How AI Is Rebuilding the SOC, One Stage at a Time
Mulayam Yadav
Apr 21, 2025
•
6 Min
Mulayam Yadav
Apr 21, 2025
•
6 Min
The traditional Security Operations Center (SOC) is no longer sustainable.
Faced with rising attack volumes, increasingly advanced threats, and growing talent shortages, today’s SOC leaders are confronting a harsh reality: the current model even with best-in-class SIEMs, SOAR platforms, and threat intel tools cannot scale fast enough to meet the pace of modern risk. Most organizations are still operating in a reactive mode, relying on manual investigations and static playbooks while adversaries leverage automation, obfuscation, and AI.
A new operating model is emerging — one where AI becomes a strategic partner in threat detection and response, not just a back-end enhancement. This insight outlines the evolution of the SOC through its critical transformation phases from log correlation and alert management to orchestration, and finally, to autonomous, intelligence-led operations. Most importantly, we break down how AI must be integrated in phases, just like building a mature human team: observation, collaboration, autonomy.
For CISOs, CTOs, and security leaders, this isn’t just a tech evolution — it’s a business-critical transformation. AI is not here to replace human analysts it’s here to amplify capabilities, increase agility, and redefine scale in cyber defense.
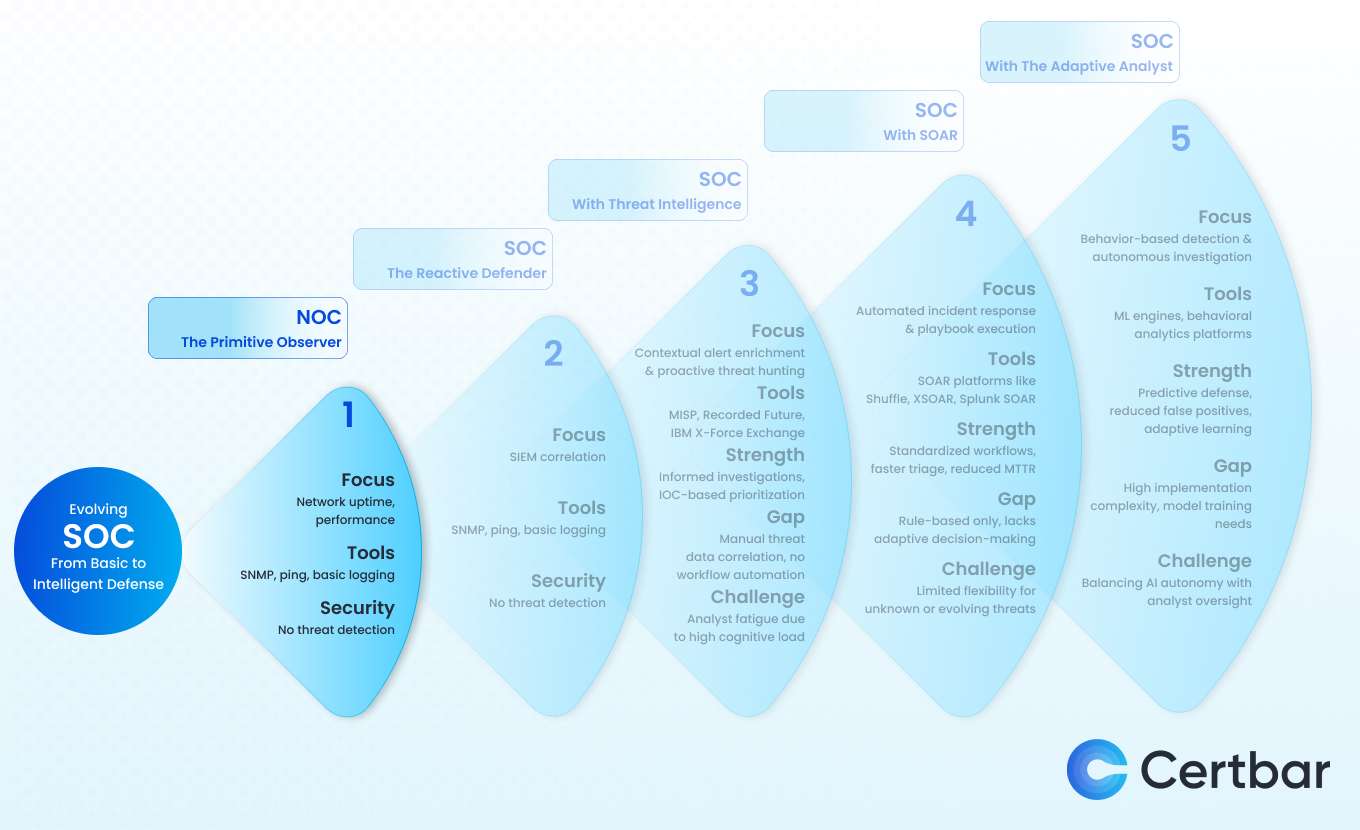
The Security Operations Center (SOC) has undergone a profound transformation evolving from basic network monitoring centers to complex ecosystems powered by threat intelligence, automation, and now artificial intelligence. Each stage in this evolution represents not just a technical upgrade, but a strategic response to new challenges in the threat landscape, data volume, and analyst fatigue.
