Monitoring USB Drives in Windows using Wazuh
Harsh Radadiya
May 24, 2024
•
5 Min
Harsh Radadiya
May 24, 2024
•
5 Min
TABLE OF CONTENTS
Share
To monitor USB drives on a Windows system using Wazuh, you first install the Wazuh agent on your Windows computer. Then, you tweak its settings to catch events related to USB usage. Finally, you keep an eye on the data it gathers to make sure everything stays safe and follows the rules.
Monitoring USB drives is crucial for several reasons:
Audit PNP Activity is a Windows feature that facilitates the detection of USB drives and the generation of Plug and Play (PnP) events. Available on Windows 10, Windows Server 2016, and later versions, this feature is essential for monitoring hardware changes and USB device activity within these operating systems.
Perform the following steps to enable this feature:
Step 1 :
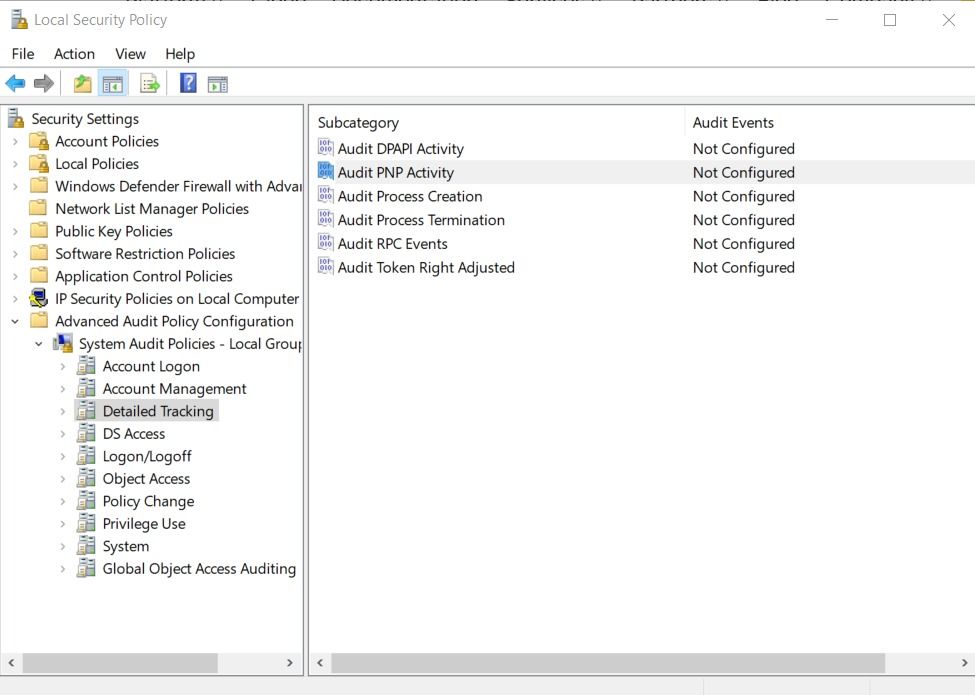
Press the Windows key + R to open the Run dialog box. In the input field, type secpol.msc and press Enter. This action will launch the Local Security Policy window, as illustrated below.
Step 2 :
Navigate to Advanced Audit Policy Configuration within the Local Group Policy Editor. Then go to System Audit Policies – Local Group Policy Object and find the Detailed Tracking section. Locate and double-click on Audit PNP Activity. In the window that appears, enable this policy by selecting Configure the following audit events: and then checking Success. Finally, click OK to apply the changes.
Add the following rule to the Wazuh server /var/ossec/etc/rules/testusb.xml file:
<group name="windows-usb-detect,">
<rule id="111000" level="7">
<if_sid>60103</if_sid>
<field name="win.system.eventID">^6416$</field>
<match>USBSTOR\\Disk</match>
<options>no_full_log</options>
<description>Windows: A PNP device $(win.eventdata.deviceDescription) was connected to $(win.system.computer)</description>
</rule>
</group>In Wazuh, Rule ID 111000 is specifically designed to detect events related to Windows Event ID 6416. This event is triggered when a Windows system identifies the connection of an external device, such as a USB drive, to the monitored Windows endpoint.
To refine the detection, the rule uses the <match> tag to filter for events containing the keyword USBSTOR\\Disk. This keyword includes detailed information about the USB device, such as the vendor name, product name, revision number, and serial number. By focusing on USBSTOR\\Disk, the rule effectively ignores other unrelated USB events, ensuring that only relevant USB drive connection events are captured and reported.
