ModSecurity Meets Wazuh: A Secure Combo
Mulayam Yadav
Oct 5, 2024
•
6 Min
Mulayam Yadav
Oct 5, 2024
•
6 Min
TABLE OF CONTENTS
Share
Today, you'll learn how to use ModSecurity with Wazuh to strengthen your web server security. ModSecurity is a powerful tool that acts as a firewall for web servers like Apache, IIS, and Nginx. It helps block attacks such as SQL injections and cross-site scripting (XSS), keeping your site safe from common web threats. However, managing all of these security alerts can be overwhelming without the right monitoring system in place.
This is where Wazuh steps in. Wazuh works together with ModSecurity to give you an all-in-one security solution. While ModSecurity blocks dangerous traffic at the door, Wazuh helps you monitor, log, and respond to these security events in real time. Using Wazuh, you can track every potential threat that ModSecurity handles and get instant alerts with visual reports, making your security management simpler and more effective.
SQL injection is a common way hackers attack websites. In 2017, the Equifax data breach was caused by an SQL injection vulnerability, which exposed millions of users' data. With ModSecurity, this kind of attack can be stopped. The firewall scans incoming requests for harmful SQL code and blocks it before it can do any damage.
When you integrate ModSecurity with Wazuh, you not only block attacks but also monitor and analyze them. Wazuh can alert you when something suspicious happens, making it easier to protect your site.
ModSecurity is designed to protect against many of the most critical security risks identified in the OWASP Top 10, a list of the most common and dangerous web application vulnerabilities. For example, it can block SQL injections, where attackers try to manipulate databases through harmful SQL queries, and Cross-Site Scripting (XSS), where malicious scripts are injected into web pages. It also guards against Cross-Site Request Forgery (CSRF), preventing unauthorized actions on a user’s behalf, and protects against Security Misconfigurations, where vulnerabilities arise due to improperly configured systems. ModSecurity actively scans traffic for these and other OWASP-listed threats, blocking malicious requests before they can exploit your application, providing a robust defense for your web environment.
Integrating ModSecurity with Wazuh significantly boosts the security of your web application by offering real-time monitoring and alerts. In this guide, we’ll take you through the steps to set up this powerful combination.
Before you begin, ensure you have the following requirements in place:
Step 1: Access your terminal application on your server
Step 2: Before installing ModSecurity, it's a good idea to update your package lists to ensure you have the latest versions available. Run the following command:
sudo apt-get update
Step 3: If you are using Apache, run the following command to install ModSecurity:
sudo apt-get install libapache2-mod-security2
Step 4: Enable the ModSecurity module by executing the following command:
sudo a2enmod security2Step 5: To apply the changes, restart the Apache web server with the command below:
systemctl restart apache2Step 6: By default, ModSecurity only detects suspicious activity. To enhance security, we need to configure it to block malicious requests.
Step 7: We will copy the default ModSecurity configuration file to a new file. Run the command below:
sudo cp /etc/modsecurity/modsecurity.conf-recommended /etc/modsecurity/modsecurity.confStep 8: Next, open the configuration file in a text editor (like nano):
sudo nano /etc/modsecurity/modsecurity.confStep 9: Locate the line that says SecRuleEngine DetectionOnly and change it to SecRuleEngine On. This change enables ModSecurity to actively block malicious requests.
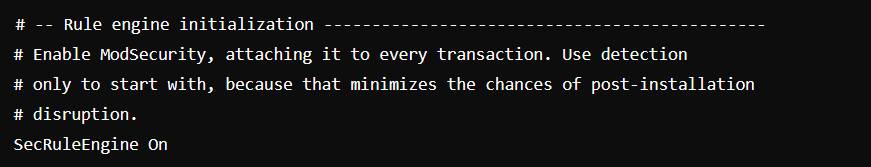
Step 10: To apply the configuration changes, restart the Apache server:
sudo systemctl restart apache2We have to install the Wazuh agent on the server where we have installed ModSecurity. Once the agent is in place, we can enhance the monitoring of ModSecurity logs by configuring it to send these logs to the Wazuh manager. By default, the Apache ModSecurity logs are stored in the Apache error log, which is found at /var/log/apache2/error.log. Follow the steps below to establish this configuration.