The journey is not linear; it’s adaptive. SOCs have historically evolved because of operational necessity as new threats emerged and analyst capacity was stretched, new platforms were introduced to restore control and speed. This section outlines the five major stages of SOC evolution, visually captured below, and provides strategic context on what each phase achieved and where it fell short.
Before cybersecurity became a boardroom conversation, operational visibility meant one thing: uptime. Before cybersecurity took center stage, the NOC focused on maintaining availability and ensuring that networks ran smoothly without interruption.. Its focus was never security it was stability.
The objective was straightforward: maintain uptime, avoid outages, and address network slowdowns quickly. Metrics were centered around throughput, latency, and link failures not adversarial threats or breach containment. Security, if considered at all, was peripheral handled through firewalls or antivirus, and often siloed from operational workflows.
There was no concept of threat intelligence, lateral movement, or behavioral anomalies. Logs were collected, if at all, for audit purposes—not real-time correlation. Breaches were often discovered after damage was done, either through operational disruption or third-party disclosure. In many organizations, IT and security were not just separate teams they were separate mental models.
Strategic Focus:
Security Gaps:
For years, security teams have been collecting tools—SIEMs, SOARs, EDRs, TIPs all stacked, stitched, and scripted together in the hope that more technology would deliver better security. But more tools didn’t solve the problem. Faster attacks, smarter adversaries, and mounting alert volumes kept outpacing even the best-built stacks.
What’s needed now isn’t another integration or dashboard. It’s a leap forward. That leap is AI—not as a feature, but as a foundational upgrade to how security operations think, respond, and scale.
AI changes the very architecture of the SOC:
It’s not just automating what analysts do—it’s amplifying what they’re capable of. An AI-augmented SOC can correlate faster than a SIEM, contextualize better than a threat intel feed, and assist more flexibly than any static playbook.
But most importantly, AI restores what’s been lost in the complexity of modern SOCs: focus. Clarity. Confidence.
This is the upgrade security leaders have been waiting for—not more dashboards, but fewer decisions to second-guess. Not more data, but the right context at the right time. Not more headcount, but higher impact from every analyst on the team.
The future isn’t just tool-rich—it’s intelligence-first.
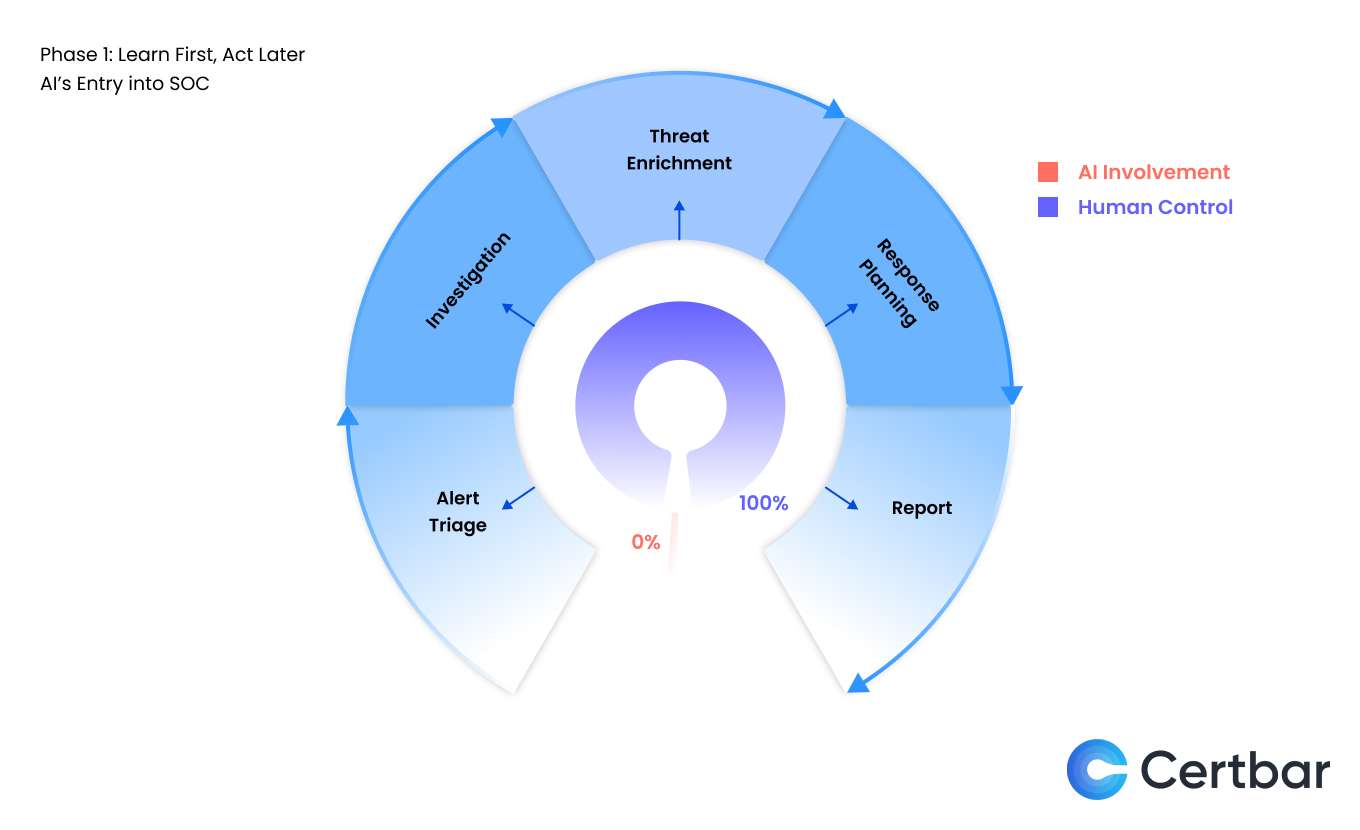
Integrating Artificial Intelligence into a Security Operations Center is not a single leap it’s a phased transformation. Think of AI as a new team member: it needs training, oversight, and phased exposure to critical tasks. This section outlines a strategic three-phase framework designed to help security leaders adopt AI in a structured and scalable way, without compromising trust or control.
In this foundational phase, AI doesn’t act — it watches.
The entire investigative process remains in human hands. Analysts own every step: triaging alerts, gathering context, validating hypotheses, planning responses, and writing reports. AI has 0% involvement in decision-making and 100% focus on learning.
This is where AI starts building its internal model—not from static rules or predefined logic, but by observing real-world investigations. It studies how analysts pivot through data, what signals they prioritize, and how they turn noise into insight. Every click, query, and conclusion becomes part of a deep learning loop.
