headless install, making resource consumption optimised just for these projects.
You can do different stuff with this device, and I mean good and educational, duh!
For starters, after building one plug it into your own network and perform a security audit testing for security issues. Take a note of what's going on and understand the way it performs all these different tests, you’ll be able to answer the what and the why and how, the questions worth researching for. You’ll find so many vulnerabilities hiding in plain sight.
Observe the results of a port scan, look for open ports and the services running on those ports. What if you had a couple of different servers hosted on the same network each have different data, well this can brute force services and even steal files showing you loose ends withing your network. You can also run custom nmap scripts to tailor the scan based on your requirements. Let’s say there are some CCTV cameras in your environment, the service scan might help you detect vulnerabilities directly for that camera or indirectly having an impact to that camera.
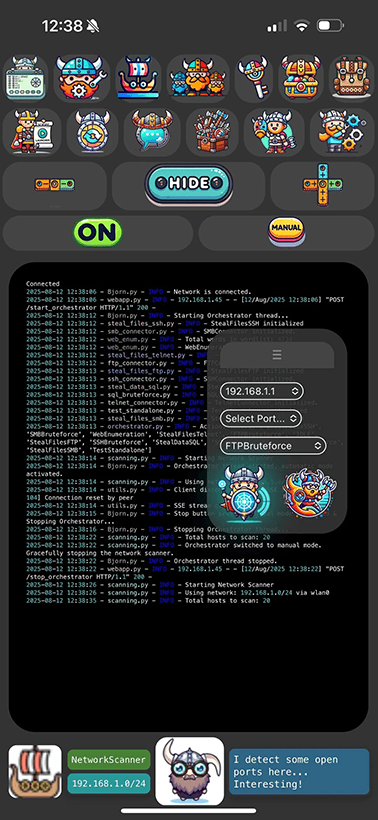
Once found a chunk of vulns, don’t stop there, understand what cause those vulns in the first place, how it’s impacting your network and what patches are required to mitigate those vulnerabilities.
You could also keep an eye on what devices are connected to your network, that’s a cool feature to have against intruders try to infiltrate and attack the network.
We have scratched the tip of iceberg; there’s lot more to this device than one might imagine.
This tool is great for beginners and those who seek interest in Linux CLI. You’ll make the system then break the system and then retry the whole thing multiple times learning something new skills and build different perspectives.
The Bjorn Project:
Share