Step 2 :
Restart the Wazuh Manager to Apply Changes:
systemctl restart wazuh-managerPlug a USB device into the monitored Windows endpoint.
Explore the “Security Events” section within the Wazuh dashboard to view alerts triggered by USB drive insertions on your Windows endpoints. This section provides a comprehensive overview of security incidents, including alerts indicative of USB activity. By monitoring this tab, you can promptly identify and respond to any unauthorized or suspicious USB device connections within your network.
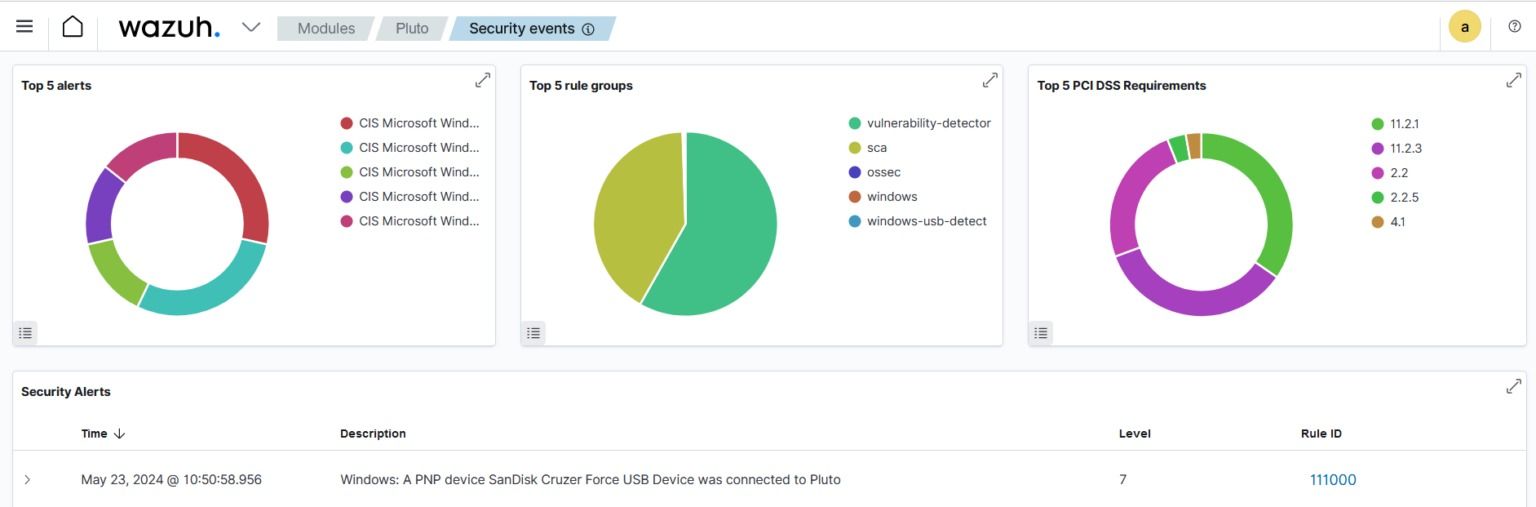
Perform the steps below to trigger alerts when authorized and unauthorized USB drives are inserted into the monitored Windows endpoint.
You must create a CDB (constant database) list of authorized USB drives using their deviceIdfields. We need a list of authorized devices for matching with detected drive activities. A drive not included on this list will be flagged as unauthorized.
Step 1 :
On the Wazuh dashboard, expand the rule ID 111000 alert and extract the value from the data.win.eventdata.deviceId field. This field contains the vendor name, product name, revision number, and serial number. The image below shows the deviceId extracted from the alert generated earlier.