Think of this as a junior analyst shadowing a seasoned investigator—not interfering, but absorbing the craft. This silent observation is critical: it ensures that when AI does step in later, it reflects the real behaviors, instincts, and workflows of the team it’s meant to support.
At this stage, AI is not a tool. It’s a student—and the analysts are the teachers.
As AI becomes more deeply embedded in the SOC, a familiar question echoes across boardrooms and security teams alike:
Will AI replace human analysts?
The short answer: no.
The strategic answer: It’s not about replacing people. It’s about unlocking potential..
The highest-performing SOCs aren’t the ones that automate everything. They’re the ones that strategically pair human judgment with machine precision. AI thrives in areas that demand scale, speed, and consistency log correlation, enrichment, and triage. But when it comes to context, ethics, or nuance, humans still lead.
Even in the most advanced SOCs, AI doesn’t make the final call it scopes the noise, enriches the signal, and hands analysts decision-ready context. In doing so, it removes 90% of the repetitive tasks that cause burnout and high turnover.
In this new model, analysts aren’t replaced they’re repositioned.
They move from alert clearers to strategic defenders. From reactive responders to proactive threat hunters. From fatigue to focus.
This shift isn’t just operational. It’s cultural.
It improves morale, increases retention, and creates a more sustainable, more satisfying SOC model one where AI handles the grind, and analysts focus on what only humans can do.
AI accelerates investigation. It reduces response time.
But most importantly, it ensures that humans are solving the highest-value problems not lost in low-value noise.
The evolution of the SOC is no longer about adding more tools it’s about designing a system that can think, learn, and scale alongside modern threats. As we’ve explored, traditional models built on SIEM, SOAR, and manual triage can no longer meet the speed, volume, or sophistication of today’s cyber risks. Artificial Intelligence represents not a feature enhancement, but a foundational shift in operational capability.
But adopting AI isn’t a binary leap it’s a phased transformation. From silent observation to collaborative investigation and, eventually, autonomous execution, AI must be introduced like any new analyst: trained gradually, guided responsibly, and trusted through performance. Organizations that get this right won’t just respond faster they’ll build more resilient, less fatigued, and more strategically focused security teams.
The future-ready SOC doesn’t ask us to choose between human and machine. It demands we orchestrate them. As AI takes on scale and speed, human analysts are freed to focus on what truly matters: proactive threat modeling, scenario planning, and critical thinking the skills that make cybersecurity a strategic advantage.
AI isn’t replacing the SOC it’s rebuilding it around what matters most: speed, clarity, and human intelligence.
As a leading cybersecurity provider, we are here to help you secure your organization and stay ahead of emerging threats. To learn more about how we can protect your business, contact us today.
Share
 Mulayam Yadav
Mulayam Yadav
 Harsh Radadiya
Harsh Radadiya
 Harsh Radadiya
Harsh RadadiyaAI reduces both significantly. Many organizations report 30–40% faster detection and response times after integrating AI into their workflows.