Step 1: Use the following command to open the Wazuh agent's configuration file in a text editor (such as nano):
sudo nano /var/ossec/etc/ossec.confStep 2: Find the <ossec_config> section in the configuration file and insert the following lines to enable log forwarding for the Apache error log:
<localfile>
<log_format>apache</log_format>
<location>/var/log/apache2/error.log</location>
</localfile>Step 3: To apply the changes made to the configuration file, restart the Wazuh agent with the following command:
sudo systemctl restart wazuh-agentTo ensure that everything is working correctly and to generate alerts on the dashboard, we will test the setup by performing a vulnerability scan against the web application using a command-line tool called Nikto.
Step 1: Nikto can be easily installed on Debian-based systems using the APT package manager. Open your terminal and run the following command:
sudo apt-get install nikto -y
Step 2: After successfully installing Nikto, you can run it to perform a scan on your web server. Use the following command, replacing <webserver_IP> with the actual IP address of your web server:
nikto -h <webserver_IP>Step 3: After running the Nikto scan, head over to the Wazuh dashboard. Select the agent corresponding to your web server, and you should now see the ModSecurity logs generated by the scan. These logs will display the alerts triggered by ModSecurity in response to the vulnerabilities detected during the scan.
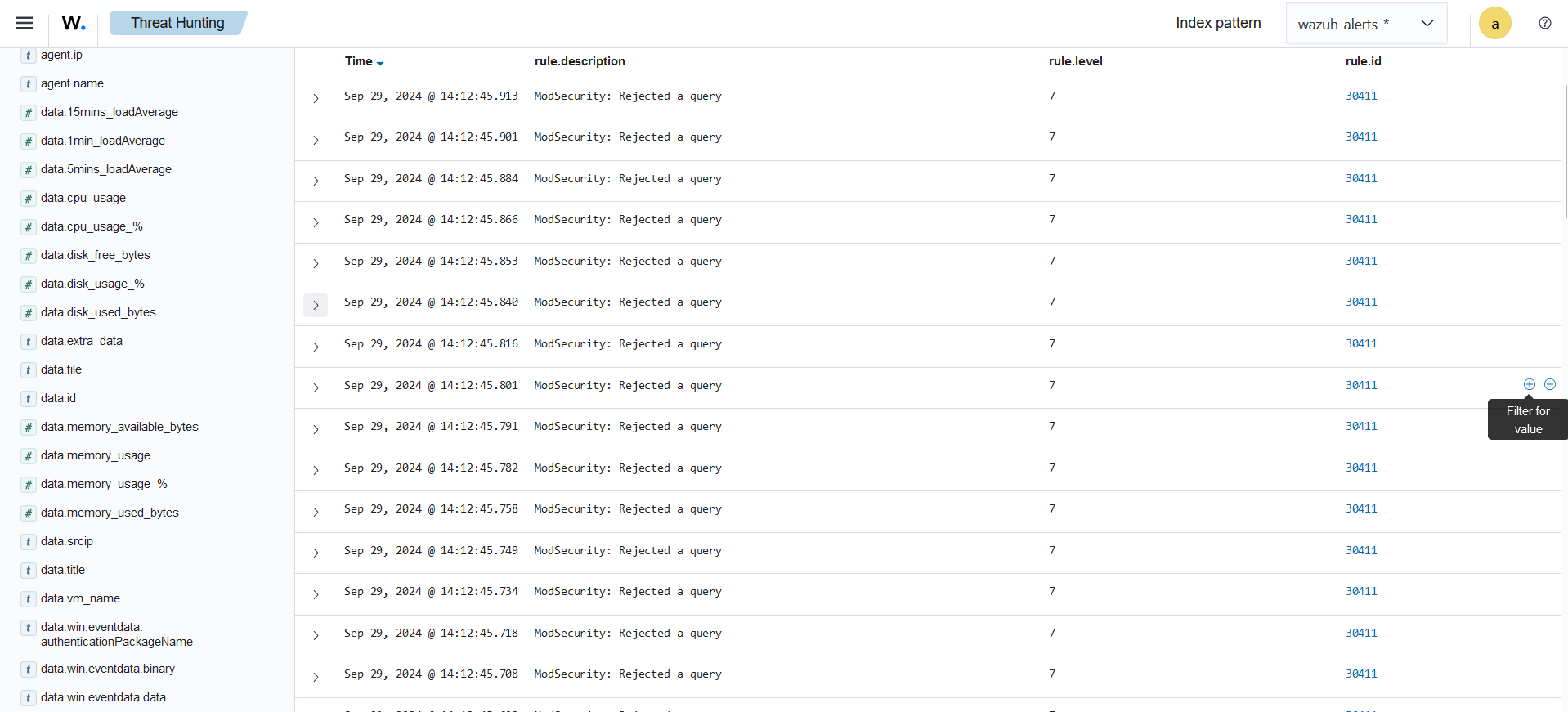
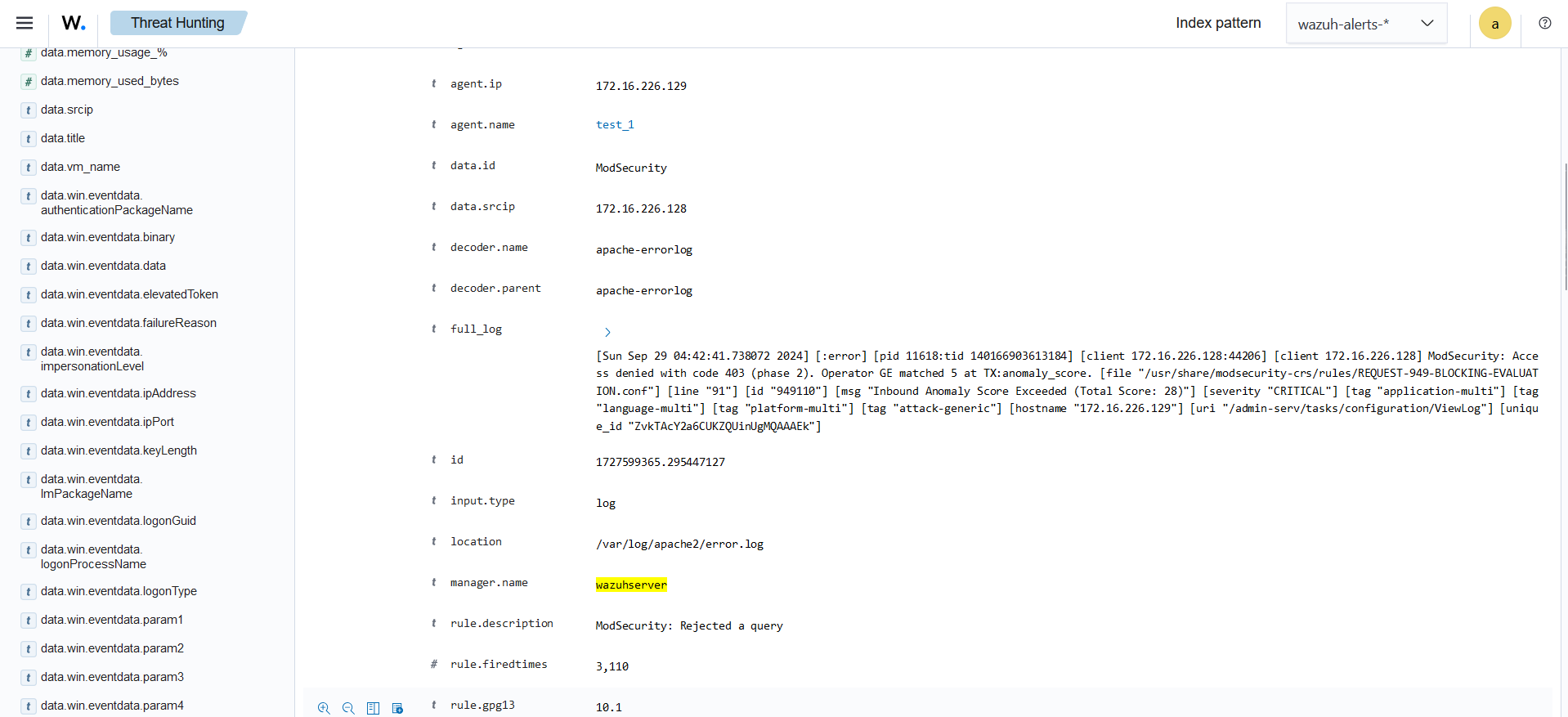
Integrating ModSecurity with Wazuh strengthens your web application security by offering real-time monitoring, alerting, and centralized logging. ModSecurity acts as a web application firewall, defending against threats like those in the OWASP Top 10. This guide helps you configure ModSecurity and Wazuh to detect, block, and visualize security events. Testing with Nikto validates the setup, ensuring vulnerabilities are addressed. Regular updates and proactive monitoring will keep your web environment secure against evolving threats.
Share

 Shreya Dhameliya
Shreya Dhameliya
 Shreya Dhameliya
Shreya Dhameliya
 Harsh Radadiya
Harsh Radadiya