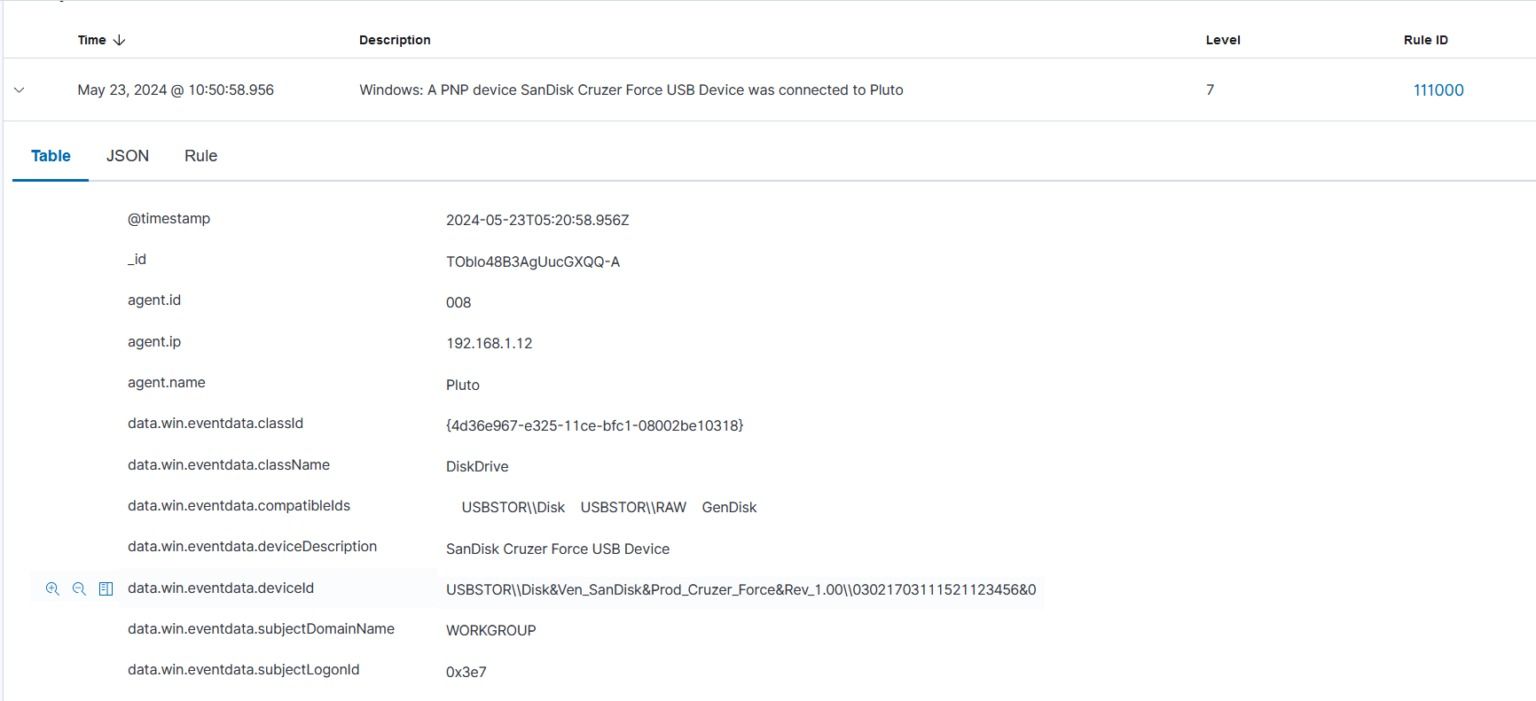
Step 2 :
On the Wazuh server, create a usb-drives CDB list in the /var/ossec/etc/lists directory:
sudo touch /var/ossec/etc/lists/usb-drivesStep 4 :
To include USB drive monitoring in Wazuh, add <list>etc/lists/usb-drives</list> within the <ruleset> section of /var/ossec/etc/ossec.conf. After restarting the Wazuh manager, this configuration enhancement will enable tracking USB drives effectively.
<ruleset>
<!-- Default ruleset -->
<decoder_dir>ruleset/decoders</decoder_dir>
<rule_dir>ruleset/rules</rule_dir>
<rule_exclude>0215-policy_rules.xml</rule_exclude>
<list>etc/lists/audit-keys</list>
<list>etc/lists/amazon/aws-eventnames</list>
<list>etc/lists/security-eventchannel</list>
<!-- User-defined ruleset -->
<decoder_dir>etc/decoders</decoder_dir>
<rule_dir>etc/rules</rule_dir>
<list>etc/lists/usb-drives</list>
</ruleset>Here, we introduce two rules aimed at identifying both authorized and unauthorized USB drives. Follow the outlined steps to seamlessly integrate these rules into your Wazuh server for enhanced USB drive monitoring capability.
Step 1 :
Add the following rules to the previously created windows-usb-detect group in the /var/ossec/etc/rules/testusb.xml file:
<rule id="111001" level="5">
<if_sid>111000</if_sid>
<options>no_full_log</options>
<description>Windows: Authorized PNP device $(win.eventdata.deviceDescription) was connected to $(win.system.computer).</description>
</rule>
<rule id="111002" level="8">
<if_sid>111000</if_sid>
<list field="win.eventdata.deviceId" lookup="not_match_key">etc/lists/usb-drives</list>
<options>no_full_log</options>
<description>Windows: Unauthorized PNP device $(win.eventdata.deviceDescription) was connected to $(win.system.computer).</description>
</rule>
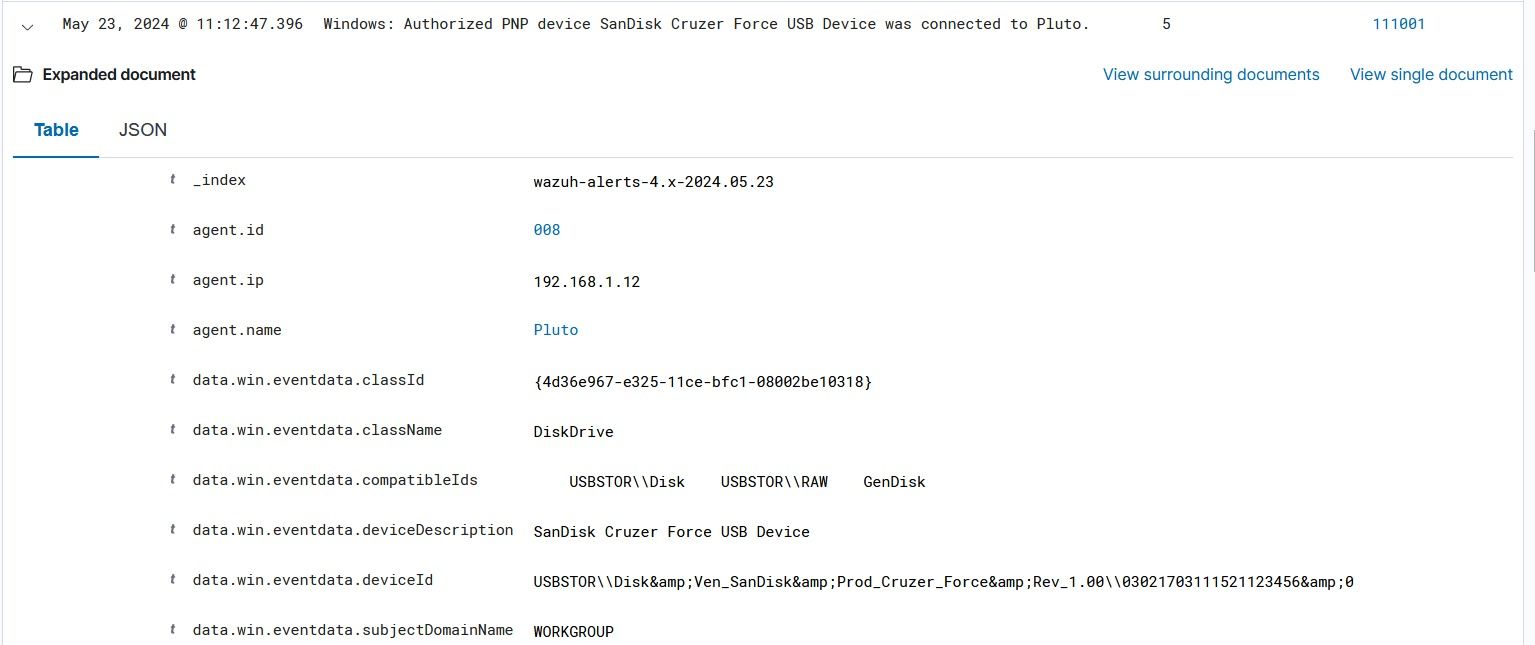
Rule ID 111001 triggers alerts for authorized USB drive insertions, while Rule ID 111002 generates alerts for unauthorized ones, indicating a mismatch in devised against the CDB list. These rules facilitate comprehensive monitoring of USB drive activity on endpoints.
Step 2 :
Restart the Wazuh manager for the changes to take effect.
systemctl restart wazuh-managerTo detect both authorized and unauthorized USB drives:
View the Security events on the Wazuh dashboard to observe generated alerts. Authorized USB events will be indicated differently from unauthorized ones, providing a clear visual distinction
Share
Get free guidance from certified experts or build tailored strategies with our team now.